Create a detection rule
editCreate a detection rule
editRules run periodically and search for source events, matches, sequences, or machine learning job anomaly results that meet their criteria. When a rule’s criteria are met, a detection alert is created.
You can create the following types of rules:
- Custom query: Query-based rule, which searches the defined indices and creates an alert when one or more documents match the rule’s query.
-
Machine learning: Machine learning rule, which creates an alert when a machine learning job discovers an anomaly above the defined threshold (see Anomaly detection with machine learning).
For machine learning rules, the associated machine learning job must be running. If the machine learning job isn’t running, the rule will:
- Run and create alerts if existing anomaly results with scores above the defined threshold are discovered.
- Issue an error stating the machine learning job was not running when the rule executed.
-
Threshold: Searches the defined indices and creates a detections alert when the number of times the specified field’s value is present and meets the threshold during a single execution. When multiple values meet the threshold, an alert is generated for each value.
For example, if the threshold
fieldissource.ipand itsvalueis10, an alert is generated for every source IP address that appears in at least 10 of the rule’s search results. - Event correlation: Searches the defined indices and creates an alert when results match an Event Query Language (EQL) query.
-
Indicator match: Creates an alert when Elastic Security index field values match field values defined in the specified indicator index patterns. For example, you can create an indicator index for IP addresses and use this index to create an alert whenever an event’s
destination.ipequals a value in the index. Indicator index field mappings should be ECS-compliant. For information on creating Elasticsearch indices and field types, see Index some documents, Create index API, and Field data types. If you have indicators in a standard file format, such as CSV or JSON, you can also use the Machine Learning Data Visualizer to import your indicators into an indicator index. See Explore the data in Kibana and use the Import Data option to import your indicators.You can also use value lists as the indicator match index. See Use value lists with indicator match rules at the end of this topic for more information.
-
New terms: Generates an alert for each new term detected in source documents within a specified time range. You can also detect a combination of up to three new terms (for example, a
host.ipandhost.idthat have never been observed together before).
When modifying rules or managing detection alerts, you can add exceptions that prevent a rule from generating alerts even when its criteria are met. This is useful for reducing noise, such as preventing alerts from trusted processes and internal IP addresses.
You can add exceptions to custom query, machine learning, event correlation, and indicator match rule types.
For both prebuilt and custom rules, you can send notifications when alerts are created. Notifications can be sent via Jira, Microsoft Teams, PagerDuty, Slack, and others, and can be configured when you create or edit a rule.
Creating a new rule requires the following steps:
Additional configuration is required for detection rules using cross-cluster search. Refer to Cross-cluster search and detection rules.
At any step, you can preview the rule before saving it to see what kind of results you can expect.
After you activate a rule, you can check if it is running as expected
using the Monitoring tab on the Rules page. If you see
values in the Gap column, you can Troubleshoot missing alerts.
When a rule fails to run, the Elastic Security app tries to rerun it at its next scheduled run time.
Authorization
editRules, including all background detection and the actions they generate, are authorized using an API key associated with the last user to edit the rule. Upon creating or modifying a rule, an API key is generated for that user, capturing a snapshot of their privileges. The API key is then used to run all background tasks associated with the rule including detection checks and executing actions.
If a rule requires certain privileges to run, such as index privileges, keep in mind that if a user without those privileges updates the rule, the rule will no longer function.
Data views and index patterns
editWhen you create a rule, you must either specify the Elasticsearch index pattens for which you’d like the rule to run, or select a data view as the data source. If you select a data view, you can select runtime fields associated with that data view to create a query for the rule (with the exception of machine learning rules, which do not use queries).
To access data views, ensure you have the required permissions.
Select rule type and scope
edit-
Go to Manage → Rules → Create new rule. The Create new rule page displays.
-
Select the type of rule you want to create, then follow the steps outlined in that section:
Create a machine learning rule
editTo create or edit machine learning rules, you must have the appropriate license or use a
cloud deployment. Additionally, you must have the machine_learning_admin user
role, and the selected machine learning job must be running for the rule to function correctly.
-
To create a rule based on a machine learning anomaly threshold, select Machine Learning, then select:
-
The required machine learning jobs.
If a required job isn’t currently running, it will automatically start when you finish configuring and enable the rule.
- The anomaly score threshold above which alerts are created.
-
- Click Continue to configure basic rule settings.
Create a custom query rule
edit-
To create a rule based on a KQL or Lucene query, select Custom query, then:
- Define which Elasticsearch indices or data view the rule searches for alerts.
