Quickstart: Secure your cloud assets with cloud security posture management
In this quickstart guide, you'll learn how to get started with Elastic Security for Cloud Security so you can monitor, detect, and investigate anomalous activity within cloud environments.
- You can follow this guide using any deployment. To get up and running quickly, we recommend Elastic Security Serverless with the Security Analytics Complete feature tier. For a complete list of deployment options, refer to Deploy > Choosing your deployment type.
- An admin account for the cloud service provider (CSP) you want to use.
The Cloud Security Posture Management (CSPM) integration helps you identify and remediate configuration risks that could undermine the confidentiality, integrity, and availability of your cloud data.
To add the CSPM integration:
- On the Get Started home page, in the Ingest your data section, select the Cloud tab.
- Select Cloud Security Posture Management (CSPM), then click Add Cloud Security Posture Management (CSPM). The integration configuration page displays.
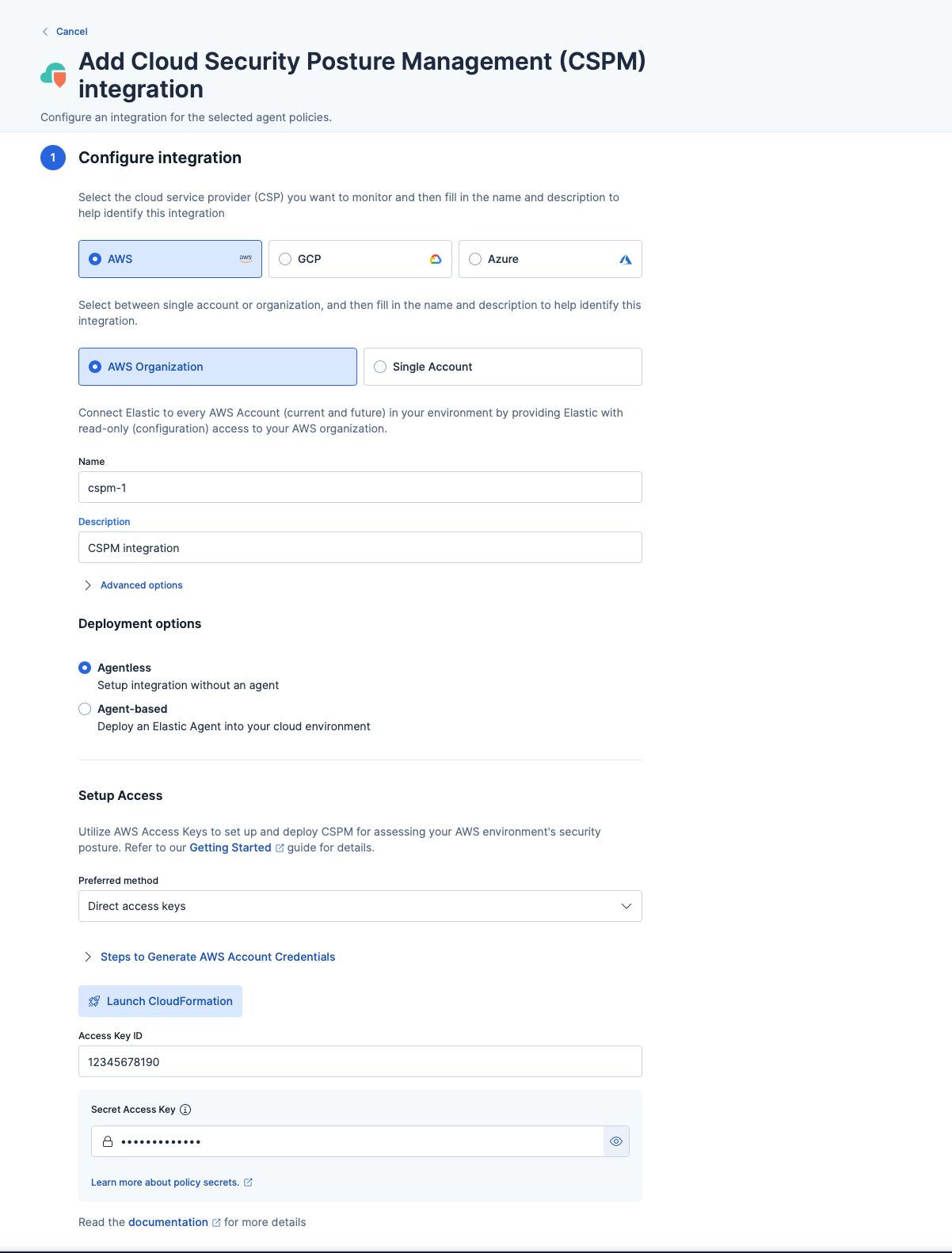
- For this guide, we'll be using a single AWS account. Select these options in the Configure integration section.
