Create a TLS certificate rule
editCreate a TLS certificate rule
editWithin the Uptime app, you can create a rule that notifies you when one or more of your monitors has a TLS certificate expiring within a specified threshold, or when it exceeds an age limit.
- To access this page, go to Observability → Uptime.
- At the top of the page, click Alerts and rules → Create rule.
- Select TLS rule.
Conditions
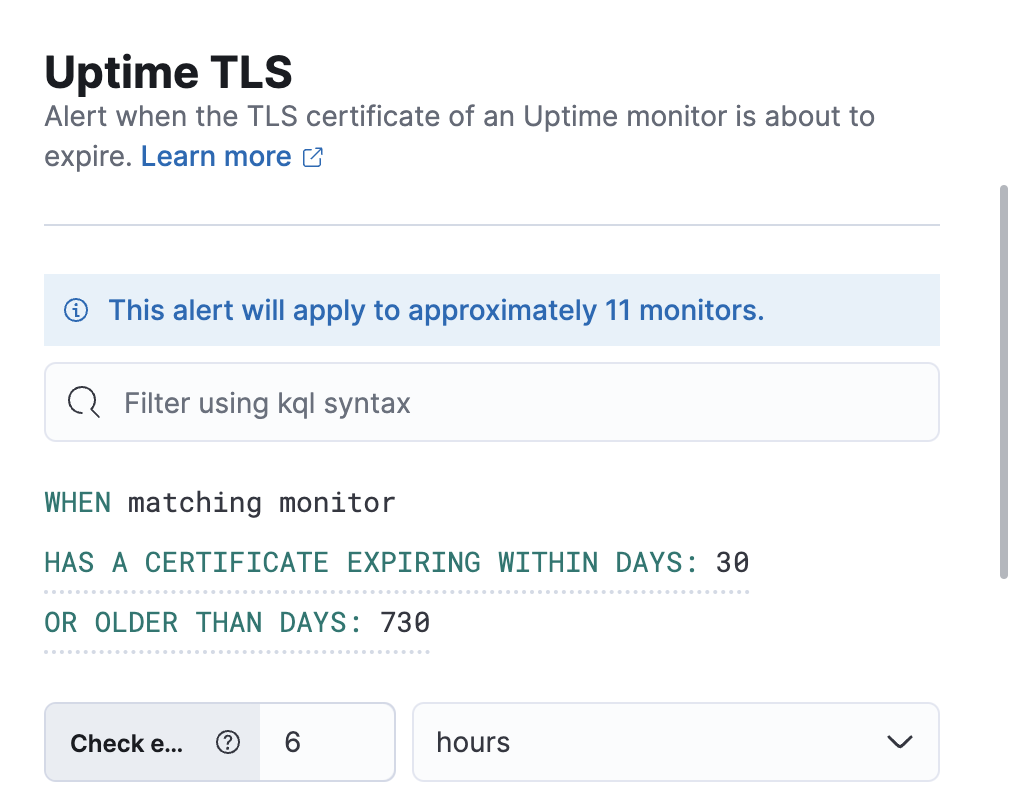
editThe threshold values for each condition are configurable on the Settings page.
You can specify the following thresholds for your rule.
Expiration threshold |
The |
Age limit |
The |
Let’s create a rule to check every 6 hours and notify us when any of the TLS certificates on sites we’re monitoring are close to expiring.
Action types
editYou can extend your rules by connecting them to actions that use the following supported built-in integrations. Actions are Kibana services or integrations with third-party systems that run as background tasks on the Kibana server when rule conditions are met.
You can configure action types on the Settings page.