-
Use the filter and query fields to create the criteria used for detecting alerts.
The following example (based on the prebuilt rule Volume Shadow Copy Deleted or Resized via VssAdmin) detects when the
vssadmin delete shadowsWindows command is executed:-
Index patterns:
winlogbeat-*Winlogbeat ships Windows event logs to Elastic Security.
-
Custom query:
event.action:"Process Create (rule: ProcessCreate)" and process.name:"vssadmin.exe" and process.args:("delete" and "shadows")Searches the
winlogbeat-*indices forvssadmin.exeexecutions with thedeleteandshadowarguments, which are used to delete a volume’s shadow copies.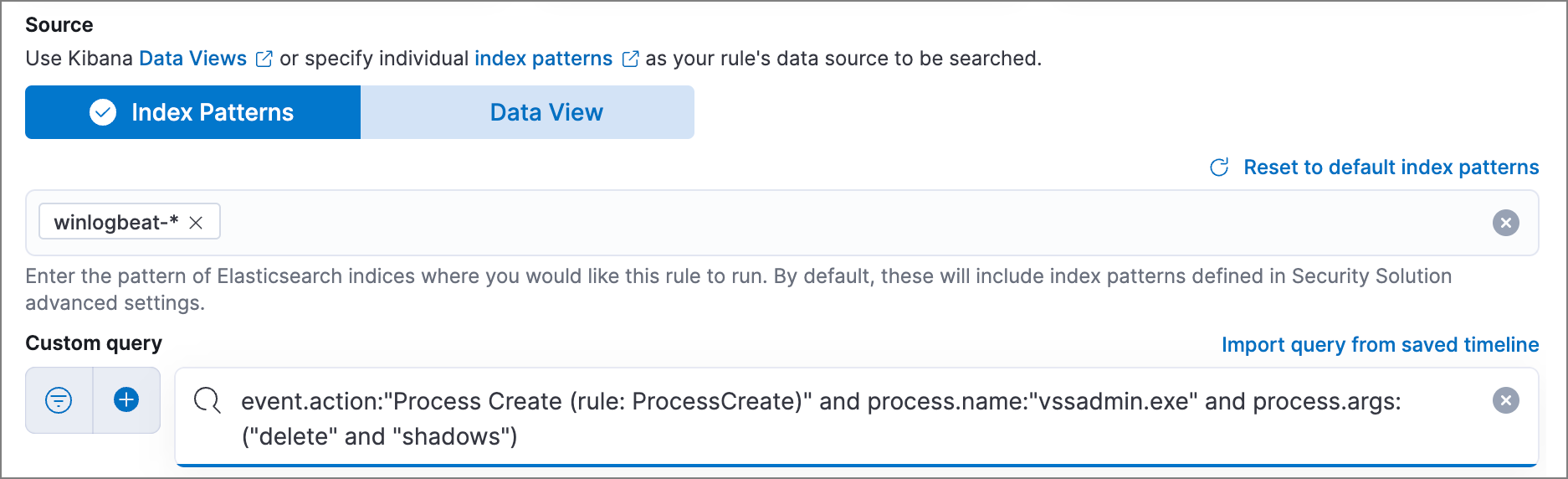
-
-
You can use Kibana saved queries (
 ) and queries from saved Timelines (Import query from saved Timeline) as rule conditions.
) and queries from saved Timelines (Import query from saved Timeline) as rule conditions.When you use a saved query, the Load saved query "query name" dynamically on each rule execution check box appears:
- Select this to use the saved query every time the rule runs. This links the rule to the saved query, and you won’t be able to modify the rule’s Custom query field or filters because the rule will only use settings from the saved query. To make changes, modify the saved query itself.
- Deselect this to load the saved query as a one-time way of populating the rule’s Custom query field and filters. This copies the settings from the saved query to the rule, so you can then further adjust the rule’s query and filters as needed. If the saved query is later changed, the rule will not inherit those changes.
-
[preview] This functionality is in technical preview and may be changed or removed in a future release. Elastic will work to fix any issues, but features in technical preview are not subject to the support SLA of official GA features. (Optional, Platinum or higher subscription required) Use Suppress alerts by to reduce the number of repeated or duplicate alerts created by the rule.
-
Enter a field name to group matching source events by the field’s unique values; only one alert will be created for each group of events. You can also enter multiple fields to group events by unique combinations of values.
