Preventing "copy-paste compromises" (ACSC 2020-008) with Elastic Security
Editor’s Note — August 19, 2020: The Elastic Endpoint Security and Elastic SIEM solutions mentioned in this post are now referred to as Elastic Security. The broader Elastic Security solution delivers endpoint security, SIEM, threat hunting, cloud monitoring, and more.
The Australian Cyber Security Centre (ACSC) recently published an advisory outlining tactics, techniques, and procedures (TTPs) used against multiple Australian businesses in a recent campaign by a state-based actor. The campaign — dubbed ‘copy-paste compromises’ because of its heavy use of open source proof of concept exploits — was first reported on June 18, 2020, receiving national attention in Australia. While urgency may be exaggerated in certain reports, it is worth noting that the ACSC generally publishes threat advisories only a few times a year.
As reported by the ACSC, in these attacks, the actor initially targets networks using vulnerable or unpatched web-facing assets. On failing to do so, spear phishing techniques were leveraged to try and gain access to infrastructure. These sort of attacks are fairly common, and Elastic Security is a powerful tool for shutting them down. With Elastic SIEM and Elastic Endpoint Security, security analysts gain a full view of your environment and whether any bad actors are trying to exploit their systems.
The advisory references the MITRE ATT&CK® framework to communicate the TTPs observed in the campaign. Detections and alerts in Elastic Security are tagged using the same framework, making it convenient for security practitioners to digest advisories like these in reference to the detection capabilities they have in place.
This blog post highlights some of the ways Elastic Security can better protect organisations targeted by groups like those described in this report. Regularly assessing security capabilities against reports such as this one helps organizations prepare for a variety of threats that may occur in the future.
Before we get started…
This post is specifically for detecting the use of some of the copy-paste compromise techniques. Organisations should design their security strategy using the concept of defence in depth. Addressing issues such as unpatched web-facing applications, network segmentation, least privilege administration, and unmanaged endpoints will significantly reduce exposure to adversaries like these.
Preventing copy-paste compromises with Elastic Security
Enable your Endpoint sensor policies
Elastic Security 7.8 provides over 100 detections right out of the box, including ones ACSC has identified for the copy-paste compromises. These include detections for attacks of execution, persistence, defence evasion, credential access, discovery, lateral movement, and exfiltration.
