What’s new in 8.2
editWhat’s new in 8.2
editHere are the highlights of what’s new and improved in Elastic Security. For detailed information about this release, check out the Release notes.
Other versions: 8.1 | 8.0 | 7.17 | 7.16 | 7.15 | 7.14 | 7.13 | 7.12 | 7.11 | 7.10 | 7.9
New landing pages added to the left navigation menu
editSeveral new landing pages were added to the navigation menu in 8.2:
The Getting started page provides guidance on adding data to your environment. When new users install Elastic Security, this page is now the default view.
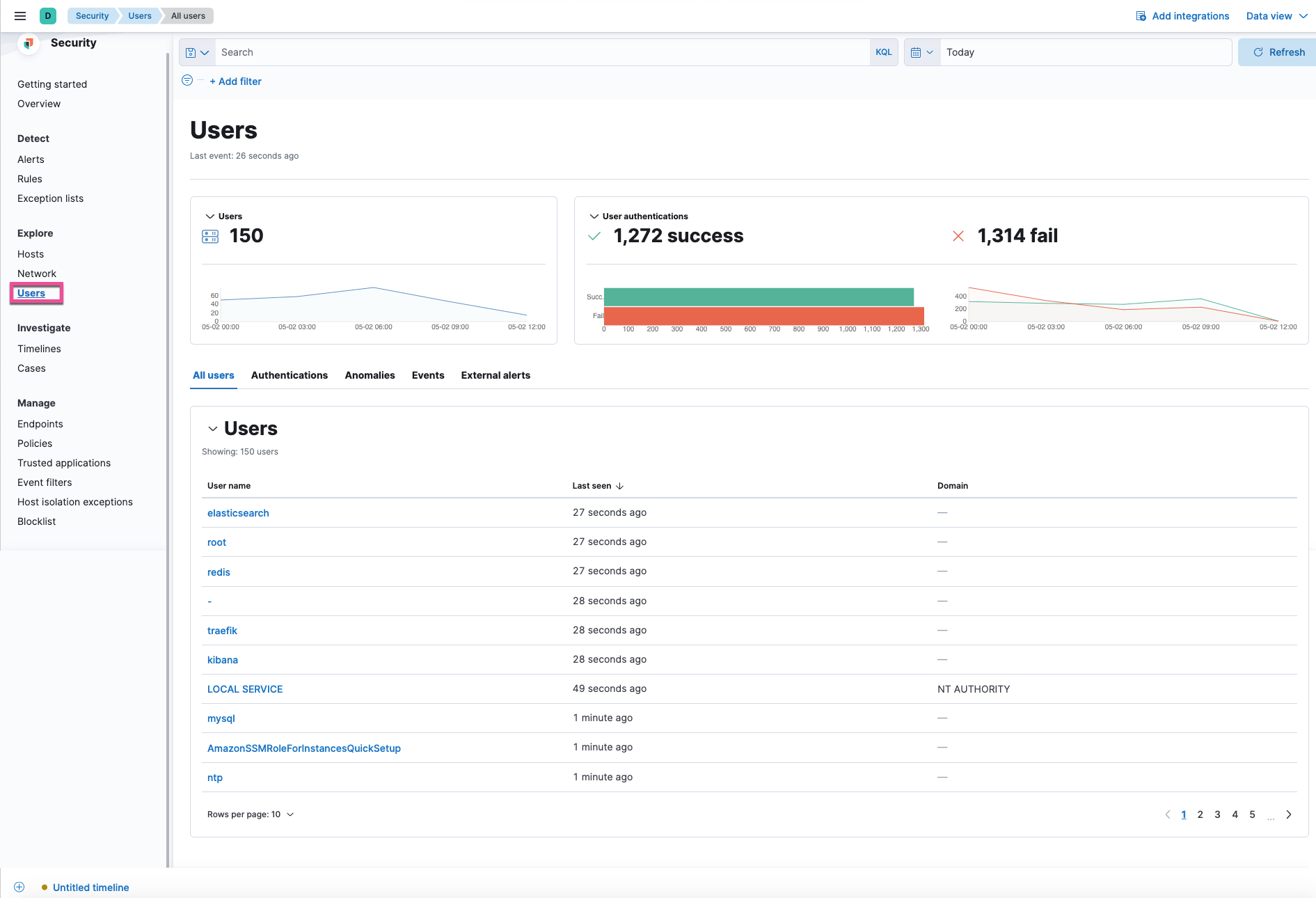
The Users page provides an overview of user data to help you understand authentication and user behavior.
