Deploy Elastic Defend on macOS with mobile device management
editDeploy Elastic Defend on macOS with mobile device management
editTo silently install and deploy Elastic Defend without the need for user interaction, you need to configure a mobile device management (MDM) profile for Elastic Endpoint—the installed component that performs Elastic Defend’s threat monitoring and prevention. This allows you to pre-approve the Elastic Endpoint system extension and grant Full Disk Access to all the necessary components.
This page explains how to deploy Elastic Defend silently using Jamf.
Configure a Jamf MDM profile
editIn Jamf, create a configuration profile for Elastic Endpoint. Follow these steps to configure the profile:
Approve the system extension
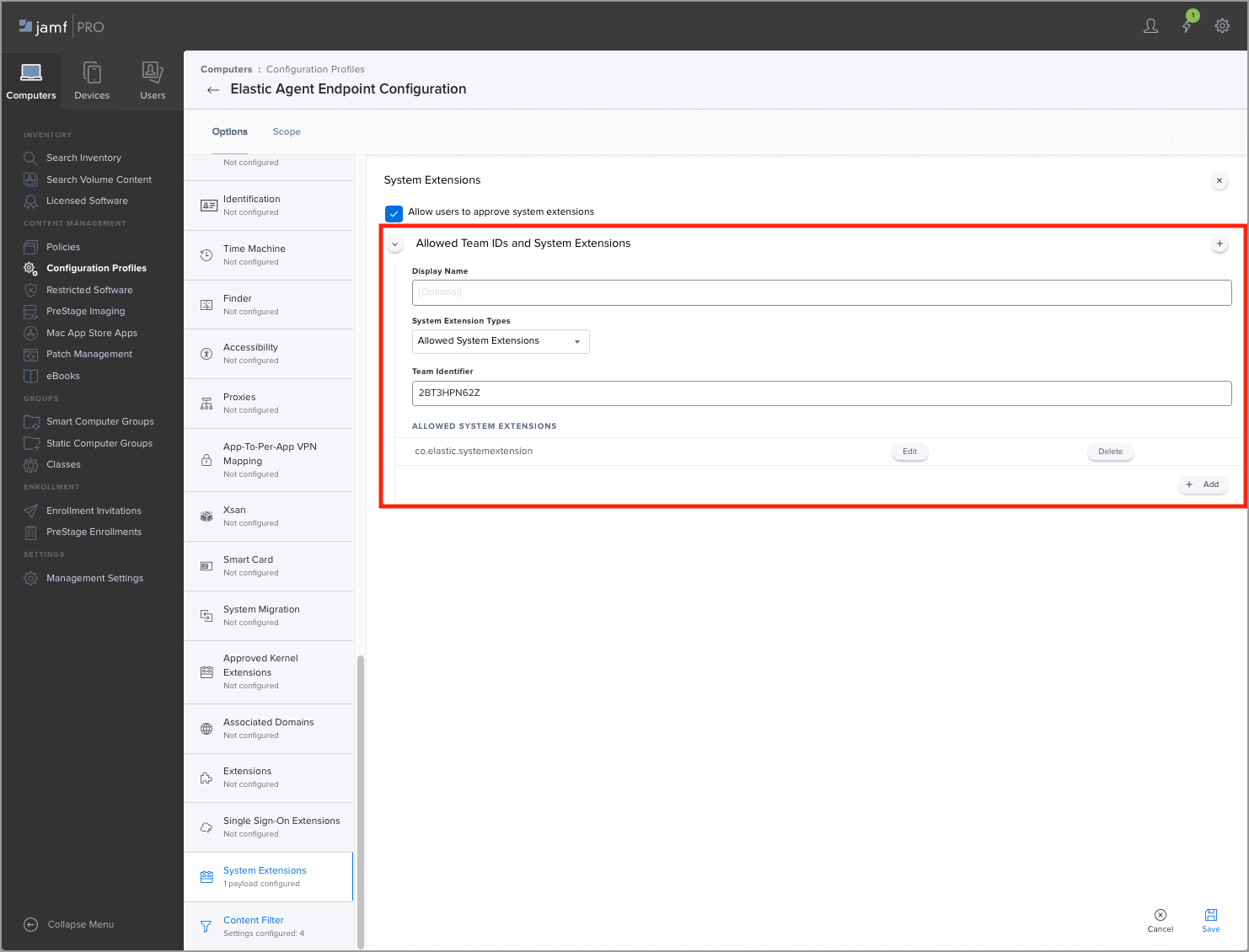
edit- Select the System Extensions option to configure the system extension policy for the Elastic Endpoint configuration profile.