With Elastic Endpoint Security, you can intuitively configure the appropriate threats and adversary behaviours on endpoints to ensure tactics and techniques leveraged by the actor can be detected. A list of targeted TTPs can be seen under each detection.
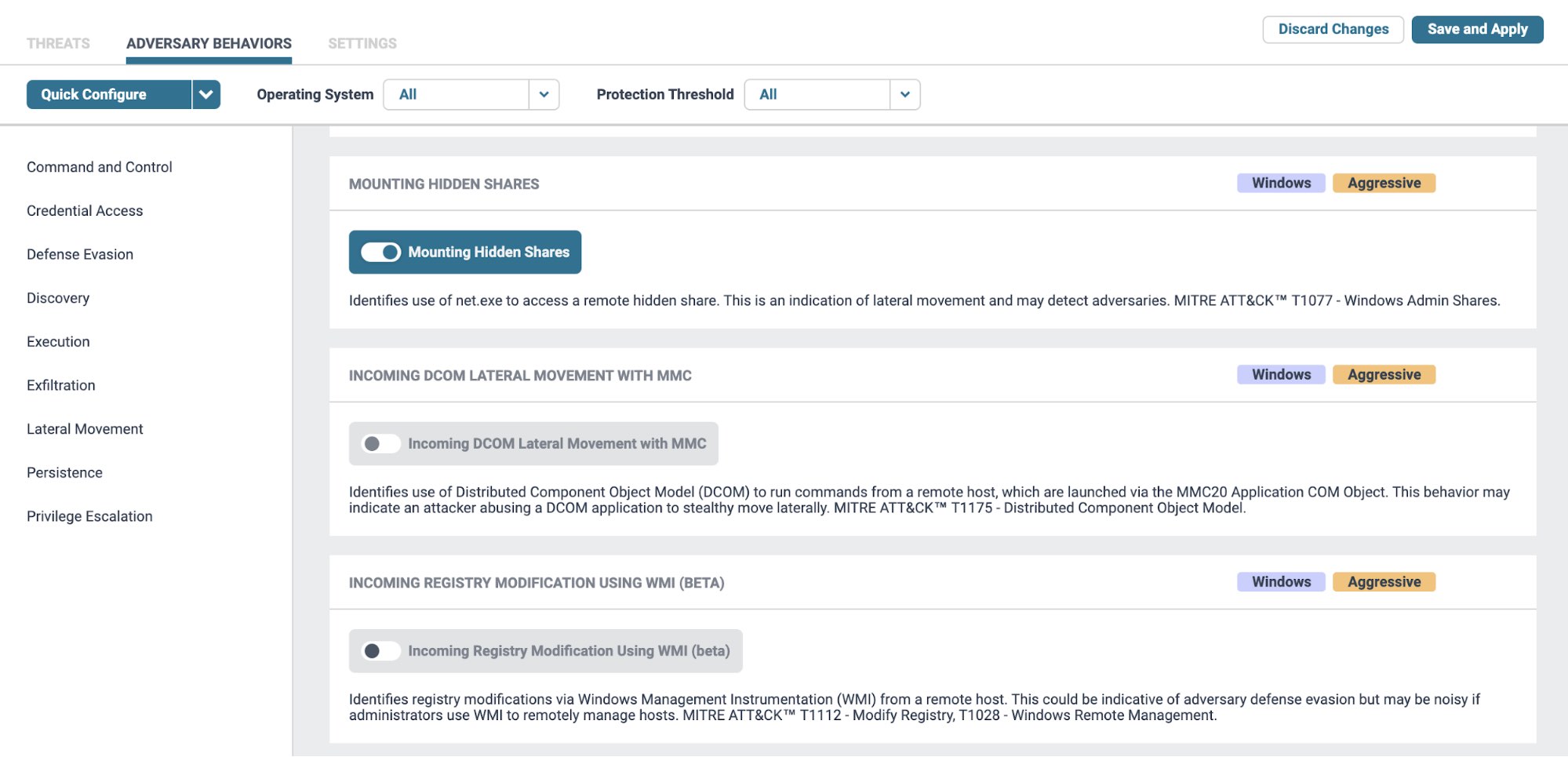
While Detect mode can alert on suspicious or potentially malicious activity, Prevent mode could be used to allow Endpoint to automatically respond to threats. It's important to note that this advanced functionality will create increased processing overhead on the endpoint, and must first be tested on a sample group of hosts before rolling it out across the fleet.
Add IoCs into Elastic SIEM
Enhance your SIEM Detection rules with the Indicators of Compromise (IoCs) published by the advisory. SIEM Detections automatically search for threats in your data based on a query you define. Users can use prebuilt rules created for commonly used data sources, or define their own rules for custom data.
A SIEM detection rule was created for each of the 9 types of indicators available. This allows for the scanning of historical data to look for signs of compromise in your environment. While IoCs may have a limited shelf-life — and shouldn't be solely relied on for detecting threats — they are still important pieces of information about intrusions which should be curated. By understanding how adversaries have succeeded in the past, we better prepare ourselves for defeating them in the future.
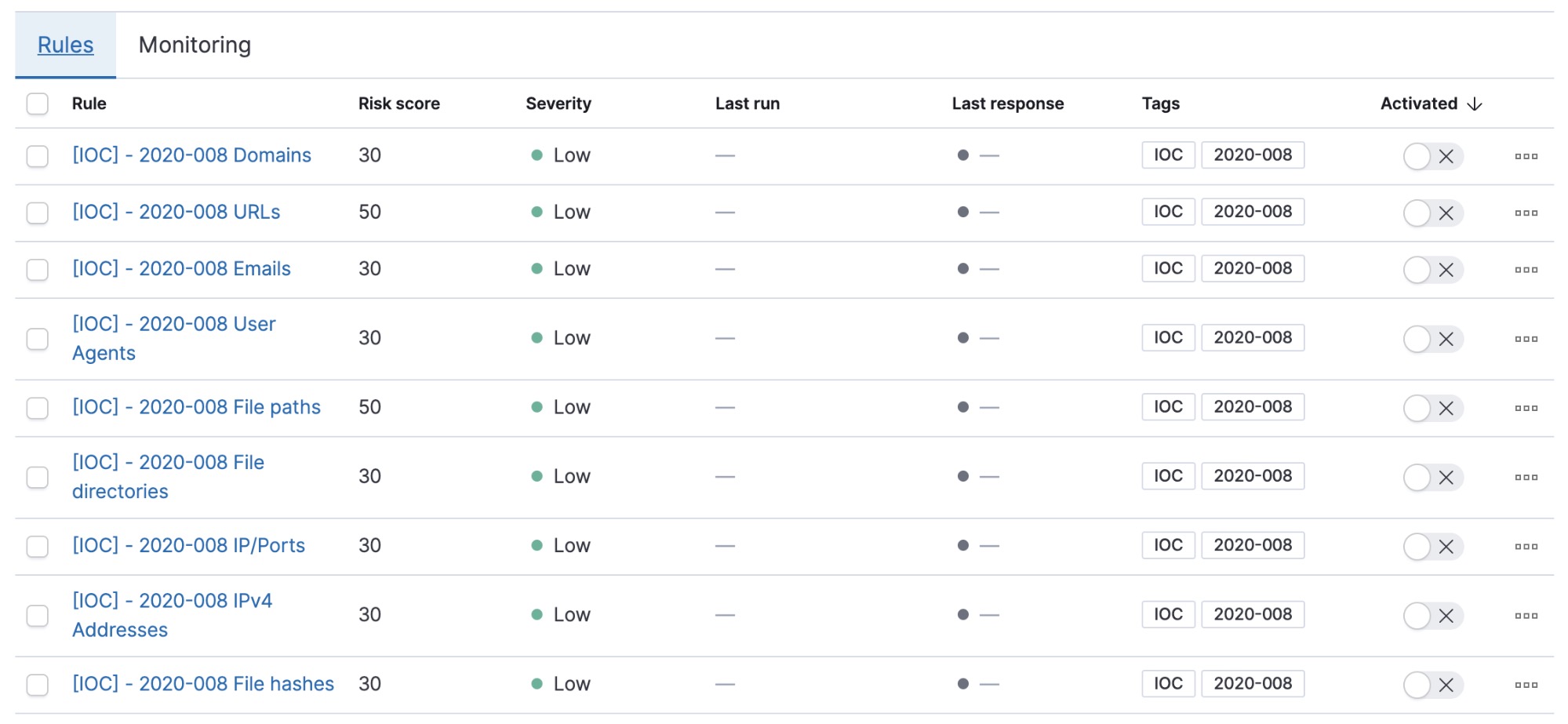
- Download the
acsc-2020-008-IOCs.ndjsonfile containing the SIEM detection rules from Elastic’s GitHub repository. All rules are tagged withIOCand2020-008for convenient filtering and management in the SIEM app - Import the rules into SIEM
- Review the field names used within the rules. The rules currently reference default Elastic Common Schema (ECS) fields, but your field names may vary internally
- Activate rules as required
Note that the SIEM rules currently run every 60 minutes, looking back at events from the last 60 minutes. The rules currently do not run actions for every execution. If you need to act on detections, it would be a good idea to modify the execution frequency that suits your needs to action, investigate, and respond accordingly.
Any events across your infrastructure (logs, metrics, endpoint, and other sources) that match the IoCs created will show up in the SIEM overview dashboard.
Identify gaps in visibility
Having visibility across multiple data sources is important for being able to detect, prevent, and respond to these threats. It is worth looking at your complete network architecture to ensure some level of logging and monitoring across critical components.