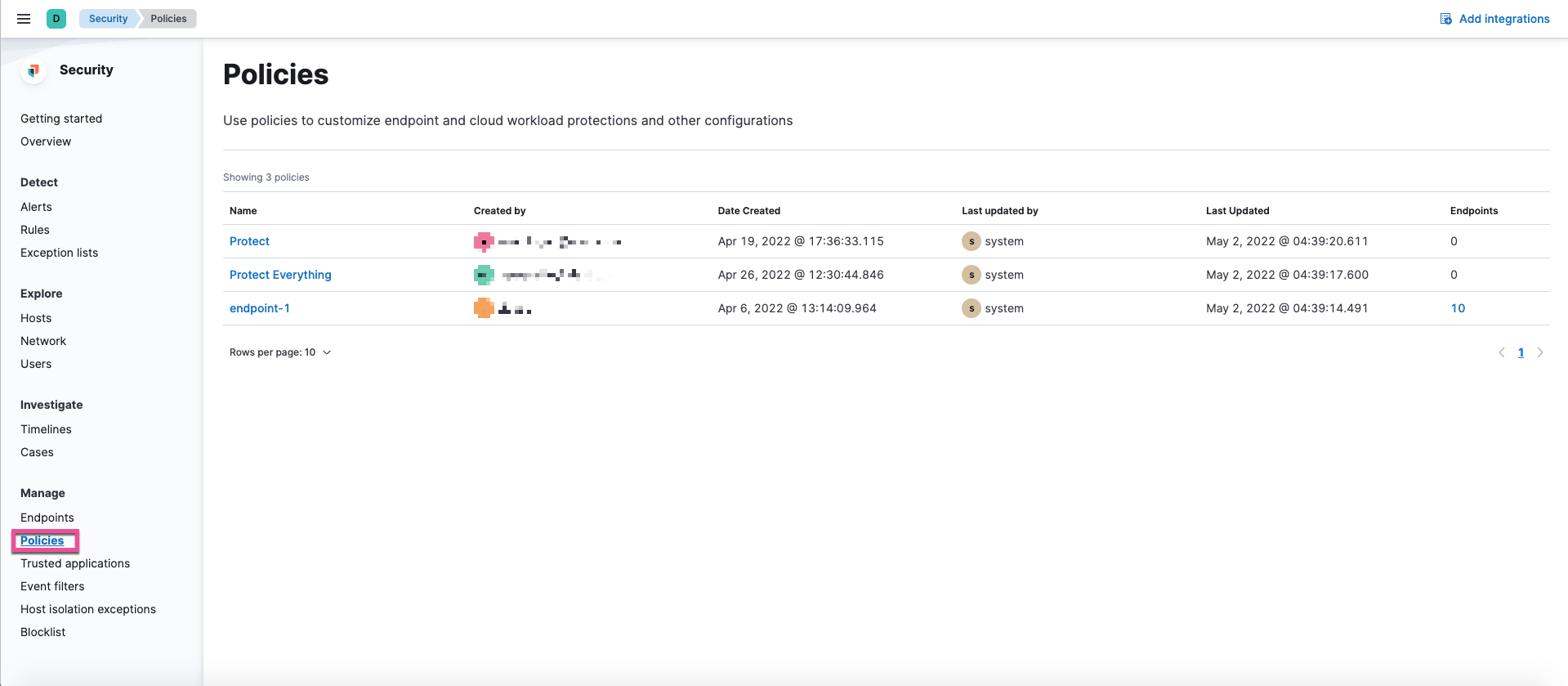
The Policies page allows you to view and manage your Endpoint Security integration policies from a single location.
The Blocklist page allows you to view, add, and manage the blocklist - a list of specified applications that are blocked from running on hosts. You can also use the blocklist API to manage blocked applications.