If you specify a field with multiple values, an alert grouping is created for each value. For example, if you suppress alerts by
destination.ipof[127.0.0.1, 127.0.0.2, 127.0.0.3], alerts will be suppressed separately for each matching value of127.0.0.1,127.0.0.2, and127.0.0.3. -
Select how often to create alerts for duplicate events:
- Per rule execution: Create an alert each time the rule runs and matches duplicate events.
-
Per time period: Create one alert for all matching events within a specified time window, beginning when the rule first matches an event and creates the alert.
For example, if a rule runs every 5 minutes but you don’t need alerts that frequently, you can set the suppression time period to a longer time, such as 1 hour. If the rule matches an event, it creates an alert at that time, and for the next hour any subsequent matches will be suppressed.
With either option, you can view all events associated with suppressed alerts by investigating the alert in Timeline. Refer to Suppress detection alerts for more information.
-
- Click Continue to configure basic rule settings.
Create a threshold rule
edit-
To create a rule based on a source event field threshold, select Threshold, then:
- Define which Elasticsearch indices the rule analyzes for alerts.
-
Use the filter and query fields to create the criteria used for detecting alerts.
You can use Kibana saved queries (
 ) and queries from saved Timelines (Import query from saved Timeline) as rule conditions.
) and queries from saved Timelines (Import query from saved Timeline) as rule conditions. -
Use the
Group byandThresholdfields to determine which source event field is used as a threshold and the threshold’s value. -
Use the
Countfield to limit alerts by cardinality of a certain field.For example, if
Group byissource.ip,destination.ipand itsThresholdis10, an alert is generated for every pair of source and destination IP addresses that appear in at least 10 of the rule’s search results.You can also leave the
Group byfield undefined. The rule then creates an alert when the number of search results is equal to or greater than the threshold value. If you setCountto limit the results byprocess.name>= 2, an alert will only be generated for source/destination IP pairs that appear with at least 2 unique process names across all events.Alerts created by threshold rules are synthetic alerts that do not resemble the source documents. The alert itself only contains data about the fields that were aggregated over (the
Group byfields). Other fields are omitted, because they can vary across all source documents that were counted toward the threshold. Additionally, you can reference the actual count of documents that exceeded the threshold from thekibana.alert.threshold_result.countfield.
- Click Continue to configure basic rule settings.
Create an event correlation rule
edit-
To create an event correlation rule using EQL, select Event Correlation, then:
-
Define which Elasticsearch indices or data view the rule searches for alerts.
Event correlation rules have a limitation that prevents them from querying multiple indices from different clusters (local and remote). To enable this, a user with the
superuserrole must modify the EQL rules that are configured to use cross-cluster search. This updates the rule’s API key to usesuperuserprivileges and allows the rule to use cross-cluster search. -
Add an EQL statement used to detect alerts.
For example, the following rule detects when
msxsl.exemakes an outbound network connection:-
Index patterns:
winlogbeat-*Winlogbeat ships Windows events to Elastic Security.
-
EQL query:
sequence by process.entity_id [process where event.type in ("start", "process_started") and process.name == "msxsl.exe"] [network where event.type == "connection" and process.name == "msxsl.exe" and network.direction == "outgoing"]Searches the
winlogbeat-*indices for sequences of amsxsl.exeprocess start event followed by an outbound network connection event that was started by themsxsl.exeprocess.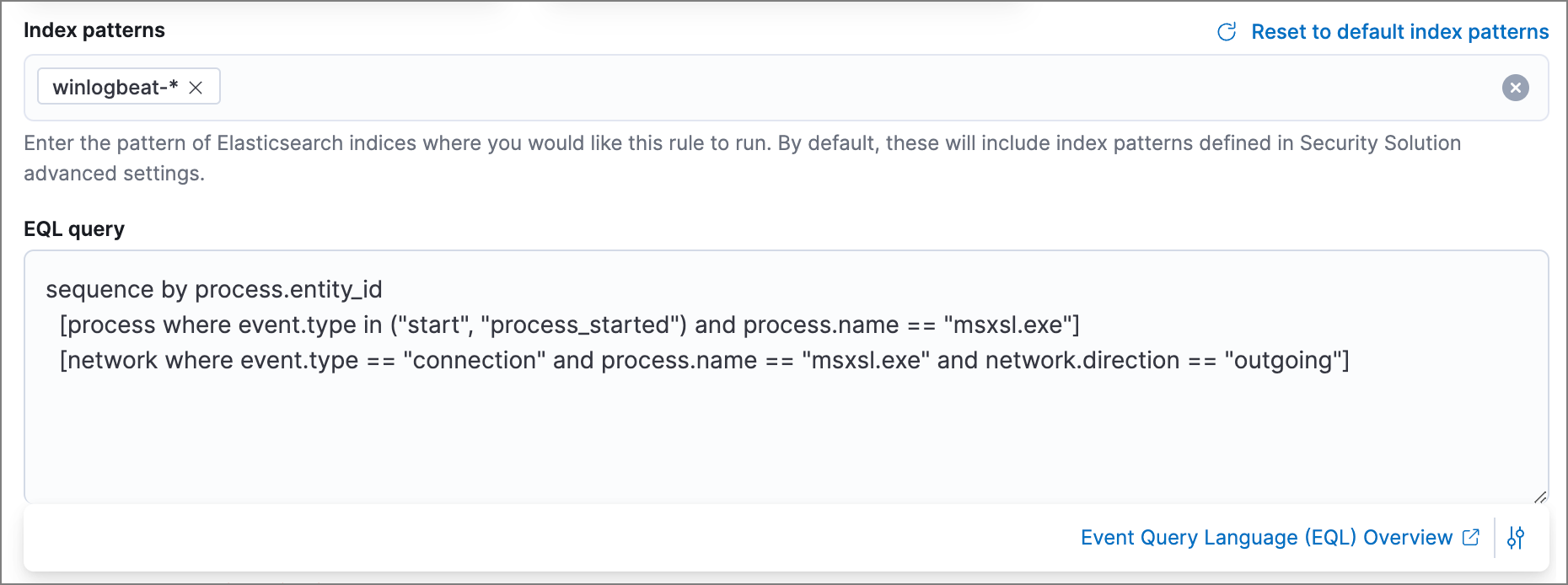
For sequence events, the Elastic Security app generates a single alert when all events listed in the sequence are detected. To see the matched sequence events in more detail, you can view the alert in the Timeline, and, if all events came from the same process, open the alert in Analyze Event view.
-
-
-
(Optional) Click the EQL settings icon (
 ) to configure additional fields used by EQL search:
) to configure additional fields used by EQL search:-
Event category field: Contains the event classification, such as
process,file, ornetwork. This field is typically mapped as a field type in the keyword family. Defaults to theevent.categoryECS field. - Tiebreaker field: Sets a secondary field for sorting events (in ascending, lexicographic order) if they have the same timestamp.
-
Timestamp field: Contains the event timestamp used for sorting a sequence of events. This is different from the Timestamp override advanced setting, which is used for querying events within a range. Defaults to the
@timestampECS field.
-
Event category field: Contains the event classification, such as
- Click Continue to configure basic rule settings.
Create an indicator match rule
editElastic Security provides limited support for indicator match rules. See Limited support for indicator match rules for more information.
-
To create a rule that searches for events whose specified field value matches the specified indicator field value in the indicator index patterns, select Indicator Match, then fill in the following fields:
- Source: The individual index patterns or data view that specifies what data to search.
-
Custom query: The query and filters used to retrieve the required results from the Elastic Security event indices. For example, if you want to match documents that only contain a
destination.ipaddress field, adddestination.ip : *.If you want the rule to check every field in the indices, use this wildcard expression:
*:*.You can use Kibana saved queries (
 ) and queries from saved Timelines (Import query from saved Timeline) as rule conditions.
) and queries from saved Timelines (Import query from saved Timeline) as rule conditions. -
Indicator index patterns: The indicator index patterns containing field values for which you want to generate alerts. This field is automatically populated with indices specified in the
securitySolution:defaultThreatIndexadvanced setting. For more information, see Update default Elastic Security threat intelligence indices.Data in indicator indices must be ECS compatible, and so it must contain a
@timestampfield. -
Indicator index query: The query and filters used to filter the fields from
the indicator index patterns. The default query
@timestamp > "now-30d/d"searches specified indicator indices for indicators ingested during the past 30 days and rounds the start time down to the nearest day (resolves to UTC00:00:00). -
Indicator mapping: Compares the values of the specified event and indicator fields, and generates an alert if the values are identical.
Only single-value fields are supported.
To define which field values are compared from the indices add the following:
- Field: The field used for comparing values in the Elastic Security event indices.
- Indicator index field: The field used for comparing values in the indicator indices.
