Elastic vs. Splunk for logs, security, and observability
The right observability and security solution is fast, affordable, and built for the future of generative AI.

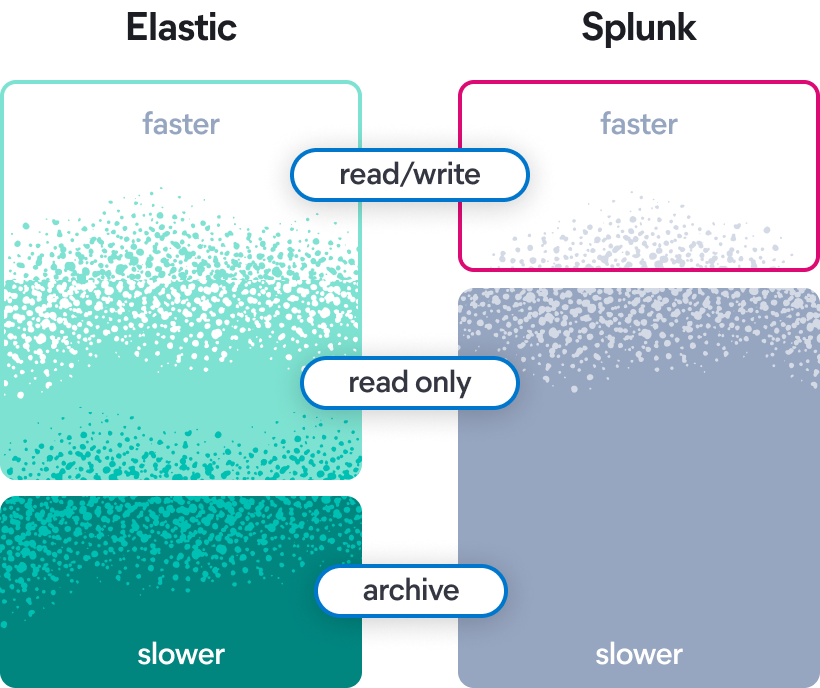
Review the key differences between the Elastic and Splunk data tiers.
Read the blogSay goodbye to Splunk limitations — elevate observability with Elastic.
Read the blogStay ahead of threats. Empower your teams with AI-driven security analytics.
Read the blogElastic vs. Splunk: Key differences
Elastic
Splunk
Elastic
Splunk
See why companies like yours choose Elastic
Learn about the real-world benefits of using the Elastic Search AI Platform for observability and security.

Informatica cuts costs, accelerates mean time to resolution (MTTR), and stays one step ahead of threats to system performance — all with a unified observability and security solution.

UOL turbocharges its security operations, achieving 80% faster incident resolution and seamless threat management, all powered by Elastic Security.

Comcast enables its engineers to iterate and innovate faster with essential feedback from Elastic Observability.
Splunk Replacement for Data Management
Elastic vs. Splunk: Cold truth about data tiers
To be successful with Splunk, you need dedicated resources plus a near-term and long-term storage strategy. Many Splunk customers struggle to align their evolving business needs to the correct data storage option.
But with Elastic, you get simple, straight-forward, and centralized data management — with no hidden agenda or costs. Search across geos in milliseconds, not seconds. Query archival tiers in minutes, not hours. Compare the capabilities of Splunk versus Elastic data tiers so you can make an informed, cost-effective decision.
Splunk Replacement for Logging
Elastic Observability
In Splunk, logs are fragmented and separated from traces and metrics. Teams cannot see the full picture on one screen. Take the first step by consolidating your logs on Elastic and gain the benefits of a unified observability solution built with Search AI. With end-to-end visibility across all your logs, metrics, and traces, correlated and in context, you can decrease MTTR and lower TCO.
Splunk Replacement for SIEM
Elastic Security
Many legacy SIEMs, like Splunk, weren't built to adjust to your business's needs. AI-driven security analytics is critical to adapt to the latest breed of threats. Accelerate SecOps workflows and reduce risk with Elastic. You get limitless scalability, advanced analytics, and generative AI insights to eliminate blind spots, strengthen defenses, and mitigate the global cyber skills shortage. The AI revolution is here — and SIEM will never be the same.
Splunk and other related marks are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. All other brand names, product names, or trademarks belong to their respective owners.