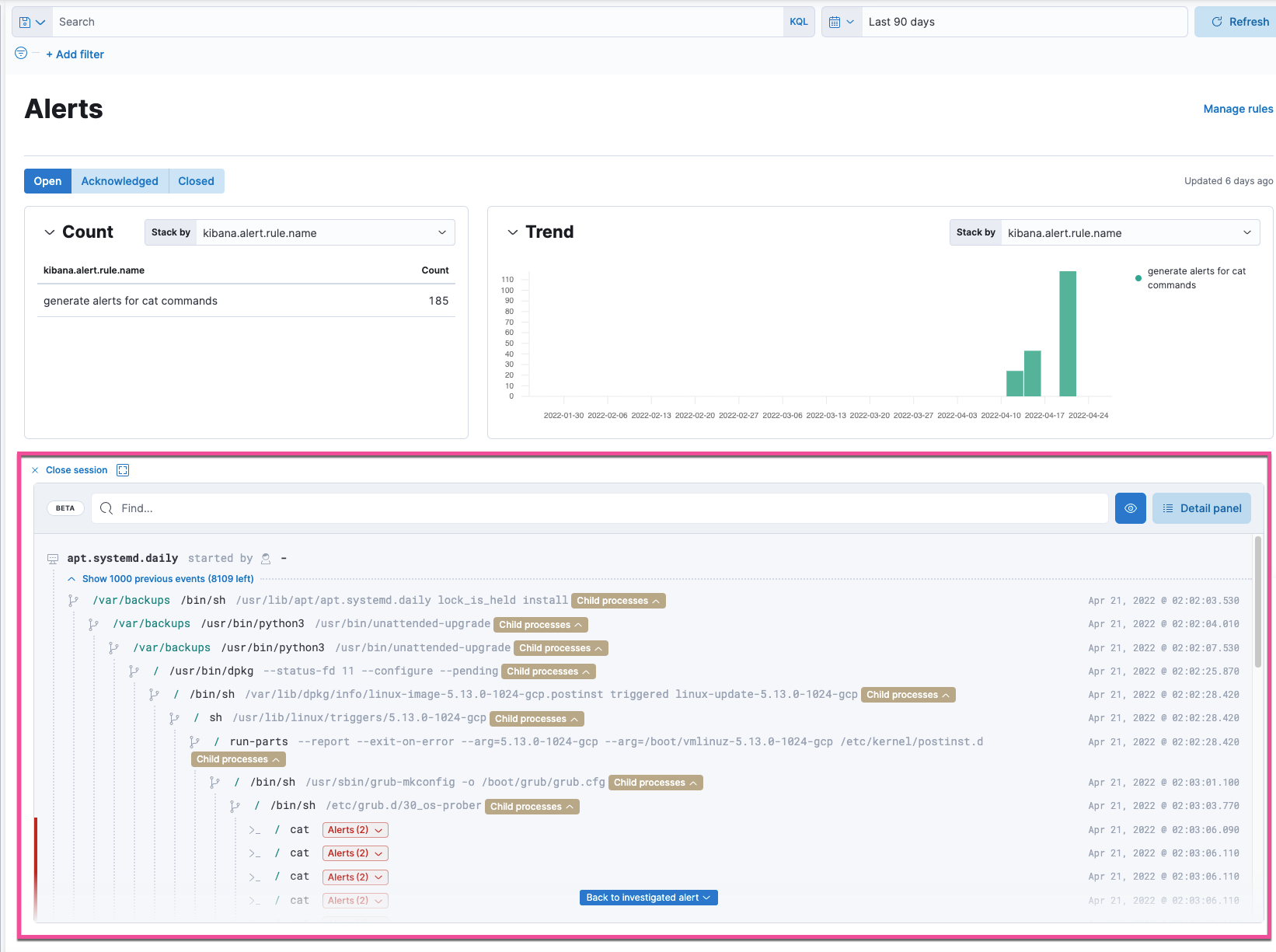
Session View tool shows Linux process executions (beta)
editSession View is a new tool that shows detailed information about Linux process executions in a chronological and hierarchal context. Use Session View to investigate alerts, user activity, and sessions on your Linux infrastructure.