- Give the integration a name and enter an optional description.
- Next, choose your deployment option. An agent-based deployment requires you to deploy and manage Elastic Agent in the cloud account you want to monitor, whereas an agentless deployment allows you to collect cloud posture data without managing the Elastic Agent deployment in your cloud. For simplicity, select Agentless.
- Next, in the Setup Access section, choose your preferred authentication method—direct access keys (recommended) or temporary keys. For this guide, we'll use direct access keys.
- Expand the Steps to Generate AWS Account Credentials, and follow the instructions.
- Once you've generated an access key ID and secret access key and pasted the credentials, click Save and continue to complete deployment. Your data should start to appear within a few minutes.
Consider adding the Cloud Native Vulnerability Management (CNVM) integration, which identifies vulnerabilities in your cloud workloads.
The Cloud Posture dashboard summarizes your cloud infrastructure's overall performance against security guidelines defined by the Center for Internet Security (CIS). It shows configuration risk metrics for all your monitored cloud accounts and Kubernetes clusters and groups them by specific parameters. All configuration risks the integration identifies are called benchmark rules and are listed on the Findings page.
The dashboard also shows your overall compliance score and your compliance score for each CIS section. Use these scores to determine how securely configured your overall cloud environment is. To learn more, refer to our documentation.
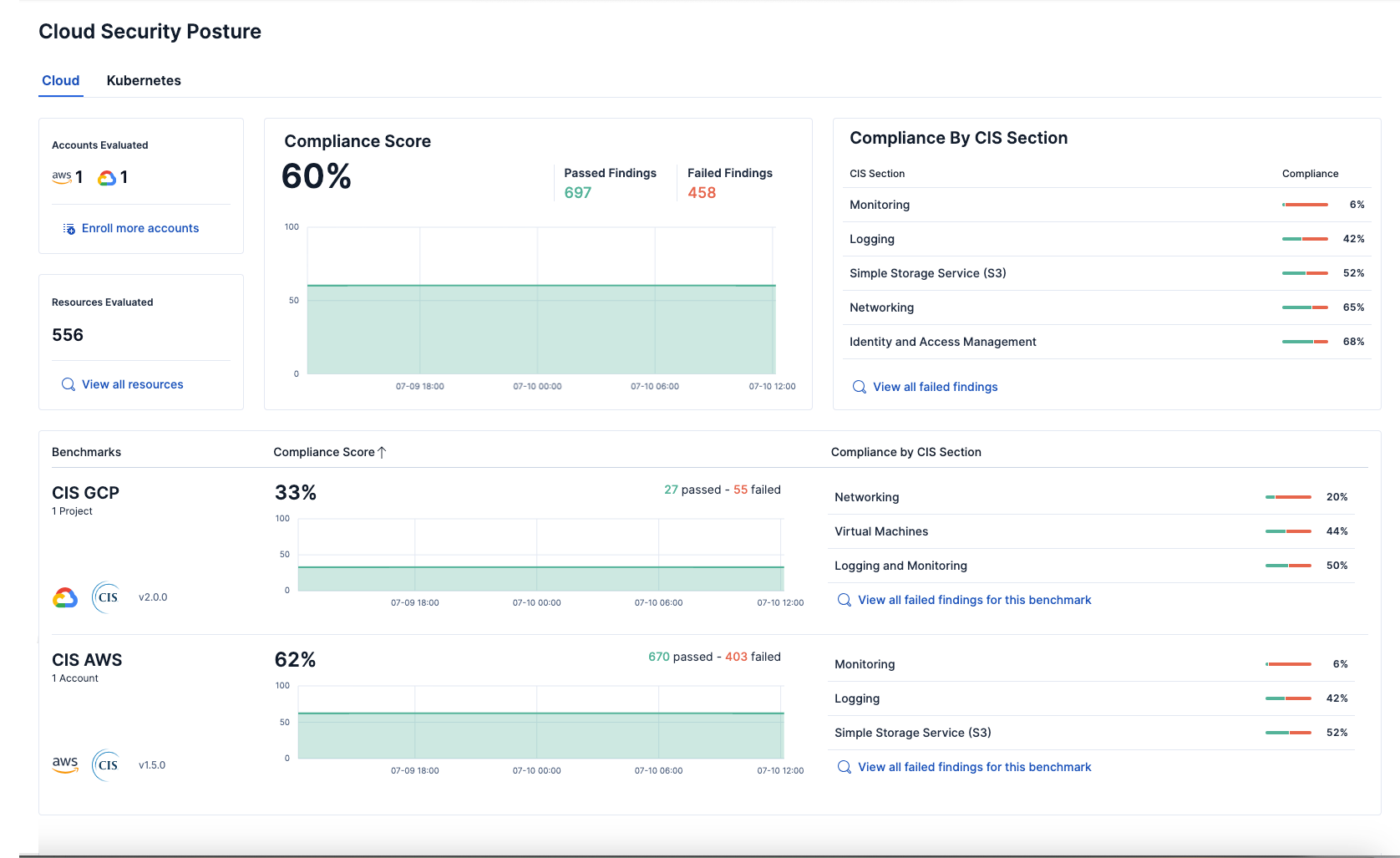
To access the Cloud Security Posture dashboard, go to Dashboards → Cloud Security Posture.