-
You can add
ANDandORclauses to define when alerts are generated.For example, to create a rule that generates alerts when
host.nameanddestination.ipfield values in thelogs-*orpacketbeat-*Elastic Security indices are identical to the corresponding field values in themock-threat-listindicator index, enter the rule parameters seen in the following image: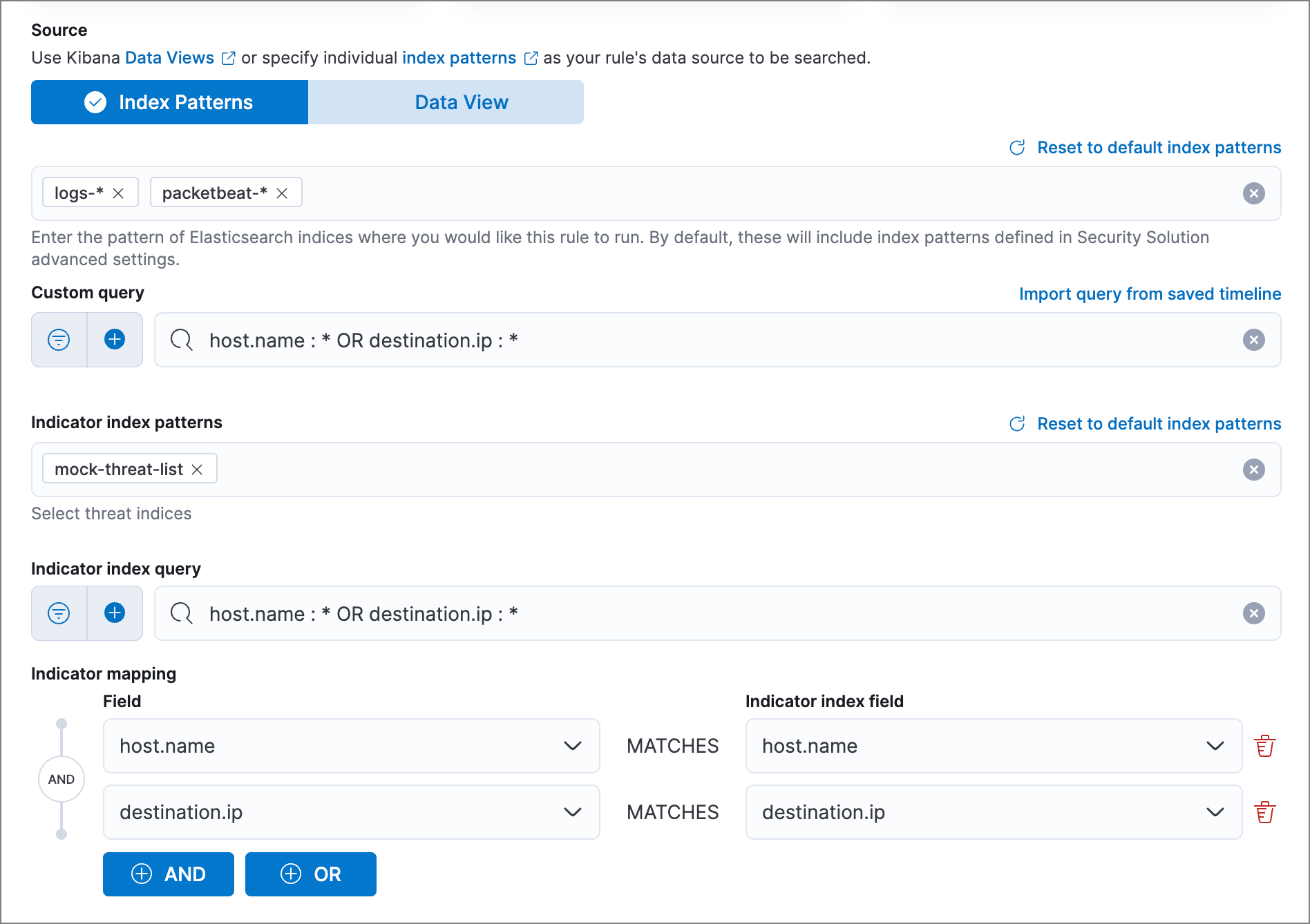
Before you create rules, create Timeline templates so they can be selected here. When alerts generated by the rule are investigated in the Timeline, Timeline query values are replaced with their corresponding alert field values.
- Click Continue to configure basic rule settings.
Create a new terms rule
edit-
To create a rule that searches for each new term detected in source documents, select New Terms, then:
- Specify what data to search by entering individual Elasticsearch index patterns or selecting an existing data view.