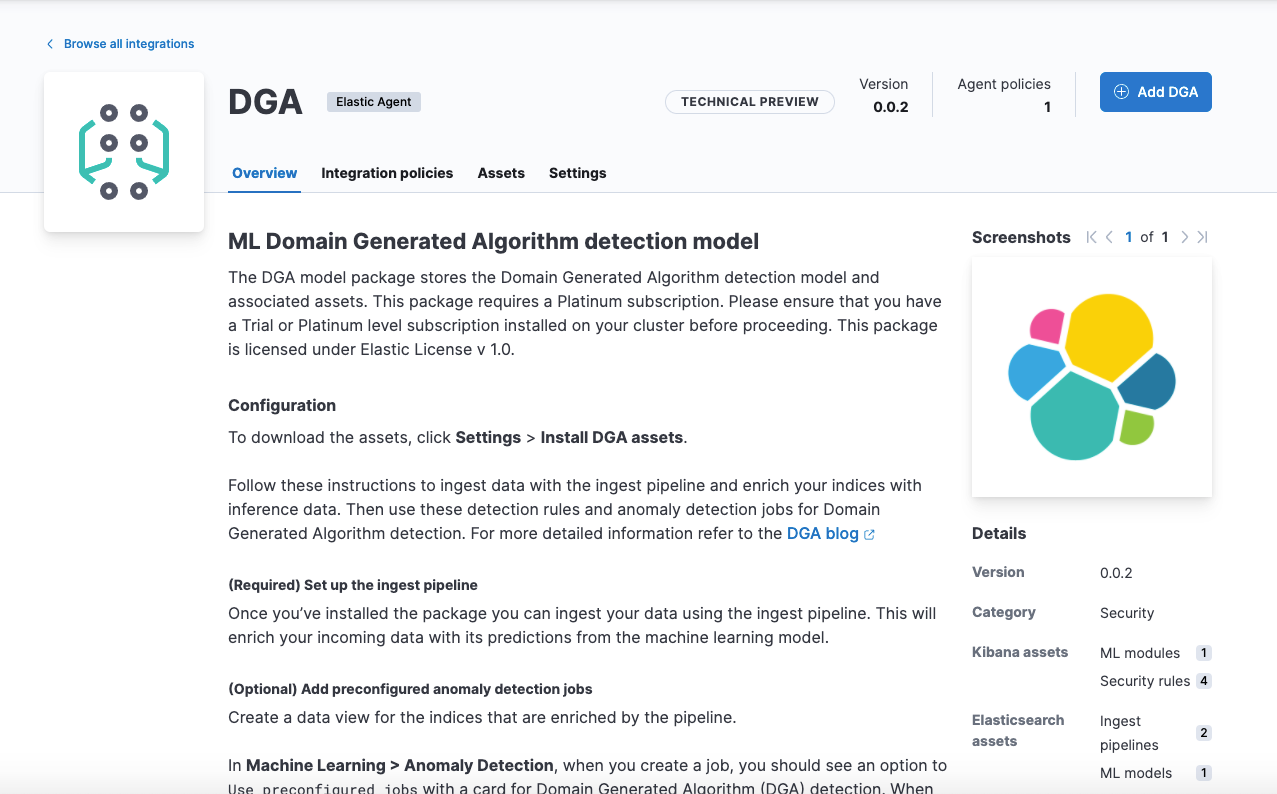
Deploy DGA and Living-off-the-land supervised models in Fleet
editIncorporating supervised models into integration packages allows you to seamlessly install package artifacts inside Kibana with a single click. Now you can deploy DGA and Living-off-the-land (LotL) detection packages within Fleet.
Wildcard support for event filters
editEvent filters now support using wildcard entries for the file.path.text field using the matches operator.