- Make sure that Allow users to approve system extensions is selected.
-
In the Allowed Team IDs and System Extensions section, add the Elastic Endpoint system extension:
- (Optional) Enter a Display Name for the Elastic Endpoint system extension.
- From the System Extension Types dropdown, select Allowed System Extensions.
-
Under Team Identifier, enter
2BT3HPN62Z. -
Under Allowed System Extensions, enter
co.elastic.systemextension.
- Save the configuration.
Approve network content filtering
edit- Select the Content Filter option to configure the Network Extension policy for the Elastic Endpoint configuration profile.
-
Under Filter Name, enter
ElasticEndpoint. -
Under Identifier, enter
co.elastic.endpoint. -
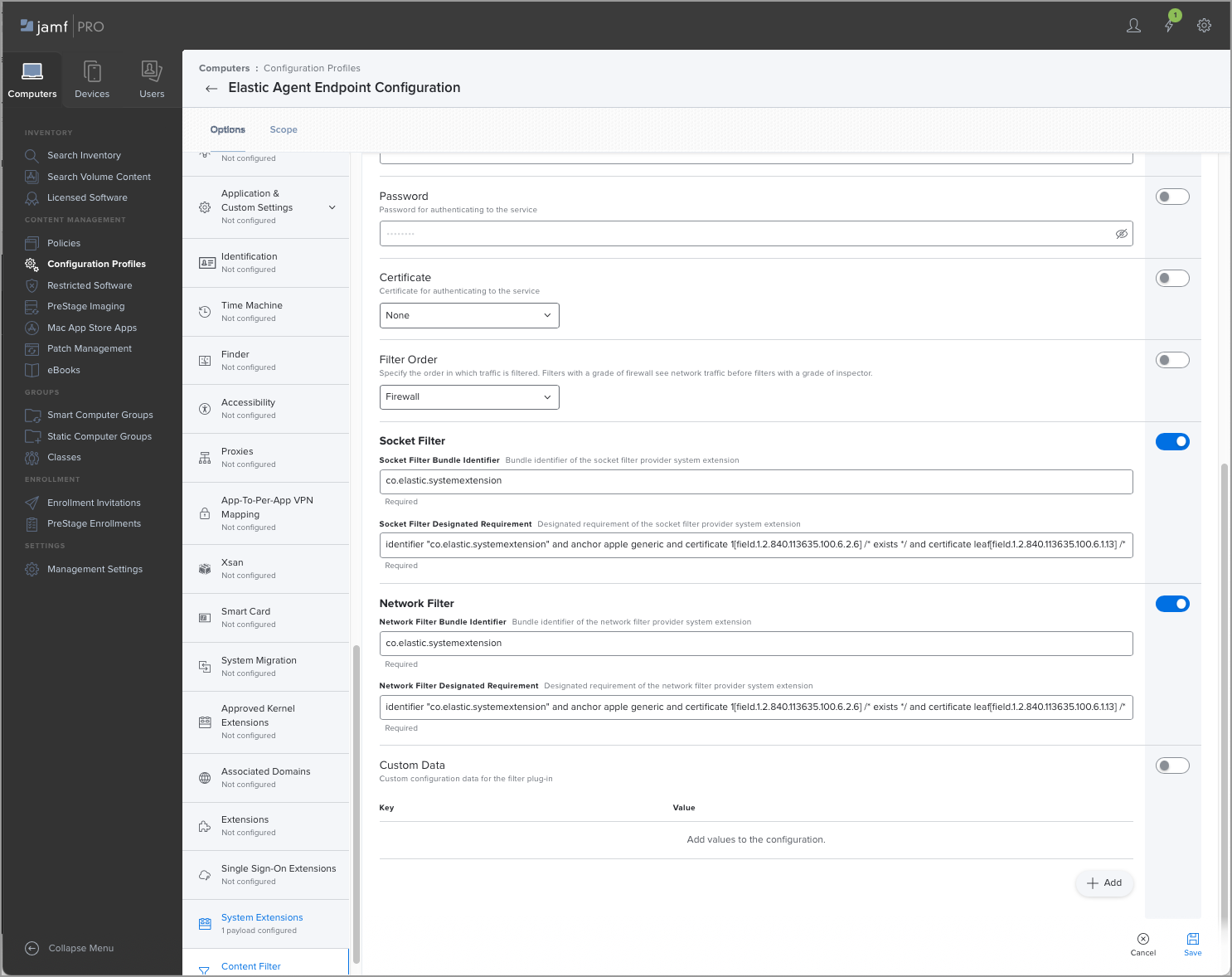
In the Socket Filter section, fill in these fields:
-
Socket Filter Bundle Identifier: Enter
co.elastic.systemextension -
Socket Filter Designated Requirement: Enter the following:
identifier "co.elastic.systemextension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2BT3HPN62Z"
-
Socket Filter Bundle Identifier: Enter
-
In the Network Filter section, fill in these fields:
-
Network Filter Bundle Identifier: Enter
co.elastic.systemextension -
Network Filter Designated Requirement: Enter the following:
identifier "co.elastic.systemextension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2BT3HPN62Z"
-
Network Filter Bundle Identifier: Enter
- Save the configuration.
Enable notifications
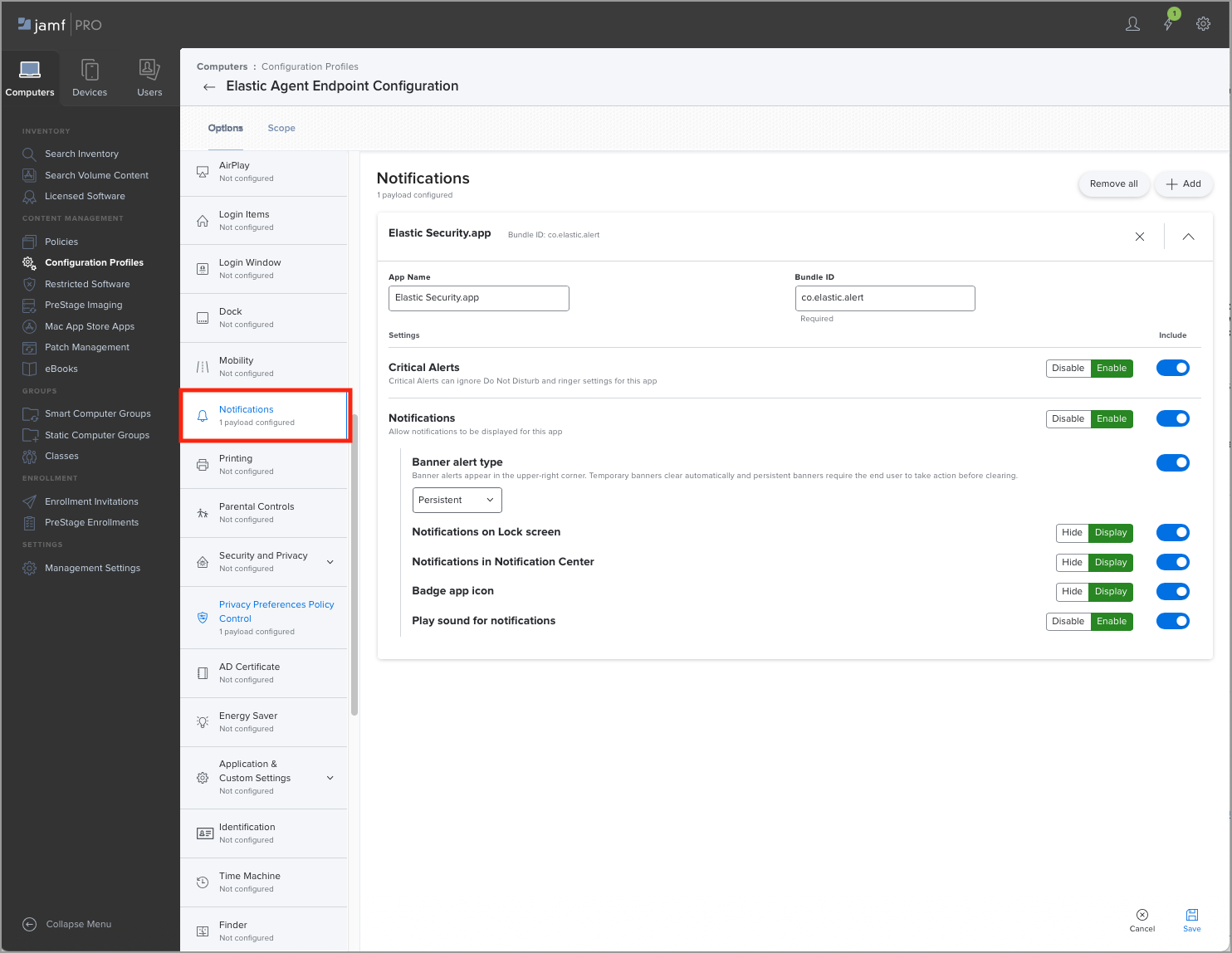
edit- Select the Notifications option to configure the Notification Center policy for the Elastic Endpoint configuration profile.
-
Under App Name, enter
Elastic Security.app. -
Under Bundle ID, enter
co.elastic.alert. -
In the Settings section, include these options with the following settings:
- Critical Alerts: Enable
- Notifications: Enable