-
Use the filter and query fields to create the criteria used for detecting alerts.
You can use Kibana saved queries (
 ) and queries from saved Timelines (Import query from saved Timeline) as rule conditions.
) and queries from saved Timelines (Import query from saved Timeline) as rule conditions. -
Use the Fields menu to select a field to check for new terms. You can also select up to three fields to detect a combination of new terms (for example, a
host.ipandhost.idthat have never been observed together before).When checking multiple fields, each unique combination of values from those fields is evaluated separately. For example, a document with
host.name: ["host-1", "host-2", "host-3"]anduser.name: ["user-1", "user-2", "user-3"]has 9 (3x3) unique combinations ofhost.nameanduser.name. A document with 11 values inhost.nameand 10 values inuser.namehas 110 (11x10) unique combinations. The new terms rule only evaluates 100 unique combinations per document, so selecting fields with large arrays of values might cause incorrect results. -
Use the History Window Size menu to specify the time range to search in minutes, hours, or days to determine if a term is new. The history window size must be larger than the rule interval plus additional look-back time, because the rule will look for terms where the only time(s) the term appears within the history window is also within the rule interval and additional look-back time.
For example, if a rule has an interval of 5 minutes, no additional look-back time, and a history window size of 7 days, a term will be considered new only if the time it appears within the last 7 days is also within the last 5 minutes. Configure the rule interval and additional look-back time when you set the rule’s schedule.
- Click Continue to configure basic rule settings.
Preview your rule (optional)
editYou can preview any custom or prebuilt rule to find out how noisy it will be. For a custom rule, you can then adjust the rule’s query or other settings.
To preview rules, you need the read privilege for the .preview.alerts-security.alerts-<space-id> and .internal.preview.alerts-security.alerts-<space-id>-* indices, plus All privileges for the Security feature. Refer to Detections prerequisites and requirements for more information.