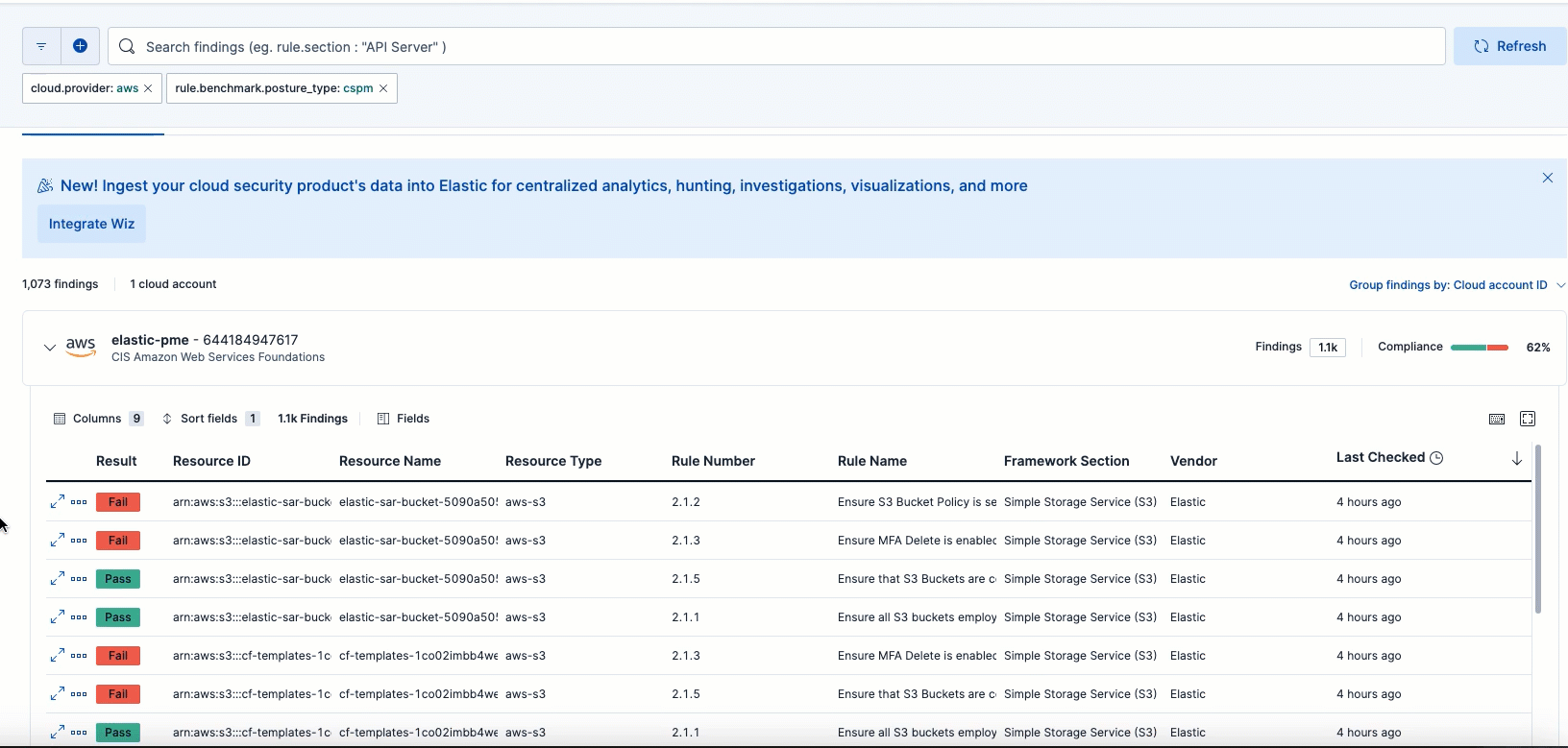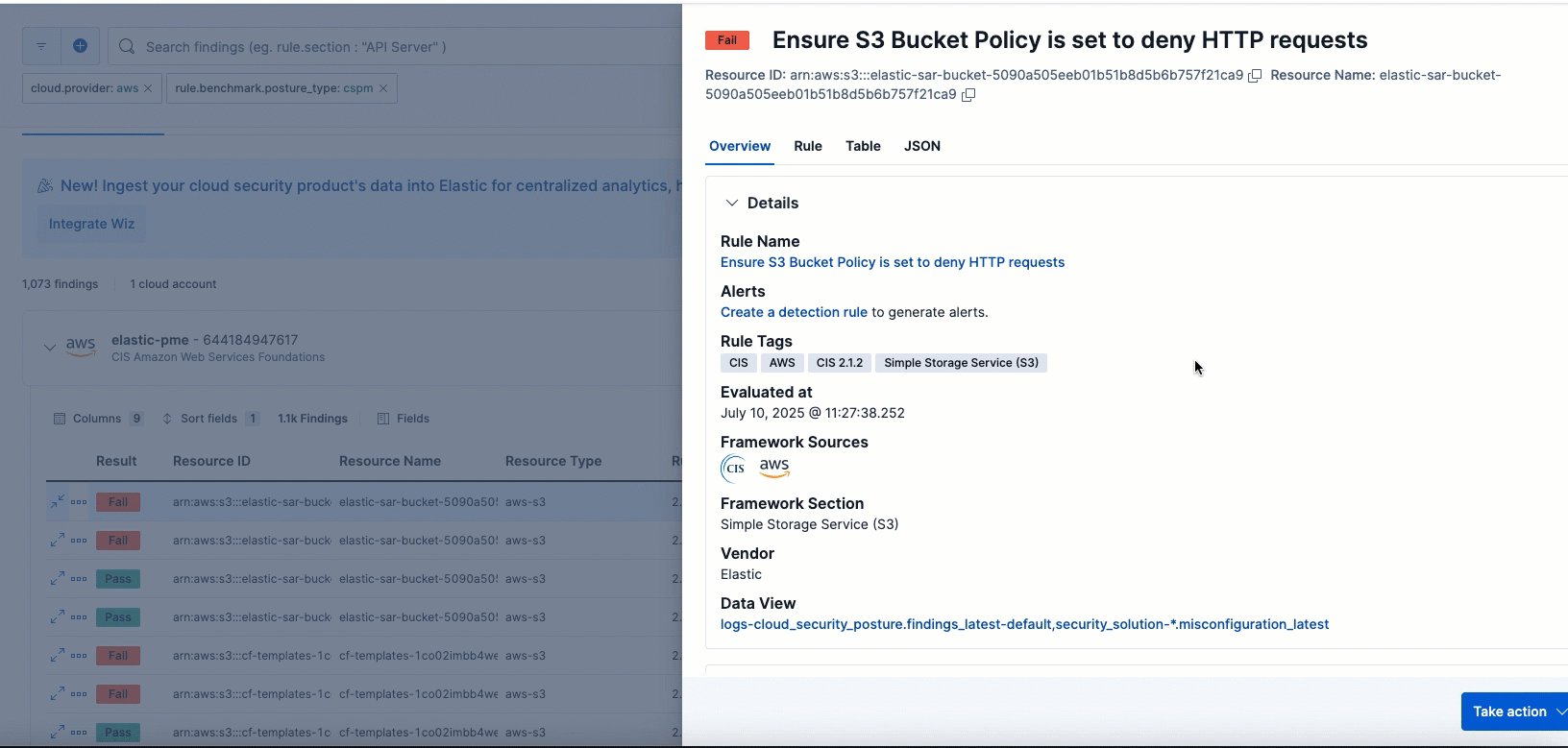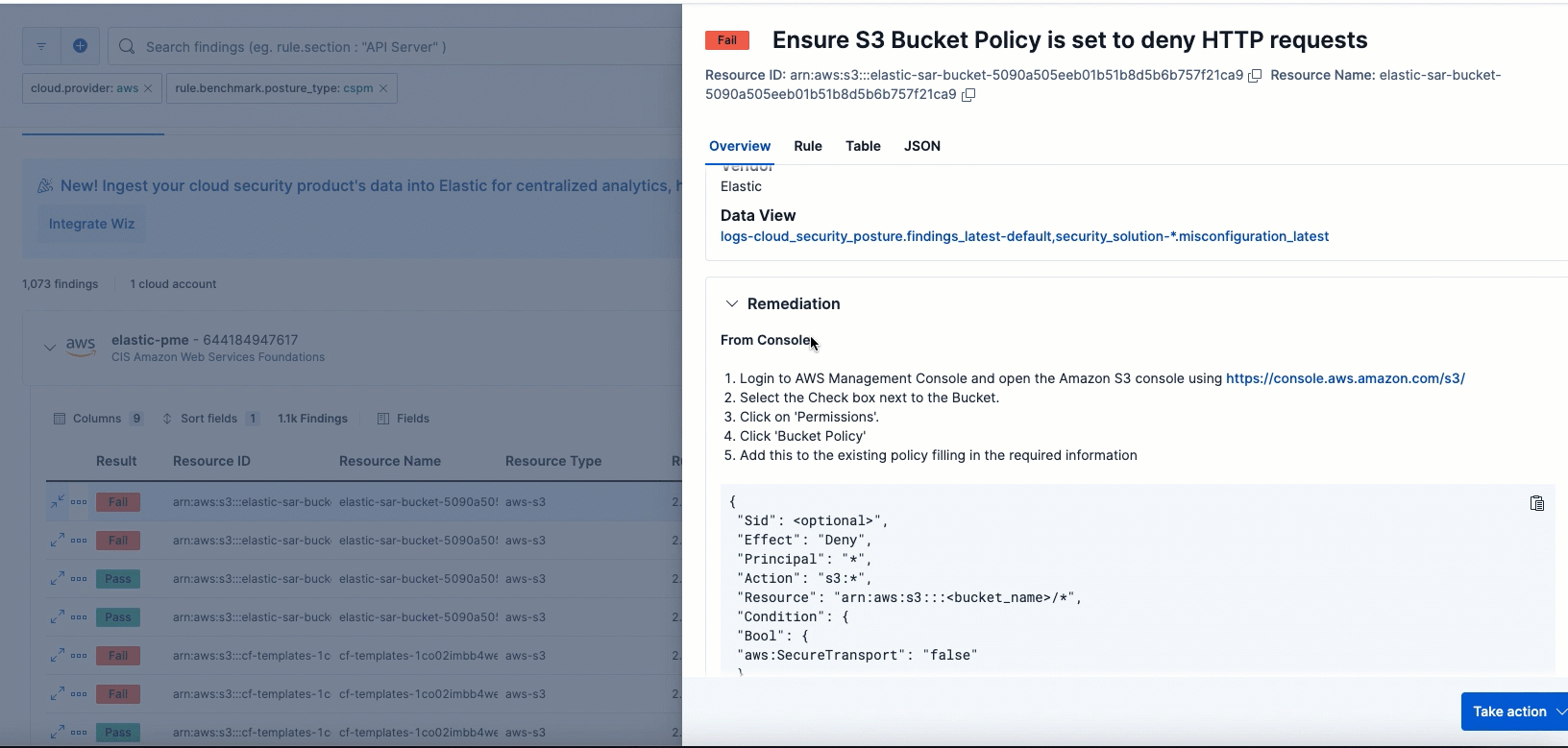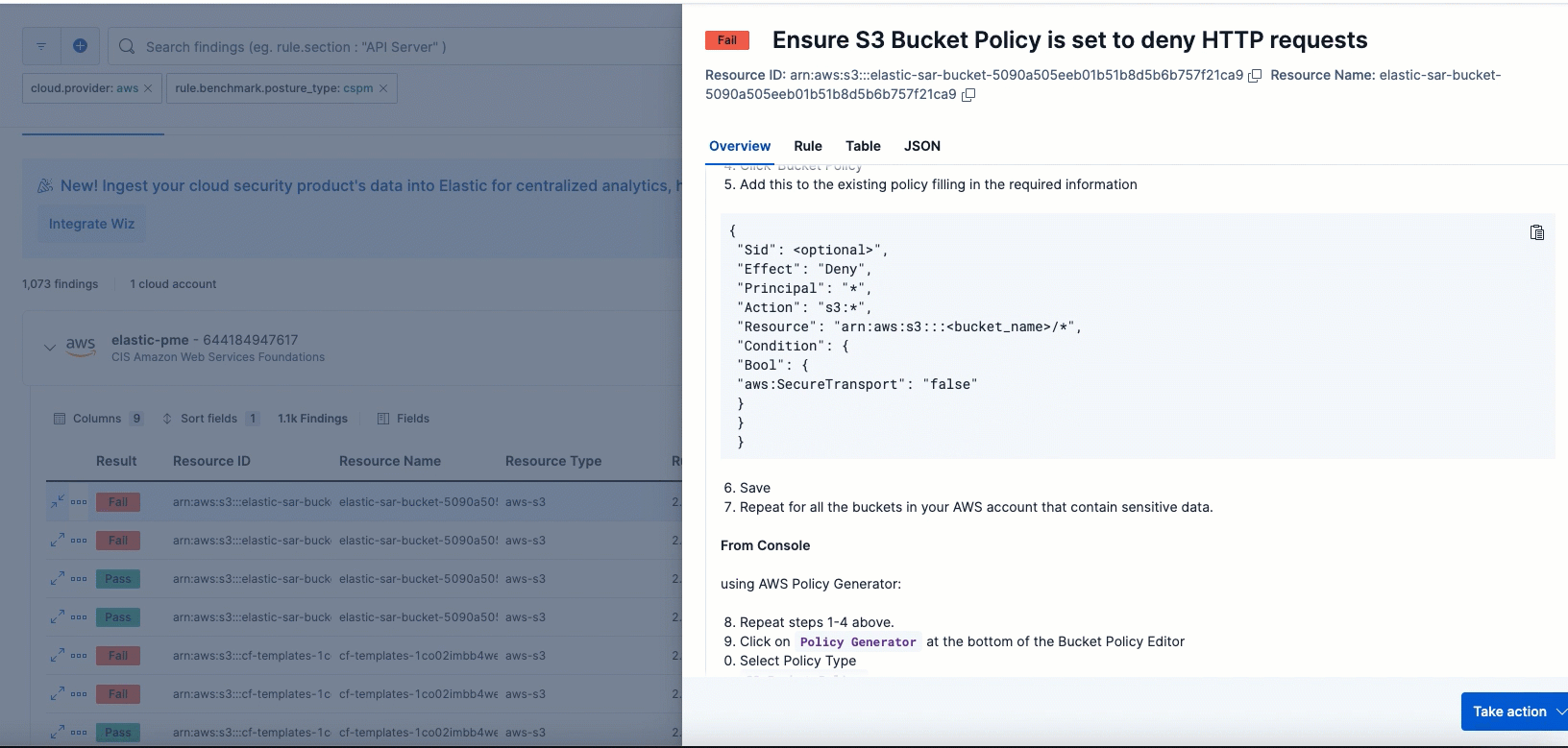
After you install the CSPM integration, it evaluates the configuration of resources in your environment every 24 hours. It lists the results and whether a given resource passed or failed evaluation against a specific security guideline on the Findings page, which you can access from the navigation menu. By default, the Findings page lists all findings without grouping or filtering. However, we recommend filtering the data for failed findings. You can also customize the table to control which columns appear.
To remediate a failed finding, click the arrow to the left of a failed finding to open the findings flyout, then follow the steps under Remediation.
On the Cloud Security Posture dashboard, click one of the "View all failed findings" links to display a filtered view.
To monitor your configuration more closely, we recommend creating detection rules to detect specific failed findings, which, if found, generate an alert.
You can create a detection rule directly from the Findings page:
- Click the arrow to the left of a finding to open the findings flyout.
- Click Take action, then Create a detection rule.
- To review or customize the new rule, click View rule. For example, you might want to set up a rule action—like an email or Slack notification—when alerts are generated. To learn more about rule actions, refer to Create a detection rule > Set up rule actions (optional).
Now that you've configured CSPM, check out these other Cloud Security resources: