What’s new in 8.16
editWhat’s new in 8.16
editHere are the highlights of what’s new and improved in Elastic Security. For detailed information about this release, check out our release notes.
Other versions: 8.15 | 8.14 | 8.13 | 8.12 | 8.11 | 8.10 | 8.9 | 8.8 | 8.7 | 8.6 | 8.5 | 8.4 | 8.3 | 8.2 | 8.1 | 8.0 | 7.17 | 7.16 | 7.15 | 7.14 | 7.13 | 7.12 | 7.11 | 7.10 | 7.9
Generative AI enhancements
editImproved Automatic Import capabilities
editAutomatic Import can now use a larger variety of large language models and accept larger log samples in a wider range of common formats.
Analyze more alerts with Attack Discovery
editAttack Discovery can now analyze up to 500 alerts at once, and provides higher-quality responses.

Customize Elastic AI Assistant using Knowledge Base
editElastic AI Assistant’s new Knowledge Base feature allows you to specify individual documents or entire indices that AI Assistant will remember and use as context. This improves the relevance, quality, and customization of its responses.

Entity Analytics enhancements
editManage persisted entity metadata with entity store
edit[preview] This functionality is in technical preview and may be changed or removed in a future release. Elastic will work to fix any issues, but features in technical preview are not subject to the support SLA of official GA features. The entity store feature allows you to query, reconcile, and maintain entity metadata from various sources, such as ingested logs, integrated identity providers, external asset repositories, and more. By extracting and storing entities from all indices in the Elastic Security default data view, the entity store lets you query entity metadata without real-time data searches.
After you enable the entity store, the Entity Analytics dashboard displays the Entities section, which offers a comprehensive view of all hosts and users in your environment. You can filter them by their source, entity risk level, and asset criticality level.

Asset criticality is available by default
editThe advanced setting for enabling asset criticality has been removed, and this feature is now available by default.
Run entity risk scoring in multiple spaces
editYou can now enable and run entity risk scoring in multiple Kibana spaces. This allows you to analyze and monitor entity risk in different contexts simultaneously.
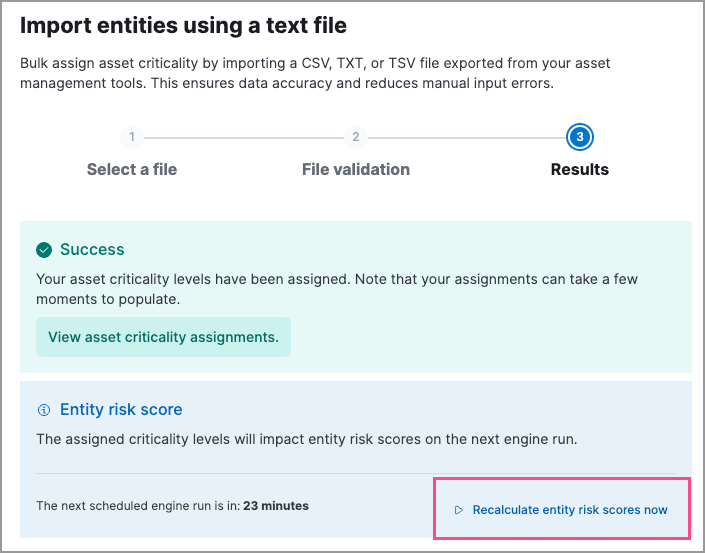
Recalculate entity risk scores after file upload
editWhen you bulk assign asset criticality using the file upload feature, the newly assigned criticality levels are automatically factored in during the next hourly risk scoring calculation. You can now manually trigger an immediate recalculation of entity risk scores by clicking Recalculate entity risk scores now during the file upload process.
Detection rules and alerts enhancements
editEnable prebuilt detection rules on installation
editPreviously, installing and enabling prebuilt rules took two steps. You can now do both in one step with the Install and enable option. This works for both single and multiple rules.