Click the Rule preview button while creating or editing a rule. The preview opens in a side panel, showing a histogram and table with the alerts you can expect, based on the defined rule settings and past events in your indices.
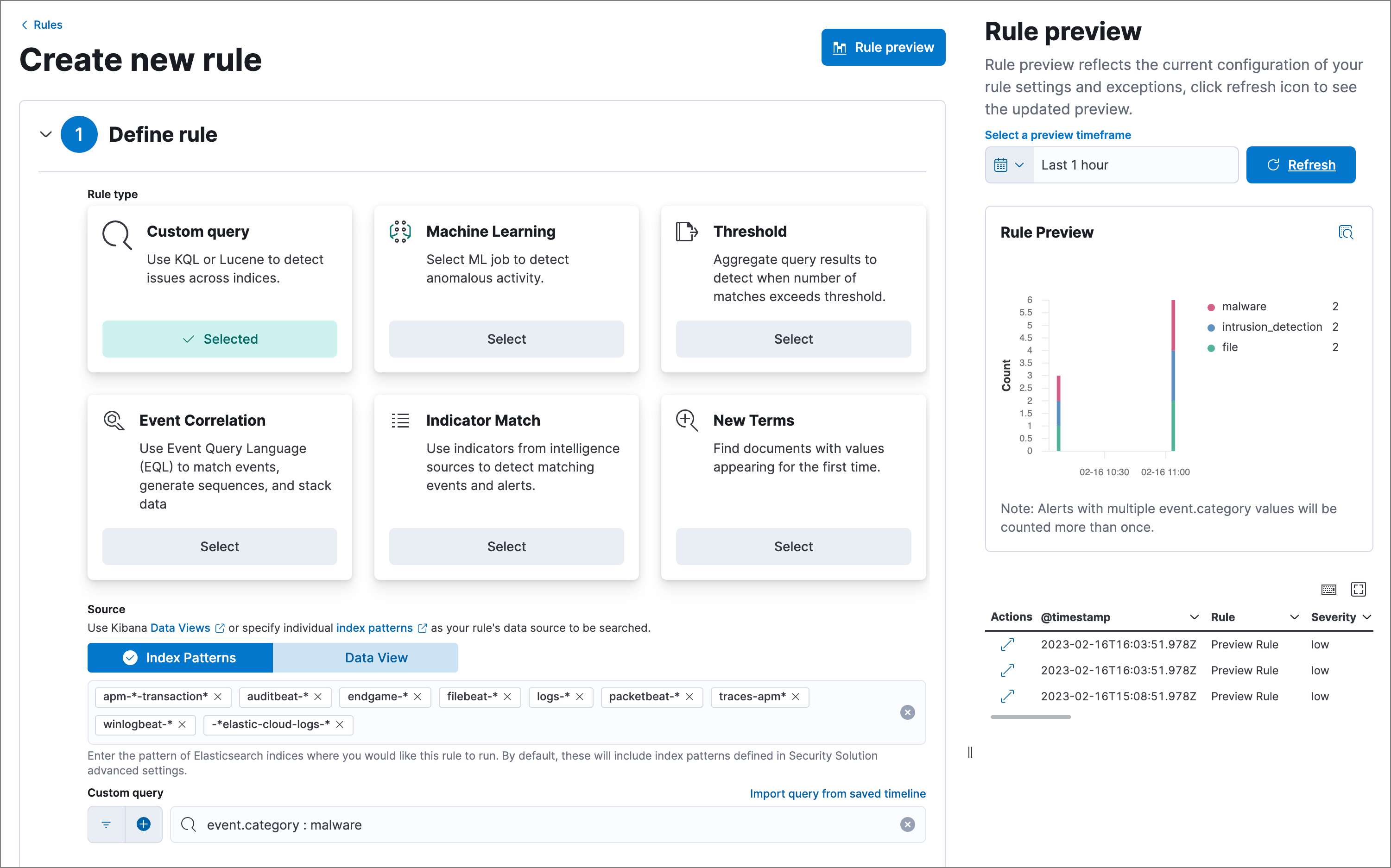
The preview also includes the effects of rule exceptions and override fields. In the histogram, alerts are stacked by event.category (or host.name for machine learning rules), and alerts with multiple values are counted more than once.
To interact with the rule preview:
-
Use the date and time picker to define the preview’s time range.
Avoid setting long time ranges with short rule intervals, or the rule preview might time out.
-
Click Refresh to update the preview.
-
When you edit the rule’s settings or the preview’s time range, the button changes from blue (
 ) to green (
) to green ( ) to indicate that the rule has been edited since the last preview.
) to indicate that the rule has been edited since the last preview.
-
For a relative time range (such as
Last 1 hour), refresh the preview to check for the latest results. (Previews don’t automatically refresh with new incoming data.)
-
When you edit the rule’s settings or the preview’s time range, the button changes from blue (
-
Click the View details icon (
 ) in the alerts table to view the details of a particular alert.
) in the alerts table to view the details of a particular alert.
-
To resize the preview, hover between the rule settings and preview, then click and drag the border. You can also click the border, then the collapse icon (
 ) to collapse and expand the preview.
) to collapse and expand the preview.
- To close the preview, click the Rule preview button again.
Configure basic rule settings
edit-
In the About rule pane, fill in the following fields:
- Name: The rule’s name.
- Description: A description of what the rule does.
-
Default severity: Select the severity level of alerts created by the rule:
- Low: Alerts that are of interest but generally are not considered to be security incidents. Sometimes a combination of low severity alerts can indicate suspicious activity.
- Medium: Alerts that require investigation.
- High: Alerts that require an immediate investigation.
- Critical: Alerts that indicate it is highly likely a security incident has occurred.