While it is a good idea to aim for maximum logging visibility across all components in your environment, based on the ACSC report on the copy-paste compromise, a good start would include:
| Endpoint | EDR telemetry, File integrity monitoring |
| Network/security appliances | Proxy, DNS, DHCP, NAC, Firewall, VPN, Active Directory |
| Critical systems | Collaboration tools (Office 365/Google Drive), Single Sign On request logs, Email logs |
| Applications | Database audit logs, Object storage access logs, File-share access logs, Cloud audit logs (AWS Cloudtrail, Google Cloud Audit logs) |
Elastic offers a wide variety of out-of-the-box integrations and modules for logging and metrics sources to help with this level of observability. If an integration you’re looking for is not yet available, custom ingest pipelines or Logstash can be leveraged to bring this data in.
Next steps
While this blog post is intended for those specifically concerned with the copy-paste compromise, these are some general security practices that are always a good idea to implement (in no particular order). Elastic also offers consulting services for organisations interested in receiving guidance tailored to their specific needs and focus areas.
Invest in an effective vulnerability management and patching process
Vulnerabilities, especially in public-facing infrastructure, are often the easiest way in for adversaries to get a leg in. Tracking CVEs for your critical infrastructure and patching vulnerabilities in a timely manner can help harden the attack surface.
Audit third-party accounts
Regularly auditing third-party accounts and access into your organisation using the principle of least privilege reduces the risk of supply chain compromises.
Monitor threat intelligence feeds and advisories for your industry
Ingest and enrich your events with threat intelligence feeds that may be relevant to you. Open source feeds such as MISP can be a good starting point. You may also opt to subscribe to a more curated intelligence feed from a number of vendors in the market.
User training (can also be part of security & compliance training)
Social engineering is often the most effective way of breaching an organisation. Attackers only need to get lucky once, while users need to be vigilant all the time. Phishing and social engineering drills can be an engaging way to educate users, alongside the standard security compliance training most organisations mandate.
Hunt and investigate using Elastic SIEM
Make the most of the SIEM app to hunt for threats, conduct investigations, and manage security cases. Some resources to help you get started include:
- Guide on getting started with SIEM
- Webinar on defending your organization with the Elastic Stack
- Webinar on enhancing security analyst workflow with the Elastic SIEM
- Read the Elastic Guide to Threat Hunting