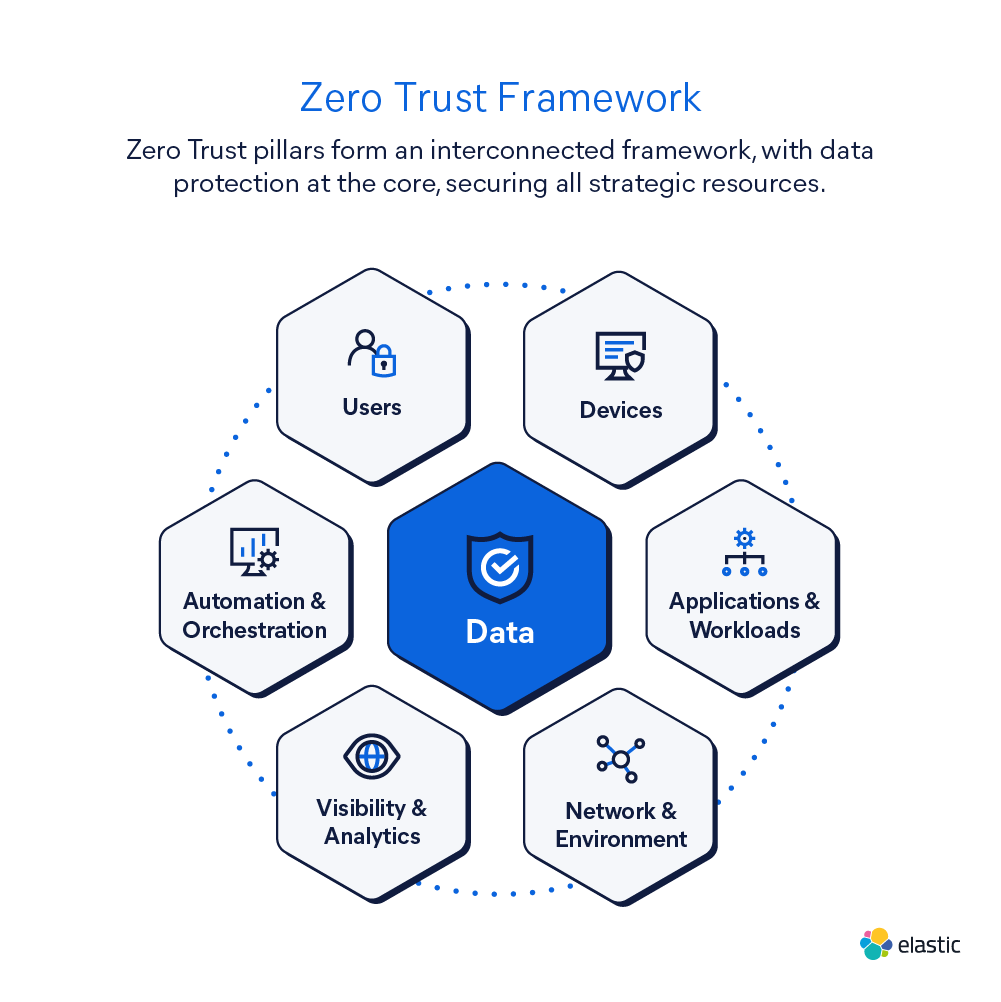
Simplify Zero Trust with a data-centric approach
Zero Trust is changing how organizations protect data, users, and systems in an increasingly complex cybersecurity environment. Elastic connects data across systems and environments for unified Zero Trust visibility and analytics.
Discover how finance, healthcare, and government institutions are using Elastic to operationalize Zero Trust strategies for a full view of cybersecurity threats.

Benefits of building a unified Zero Trust Architecture with Elastic

Customer spotlight
How a US federal agency achieved Zero Trust cyber defense with Elastic
A large federal agency modernized its cybersecurity operations with the Elasticsearch Platform at the core of its Zero Trust strategy. The results:
- Reduced costs by leveraging Elastic's FedRAMP-authorized cloud platform
- Boosted analyst productivity with AI-powered alerts and automation
- Stronger risk mitigation through real-time threat detection and rapid response
- Simplified compliance with OMB, CISA, and other federal mandates
Elastic's Zero Trust resources
Zero Trust FAQ
Zero Trust is a modern security framework built on the principle of "never trust, always verify."" Users and devices are never implicitly trusted, whether inside or outside the network perimeter. Every access request must be continually verified and authenticated before access is granted or maintained.
Today, Zero Trust is critical because of advanced threats, insider risks, and hybrid cloud growth. Many organizations — including the US federal government — are now mandated to adopt Zero Trust Architectures.
Zero Trust requires orchestrating risk across multiple pillars: identity, device, network, application, and data. This is complex when information is locked in siloed tools.
Elastic simplifies Zero Trust with a data mesh approach that unifies data from every pillar into one secure platform. This enables organizations to ingest, analyze, and act on threats seamlessly — while still integrating with existing systems.
Most Zero Trust frameworks share three core principles:
- Continuous verification — validate every access request, every time.
- Least privilege access — grant only the minimum permissions needed.
- Assume breach — design security as if attackers are already inside.
Broader principles include identity-based access, multifactor authentication (MFA), microsegmentation, and continuous monitoring.
Zero Trust goes beyond perimeter-based security, which relies on firewalls and implicit trust. Traditional models can't stop lateral movement of attackers or insider threats.
By adopting Zero Trust, organizations gain:
- Reduced risk of breaches through continuous verification
- Protection for hybrid and remote workforces across devices and locations
- Faster response to advanced cyber threats
- Operational efficiency by replacing fragmented tools with a holistic security framework
Zero Trust enables a proactive, adaptive defense that saves security teams time and keeps pace with modern IT complexity.