Run rules manually
editManually run rules for testing purposes or additional rule coverage. Details about manual runs (such as the status of each run, the total number of runs that will occur, and more) are shown on the Execution results tab of the rule details page.

Exclude cold and frozen data from rules
editRules that query cold and frozen data tiers might perform more slowly or fail. To ensure that the rules in your Kibana space exclude query results from cold and frozen tiers when executing, configure the excludedDataTiersForRuleExecution advanced setting.
View Elasticsearch queries that run during rule execution
editWhen previewing a rule, you can also learn about its Elasticsearch queries, which are submitted when the rule runs. This information can help you identify and troubleshoot potential rule issues. You can also use it to confirm that your rule is retrieving the expected data. This option is provided for ES|QL and EQL rules only.
Alert suppression is generally available for more rule types
editAlert suppression is generally available for the indicator match, threshold, machine learning, ES|QL, and new terms rule types. It is still in technical preview for event correlation rules.
Investigations enhancements
editAdd notes to alerts, events, and Timelines
editYou can now attach notes to alerts, events, and Timelines, and manage them from the Notes page. This provides an easy way to incorporate notes into your investigative workflows to coordinate responses, conduct threat hunting, and share investigative findings.

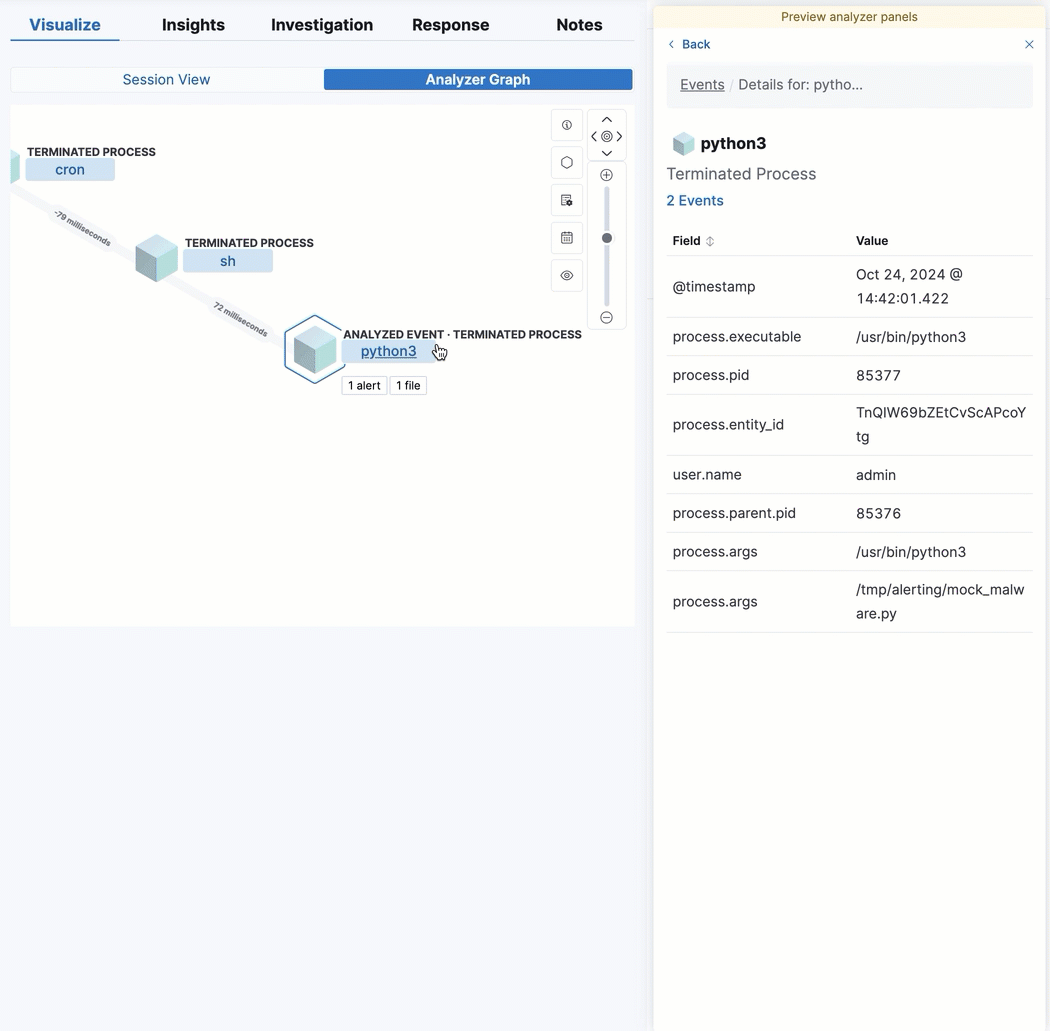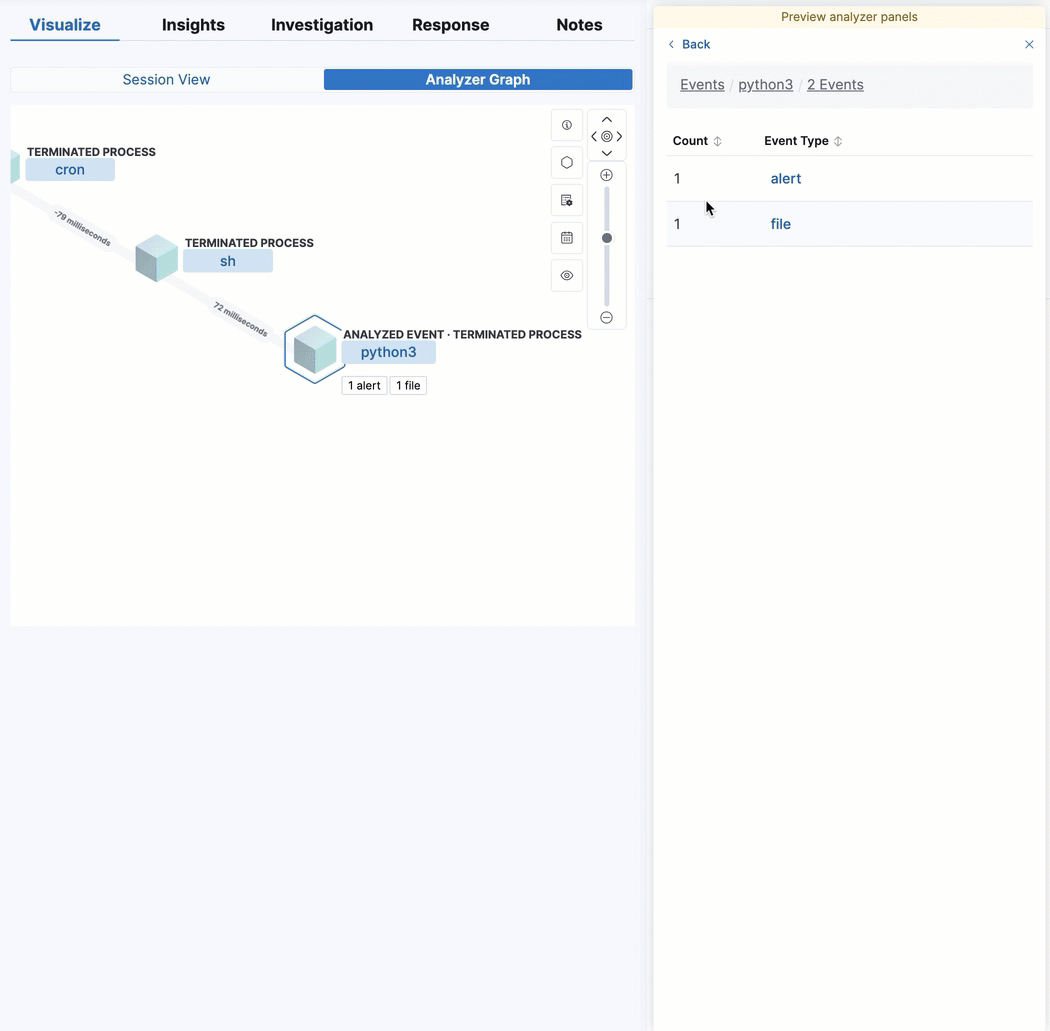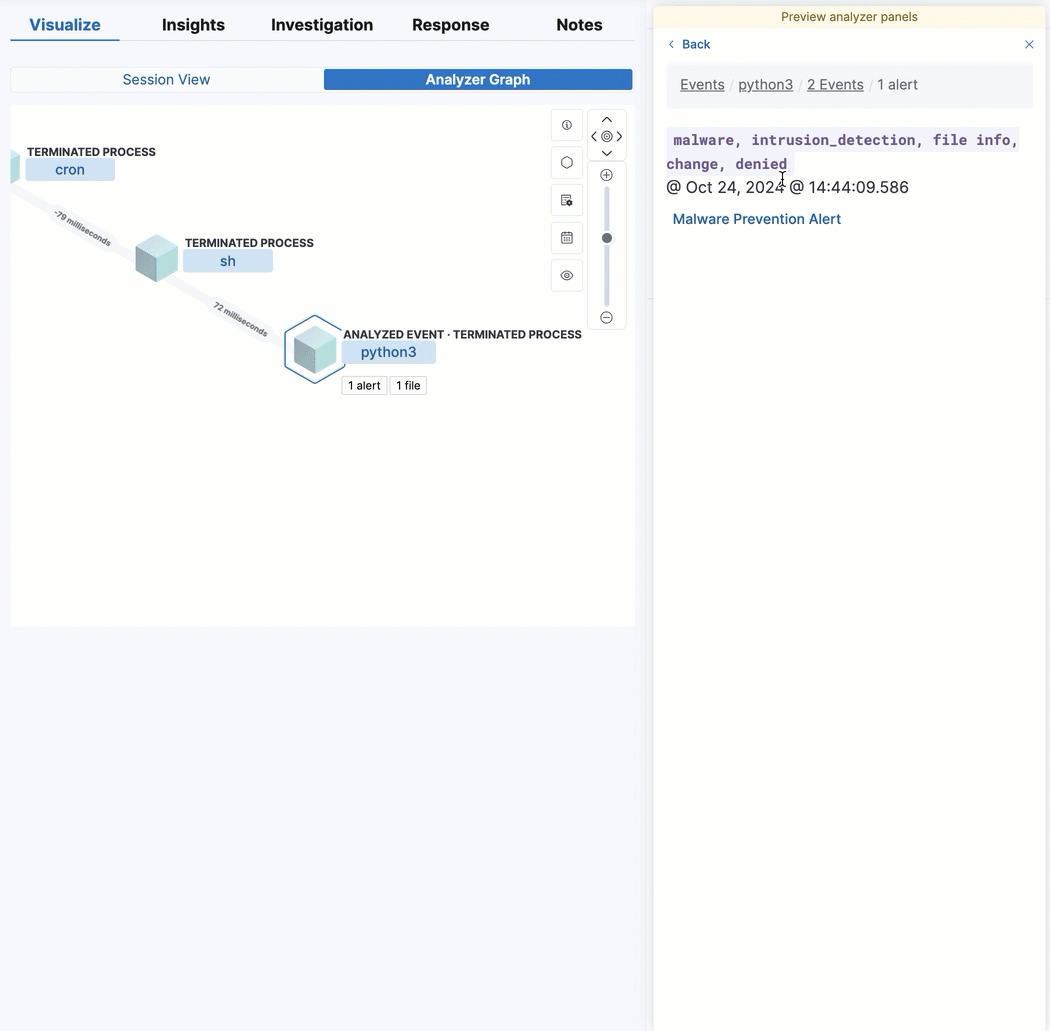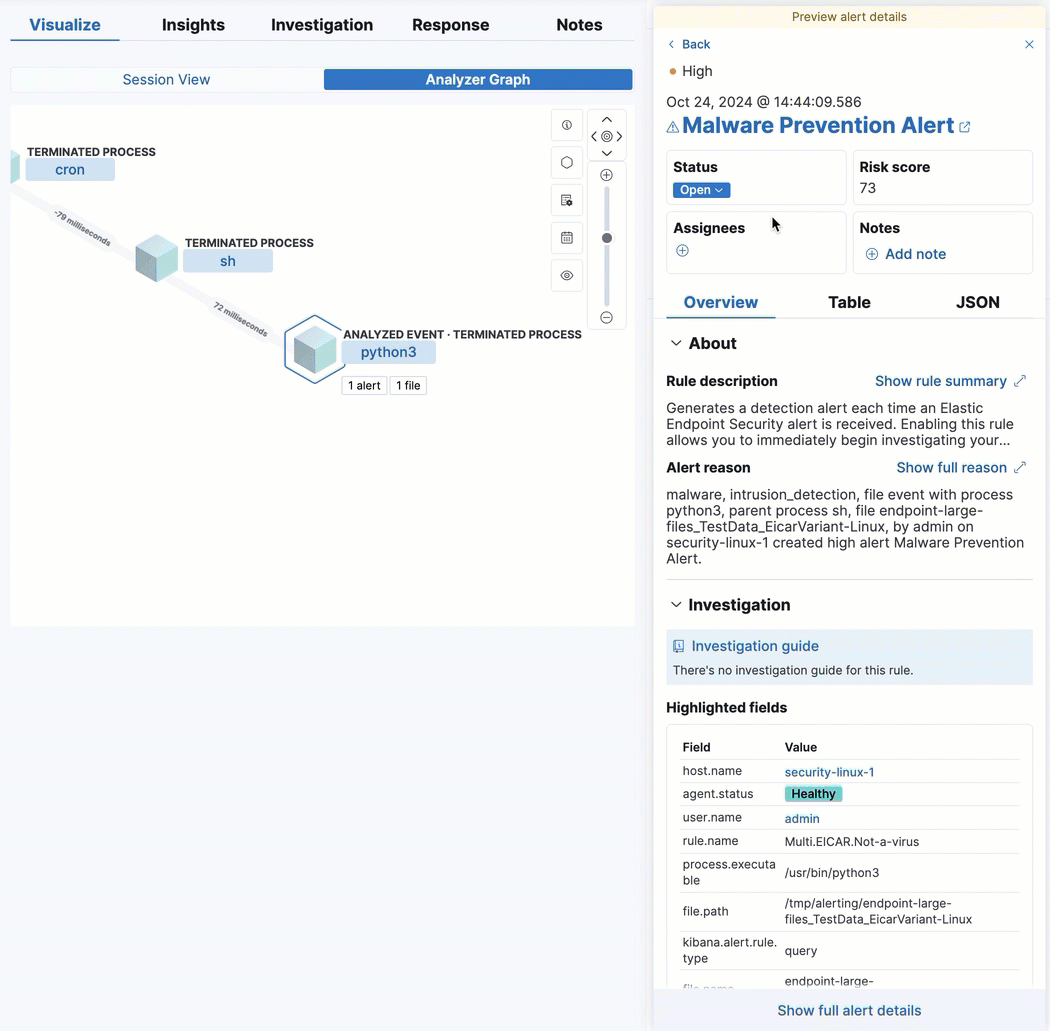
View analyzed events from the alert details flyout
edit
[preview]
This functionality is in technical preview and may be changed or removed in a future release. Elastic will work to fix any issues, but features in technical preview are not subject to the support SLA of official GA features.
By enabling the new securitySolution:enableVisualizationsInFlyout advanced setting, you can view analyzed alerts and events in the Visualize tab of the alert details flyout. This allows you to maintain the context of the Alerts table during your investigation and provides an easy way to preview related alerts and events.