Detection rules enhancements
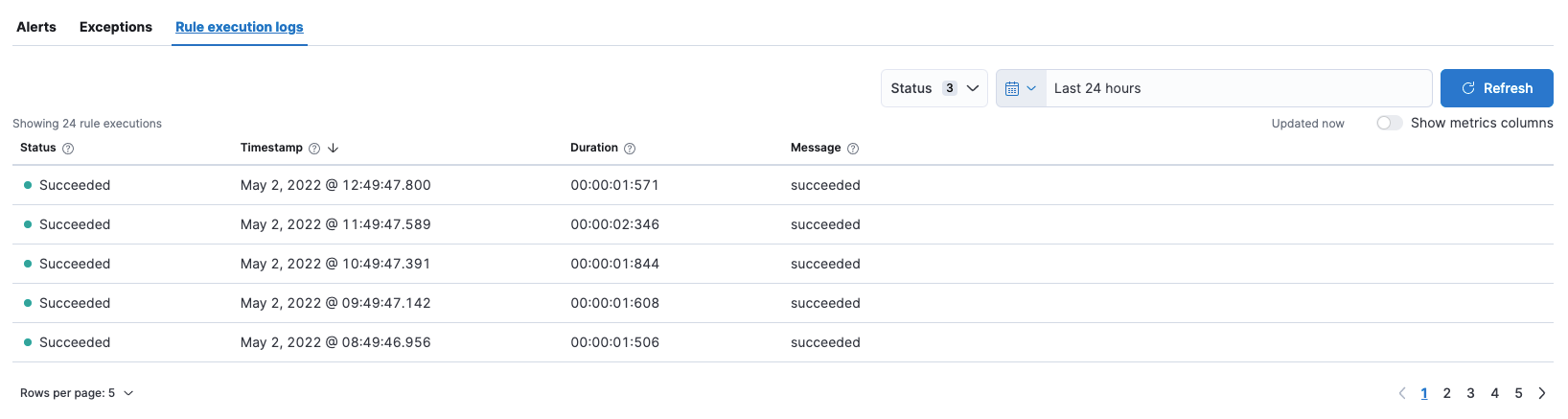
editRule execution logs
editThe new Rule execution logs tab on a rule’s details page provides historical data for the rule’s executions over time. Use this to understand how a particular rule is running and whether it’s creating the alerts you expect.
Bulk apply a Timeline template to rules
editA new bulk actions option allows you to apply a Timeline template to multiple rules at once.
New Rules table filter options
editYou can now filter the Rules table by index pattern, MITRE ATT&CK tactic or technique (name or ID), and rule name.
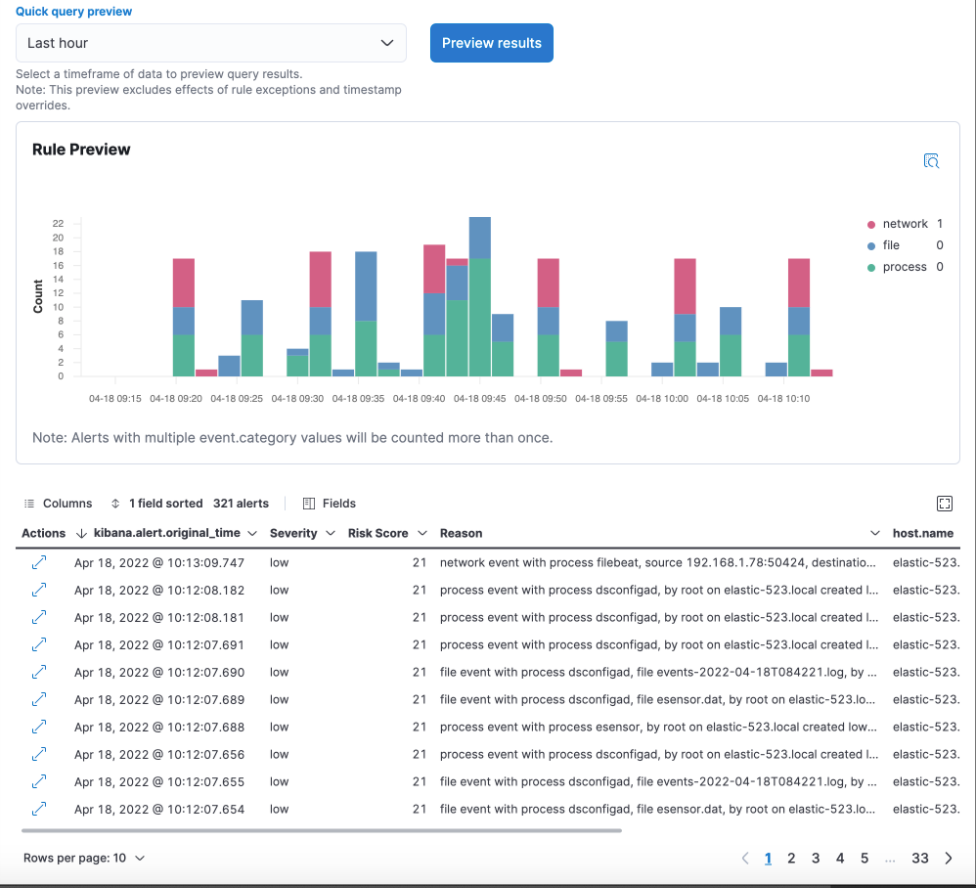
Rule preview feature includes alerts table
When you create or edit a detection rule and preview it, the rule preview now includes an alerts table with the expected alerts for the rule. Use this feature to learn how noisy a rule may be before saving it. You can now also preview indicator match rules.