- Banner alert type: Persistent
- Notifications on Lock Screen: Display
- Notifications in Notification Center: Display
- Badge app icon: Display
- Play sound for notifications: Enable
- Save the configuration.
Enable Full Disk Access
edit- Select the Privacy Preferences Policy Control option to configure the Full Disk Access policy for the Elastic Endpoint configuration profile.
-
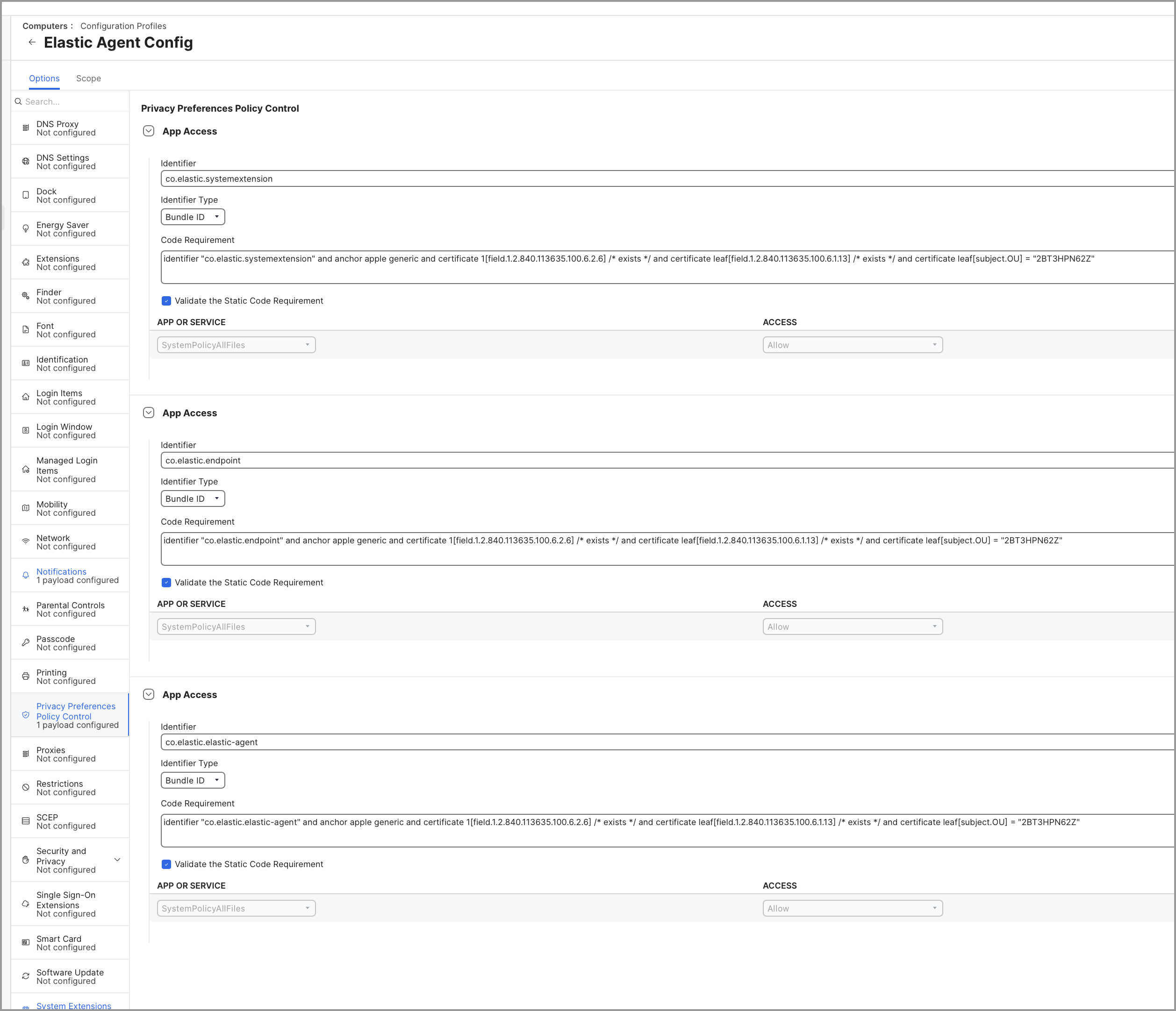
Add a new entry with the following details:
-
Under Identifier, enter
co.elastic.systemextension. - From the Identifier Type dropdown, select Bundle ID.
-
Under Code Requirement, enter the following:
identifier "co.elastic.systemextension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2BT3HPN62Z"
- Make sure that Validate the Static Code Requirement is selected.
-
Under Identifier, enter
-
Add a second entry with the following details:
-
Under Identifier, enter
co.elastic.endpoint. - From the Identifier Type dropdown, select Bundle ID.
-
Under Code Requirement, enter the following:
identifier "co.elastic.endpoint" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2BT3HPN62Z"
- Make sure that Validate the Static Code Requirement is selected.
-
Under Identifier, enter
-
Add a third entry with the following details:
-
Under Identifier, enter
co.elastic.elastic-agent. - From the Identifier Type dropdown, select Bundle ID.
-
Under Code Requirement, enter the following:
identifier "co.elastic.elastic-agent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2BT3HPN62Z"
- Make sure that Validate the Static Code Requirement is selected.
-
Under Identifier, enter
- Save the configuration.
After you complete these steps, generate the mobile configuration profile and install it onto the macOS machines. Once the profile is installed, Elastic Defend can be deployed without the need for user interaction.