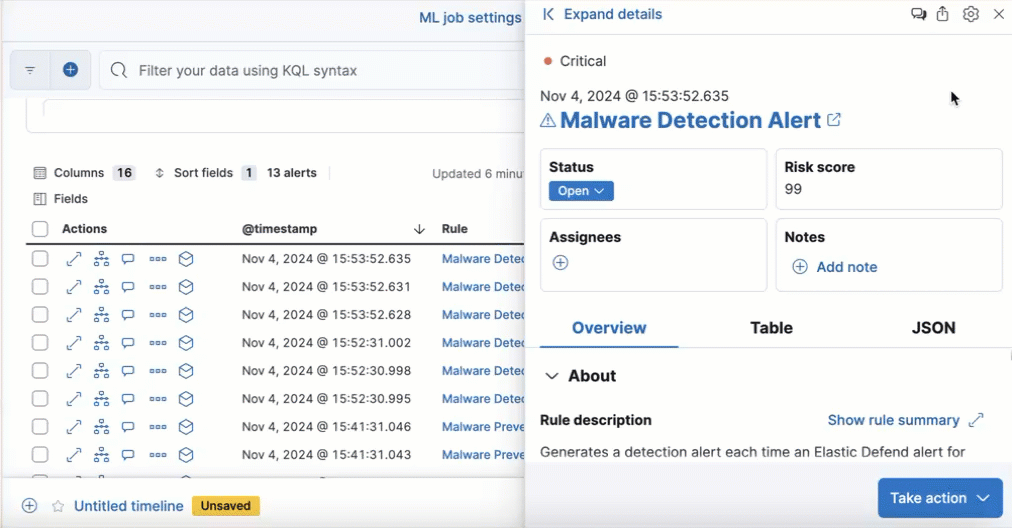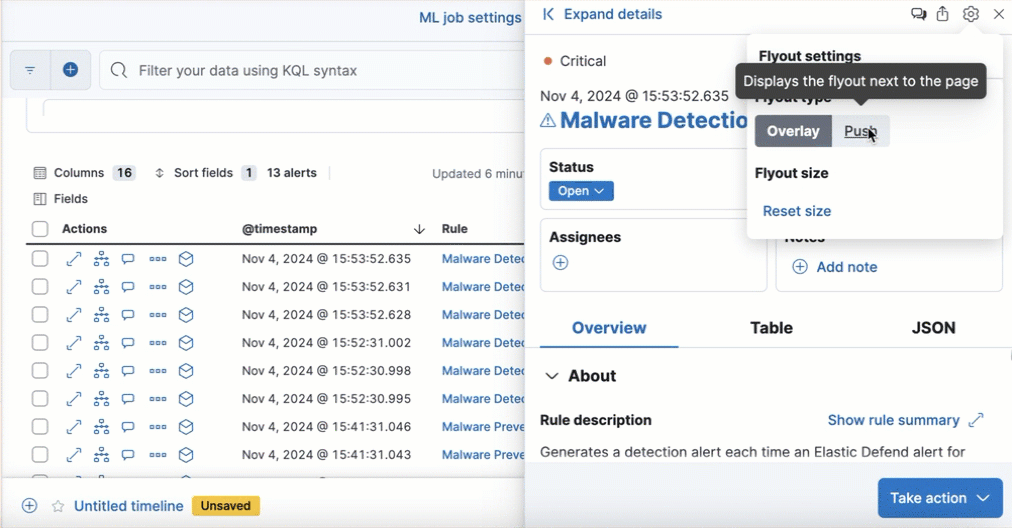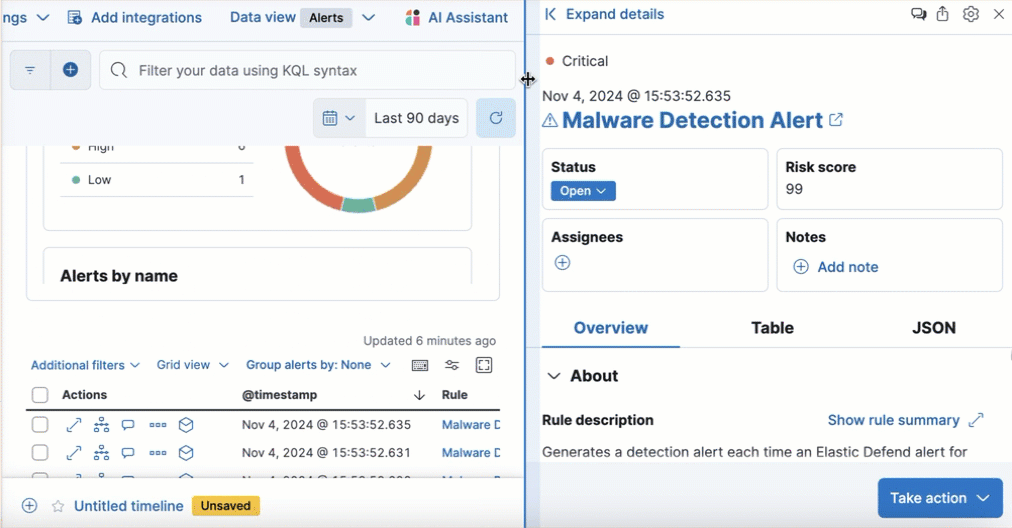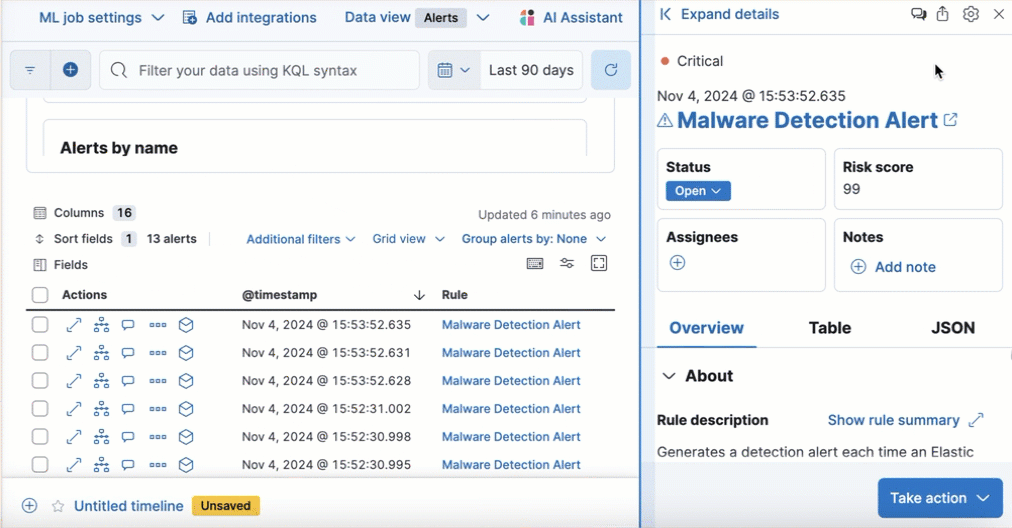
Resize alert and event details flyouts
editYou can now resize the alert and event details flyouts and choose how they’re displayed—over the Alerts table or next to it.
Elastic Defend and response actions enhancements
editMore SentinelOne third-party response actions
editAdditional third-party response actions are available using Elastic’s SentinelOne integration and connector:
- Get processes
- Terminate a process
Elastic Defend’s automated response actions support all rule types
editYou can now configure any detection rule type to perform Elastic Defend’s automated response actions.
Cloud Security enhancements
editIngest third-party cloud security data
editYou can now ingest cloud security data from several third-party sources—Falco, AWS Security Hub, and Wiz—into Elastic Security. The data appears on the Alerts and Findings pages, and in the user and host details flyouts.

Simplify posture data collection with agentless Cloud Security Posture Management deployment
editElastic’s native Cloud Security Posture Management (CSPM) integration now supports agentless deployment, giving you an easier and more streamlined way to collect posture data from your cloud service providers.