After you select a connector, you must set the action frequency. You can choose to create a summary of alerts on each check interval or on a custom interval. Alternatively, you can set the action frequency such that you choose how often the action runs (for example, at each check interval, only when the alert status changes, or at a custom action interval). In this case, you must also select the specific threshold condition that affects when actions run: Uptime TLS Alert or Recovered. For example, send a notification when an alert status changes:
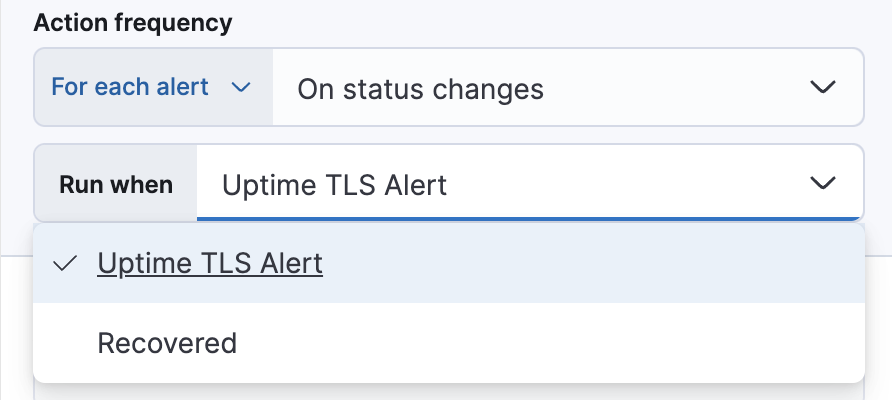
In this example, actions are not repeated when an alert remains active across checks. Actions run only when the alert status changes.
Action variables
editUse the default notification message or customize it. You can add more context to the message by clicking the icon above the message text box and selecting from a list of available variables.
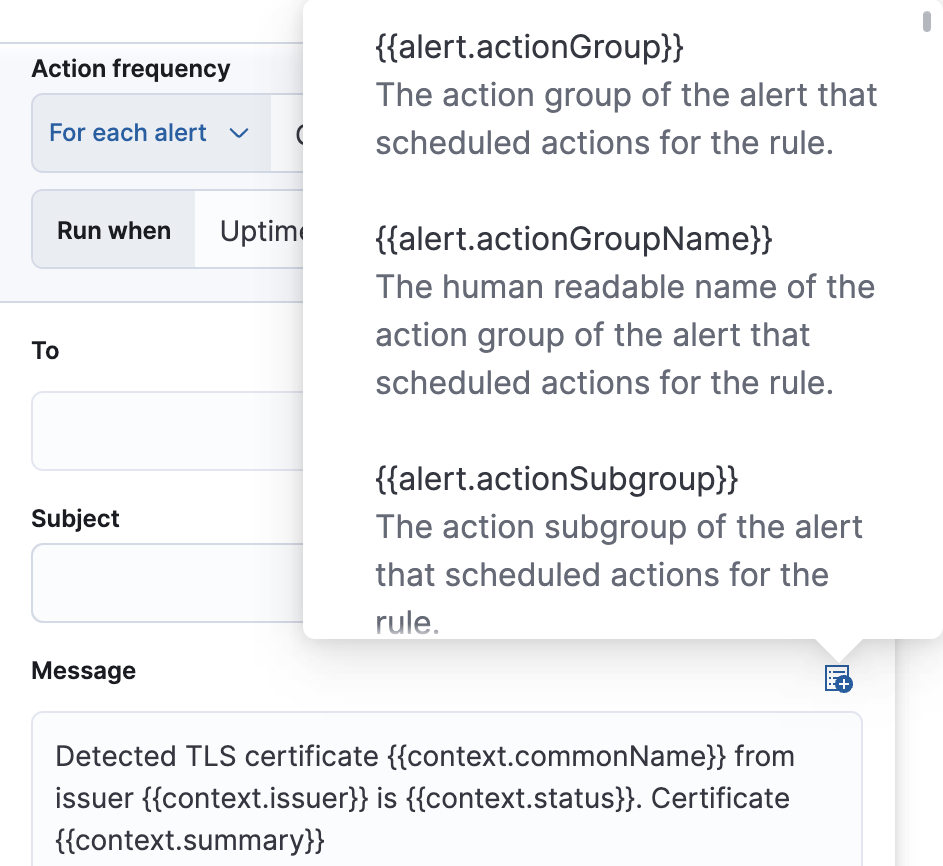
Alert recovery
editTo receive a notification when the alert recovers, select Run when Recovered. Use the default notification message or customize it. You can add more context to the message by clicking the icon above the message text box and selecting from a list of available variables.