Turn off read privilege warnings for detection rules
A new Advanced Settings toggle, securitySolution:enableCcsWarning, allows you to turn off read privilege warnings for detection rules using a remote cross-cluster search (CCS) index pattern.
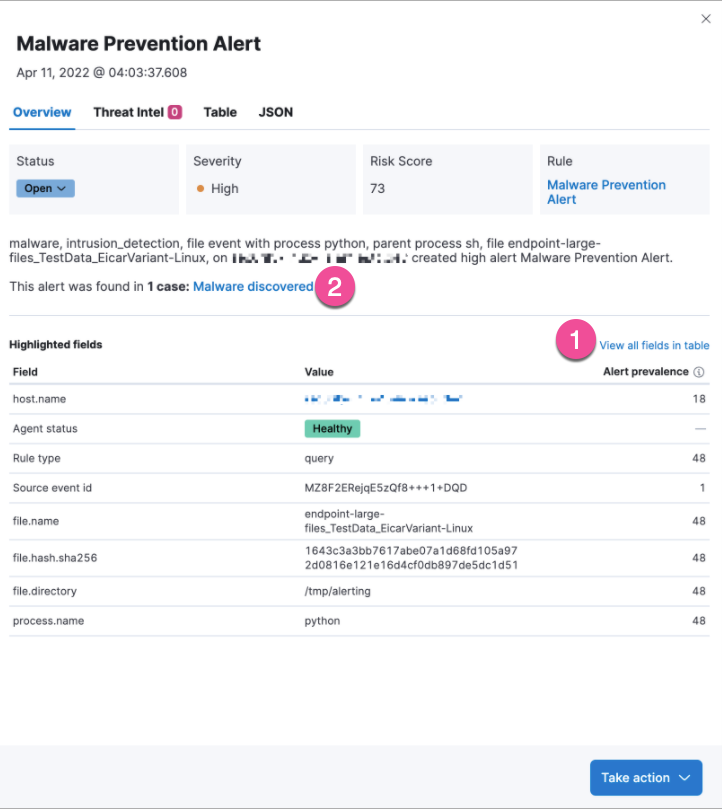
Alert details enhancements
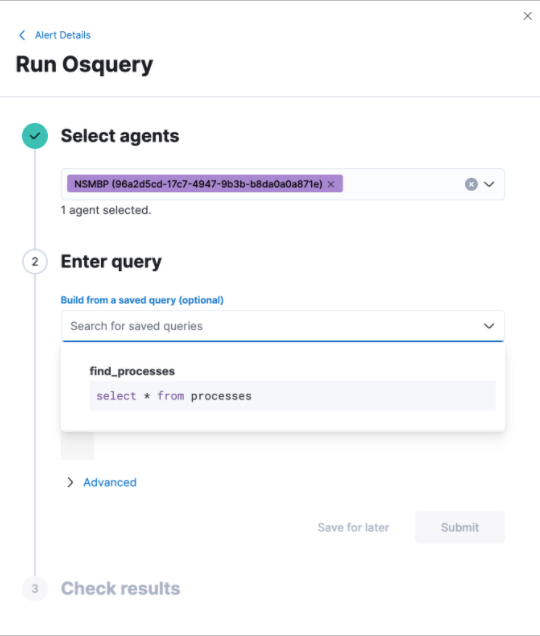
editYou can now run Osquery searches from the Take action menu on the Alert details flyout.
As shown in the image below, a new Alert prevalence column (1) shows the total number of alerts within the selected timeframe that have identical values. The Alert details flyout also now shows linked cases (2).