Elastic Security Labs: Follow us for breaking news on security threat research

Elastic Security Labs is now the official, one-stop domain for threat research from a team of 40+ industry veterans.
Elastic has been delivering timely and detailed security threat research for years — we’ve published more than 40 research articles and tools. We want to make it easier to find and share security threat research that will lead to a more secure workplace and a more protected industry overall.
“We feel that the availability of topical and timely security threat research has been traditionally inaccessible,” said Devon Kerr, Elastic Security Research Lead. “Elastic Security Labs intends to change this disparity and put in every security practitioner's hands the needed information and tools to protect their organizations.”
[Read more about CUBA and other malware here.]
Leverage Elastic Security Labs for your organization
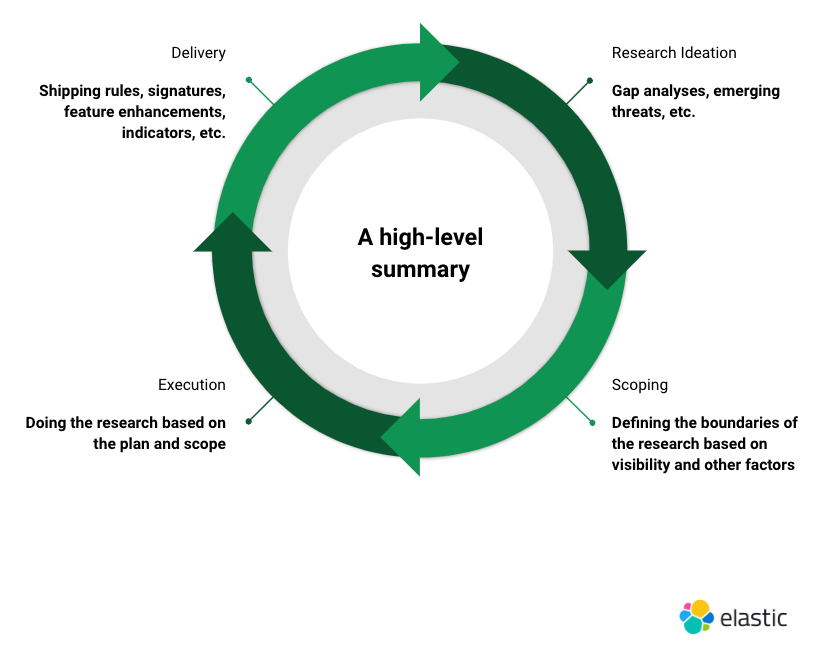
Threat research is a process. We approach it methodically to decide what research we want to take on. Elastic Security Labs approaches it by considering the following four steps:
1) Research ideation
2) Scoping
3) Execution
4) Delivery
We want security teams to have as complete a picture as possible when detecting a threat or developing security strategy.
To accomplish this, we need to think about threat research as several related domains, including threat intelligence, detection science, and malware analysis. Having a complete picture gives you confidence when something goes bump in the night — and when you’re confident something is truly a threat, you can respond more quickly.
Organizations often spot elements of an intrusion early in the process, but dismiss those observations or misunderstand them — leading to worse outcomes. If we can help inform that process and reduce the time to respond, we can steer them towards better ones. And, if your organization has struggled to hire or retain people with the right knowledge and skills to achieve that, you can benefit from ours.
Every rule, signature, and indicator, as well as many features or feature enhancements, are the direct result of threat-centric research. By seeking a deep and comprehensive understanding of a given threat, technique, or phenomenon, we learn enough to try and change outcomes for the better. It’s more than just surveying the threat landscape and reporting on it — it’s understanding those observations so that we can translate them into actionable guidance.
Research plans from Elastic Security Labs
We deliver research across several topic areas, including Security Research, Malware Analysis, Campaigns, and Groups and Tactics.
Security Research and Malware analysis are essential when most intelligence information is low-context. We want your team to understand things we’re observing to the same degree that we do, and we want to supply you with resources aligned to those threats. This helps you make decisions about your environment based on what the threat has done, what we assess the threat to be capable of, and your own risk tolerance.
To do that, we link reports like this one to a variety of resources, such as:
- Malware analysis reports for implants and tools
- Utilities we wrote for ourselves but feel you can benefit from
- Summaries of techniques we’ve observed
- Artifacts like rules and signatures that you might want to enable
We monitor Elastic telemetry and numerous third-party resources to develop our analyses, and pass the results on to you.
Attack patterns and related research have become relatively commonplace, and we think they are a core component of a mature security program. We are constantly monitoring for novel techniques, variations, and weaponized features. This is an important way we’re continually pushing our instrumentation forward and helping other Elastic engineering teams prioritize improvements.This is closely related to the science of detection, which anyone can learn to do effectively.
When we mention techniques or tactic-categories, we link to related research and artifacts so you can understand where your environment might need edge-cases covered and make better decisions about prioritization. We feel a duty to mention that many of our logic repositories are community-facing, which means you can commit those right back and help the community.
Not many enterprises maintain a team solely to analyze and reverse malware, and many of the organizations that offer such services are not universally affordable. We look at Elastic telemetry, third-party statistics, and our own capability innovations to identify a variety of malware. And none of this would be possible without our many excellent partners at Elastic who share our source code and embrace this mission. It also wouldn’t be possible without our community.
Highlights from recent research
This week, we wanted to highlight our top research articles and some of our most recent ones as well.
- Elastic Security Labs identified BLISTER in December of last year, and because of this research, it’s almost been eradicated from the internet.
- Most recently, our Linux researchers wrote about eBPFdoor, which is a way to leverage the power of BPF’s to circumvent detection.
- And, our most read research piece was the four articles we published on Log4j. We quickly identified Log4j, then provided a detailed analysis, shared how to protect with Elastic, and followed up about the Spring version too.