What’s new in 8.9
editWhat’s new in 8.9
editHere are the highlights of what’s new and improved in Elastic Security. For detailed information about this release, check out the Release notes.
Other versions: 8.8 | 8.7 | 8.6 | 8.5 | 8.4 | 8.3 | 8.2 | 8.1 | 8.0 | 7.17 | 7.16 | 7.15 | 7.14 | 7.13 | 7.12 | 7.11 | 7.10 | 7.9
Elastic AI Assistant enhancements
editThe Elastic AI Assistant now has a centralized UI for configuring settings, and you can now anonymize data sent to and from the AI provider.

Additionally, the new Generative AI token usage dashboard allows you to monitor your token usage with the AI provider.
Detect network intrusions and compromised hosts with Lateral movement detection
editLateral movement detection is a new, preventative advanced analytics package that detects anomalies from intrusions, file transfer, and Remote Desktop Protocol (RDP) events, which indicate lateral movement. To download and configure this package, follow the instructions here.
This feature requires a Platinum or Enterprise subscription.

Detection rules enhancements
editNew UI for installing and upgrading prebuilt detection rules
editThere’s a newly redesigned UI and workflow for managing prebuilt detection rules to allow more flexibility and visibility into rule updates. You can now select which prebuilt rules you want to install and update, instead of only installing the entire set of rules. You can also duplicate a rule to make changes to it.
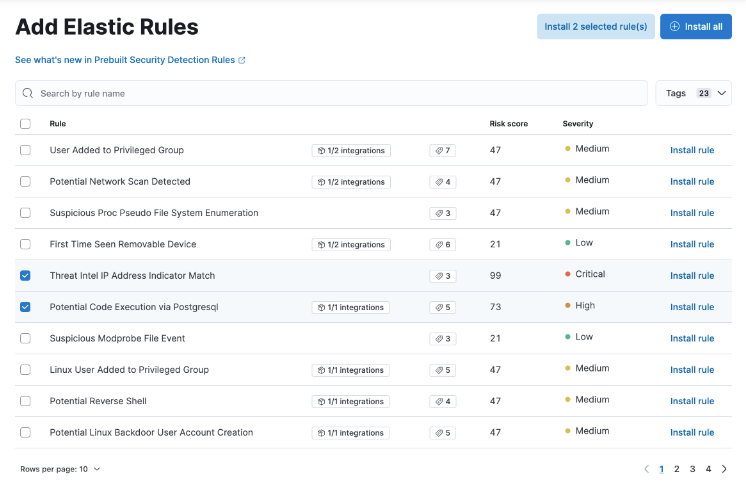
In addition, prebuilt detection rules have new tags to categorize your rules, such as the rule’s purpose, detection method, associated resources, and other information.
Monitor rule performance with the new Detection rule monitoring dashboard
editThe Detection rule monitoring dashboard provides visualizations to help you monitor the overall health and performance of Elastic Security’s detection rules. Review this dashboard for a high-level overview to determine if your rules are running successfully and how long they’re taking to run, search data, and create alerts.

Automated endpoint response actions for rules
editYou can now add the host isolation response action to rules. When rule conditions are met, the endpoint is automatically isolated.
Rule exceptions auto-populated with alert data
editNow, when you create a new rule exception from an alert, exception conditions are auto-populated with relevant alert data. A comment describing this action is also automatically added to the Add comments section.
Interactive investigation guides are now generally available
editInteractive investigation guides, which suggest steps for triaging, analyzing, and responding to potential security issues, are now generally available. You can configure an interactive investigation guide when you create a new rule or edit an existing one.

Prebuilt rule updates
editCheck out the latest updates to prebuilt rules. To download the latest updates, refer to Update Elastic prebuilt rules.
Manage and filter alert tags
editAlert tags, which you can add or remove for individual or multiple alerts, allow you to organize related alerts into categories that you can filter and group. If desired, you can also create custom tags by updating the feature’s advanced setting.

New integrations
editThe following security integrations were added in 8.9:
- Arista Firewall
- Google Security Command Center
- Microsoft Defender for Cloud
- Okta (Entity Analytics)
- SentinelOne Cloud Funnel
- Zero Networks

Upload files to an endpoint with new upload response action
editThe response console’s new upload response action allows you to upload a file to an endpoint enrolled with Elastic Defend. You can combine this with the execute response action to upload and run scripts, or perform other mitigation on remote hosts.
Cloud Security enhancements
editNew CloudFormation deployment for Cloud Security Posture Management (CSPM)
editThe CloudFormation deployment for CSPM provides a new, simpler deployment method for Cloud Security Posture Management, which you can use to monitor the security posture of your cloud assets. You can quickly set up this feature using AWS CloudFormation.
Discover vulnerabilities with the new Cloud Native Vulnerability Management dashboard
editThe Cloud Native Vulnerability Management (CNVM) dashboard gives you an overview of vulnerabilities detected in your cloud infrastructure.

Cases enhancements
editThe following enhancements have been added to Cases:
- You now have the option to specify a category for new and existing cases.
- You can now add Lens visualizations to cases from anywhere within the Elastic Security app.
- The case details Alerts tab now displays the number of alerts attached to a case.
- Email notifications now follow a new and improved template.