-
Severity override (optional): Select to use source event values to override the Default severity in generated alerts. When selected, a UI component is displayed where you can map the source event field values to severity levels. The following example shows how to map severity levels to
host.namevalues: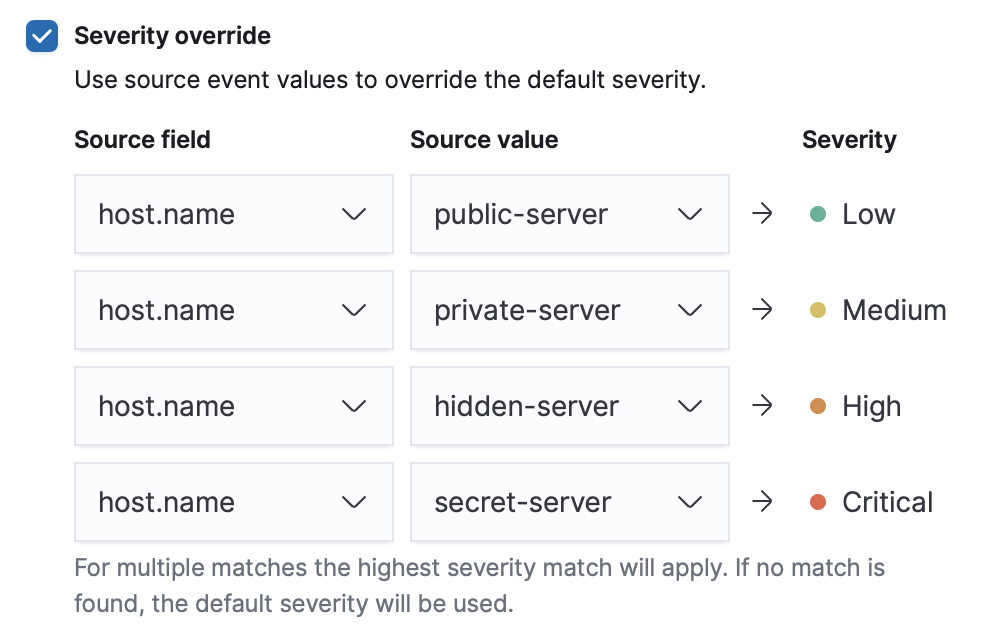
For threshold rules, not all source event values can be used for overrides; only the fields that were aggregated over (the
Group byfields) will contain data. Please also note that overrides are not supported for event correlation rules. -
Default risk score: A numerical value between 0 and 100 that indicates the risk of events detected by the rule. This setting changes to a default value when you change the Severity level, but you can adjust the risk score as needed. General guidelines are:
-
0-21represents low severity. -
22-47represents medium severity. -
48-73represents high severity. -
74-100represents critical severity.
-
-
Risk score override (optional): Select to use a source event value to override the Default risk score in generated alerts. When selected, a UI component is displayed to select the source field used for the risk score. For example, if you want to use the source event’s risk score in alerts:

For threshold rules, not all source event values can be used for overrides; only the fields that were aggregated over (the
Group byfields) will contain data. - Tags (optional): Words and phrases used to categorize, filter, and search the rule.
-
Continue with one of the following:
Configure advanced rule settings (optional)
edit-
Click Advanced settings and fill in the following fields where applicable:
- Reference URLs (optional): References to information that is relevant to the rule. For example, links to background information.
- False positive examples (optional): List of common scenarios that may produce false-positive alerts.
- MITRE ATT&CKTM threats (optional): Add relevant MITRE framework tactics, techniques, and subtechniques.
- Investigation guide (optional): Information for analysts investigating alerts created by the rule. You can also add action buttons to run Osquery or launch Timeline investigations using alert data.
- Author (optional): The rule’s authors.
- License (optional): The rule’s license.
-
Elastic endpoint exceptions (optional): Adds all Elastic Endpoint Security rule exceptions to this rule (refer to Add Elastic Endpoint exceptions to learn more about adding endpoint exceptions).
If you select this option, you can add Endpoint exceptions on the Rule details page. Additionally, all future exceptions added to the Endpoint Security rule also affect this rule.
- Building block (optional): Select to create a building-block rule. By default, alerts generated from a building-block rule are not displayed in the UI. See About building block rules for more information.
-
Indicator prefix override: Define the location of indicator data within the structure of indicator documents. When the indicator match rule executes, it queries specified indicator indices and references this setting to locate fields with indicator data. This data is used to enrich indicator match alerts with metadata about matched threat indicators. The default value for this setting is
threat.indicator.If your threat indicator data is at a different location, update this setting accordingly to ensure alert enrichment can still be performed.
-
Rule name override (optional): Select a source event field to use as the rule name in the UI (Alerts table). This is useful for exposing, at a glance, more information about an alert. For example, if the rule generates alerts from Suricata, selecting
event.actionlets you see what action (Suricata category) caused the event directly in the Alerts table.For threshold rules, not all source event values can be used for overrides; only the fields that were aggregated over (the
Group byfields) will contain data. -
Timestamp override (optional): Select a source event timestamp field. When selected, the rule’s query uses the selected field, instead of the default
@timestampfield, to search for alerts. This can help reduce missing alerts due to network or server outages. Specifically, if your ingest pipeline adds a timestamp when events are sent to Elasticsearch, this avoids missing alerts due to ingestion delays. However, if you know your data source has an inaccurate@timestampvalue, it is recommended you select the Do not use @timestamp as a fallback timestamp field option to ignore the@timestampfield entirely.The Microsoft and Google Workspace Filebeat modules have an
event.ingestedtimestamp field that can be used instead of the default@timestampfield.
-
Click Continue. The Schedule rule pane is displayed.
- Continue with setting the rule’s schedule.
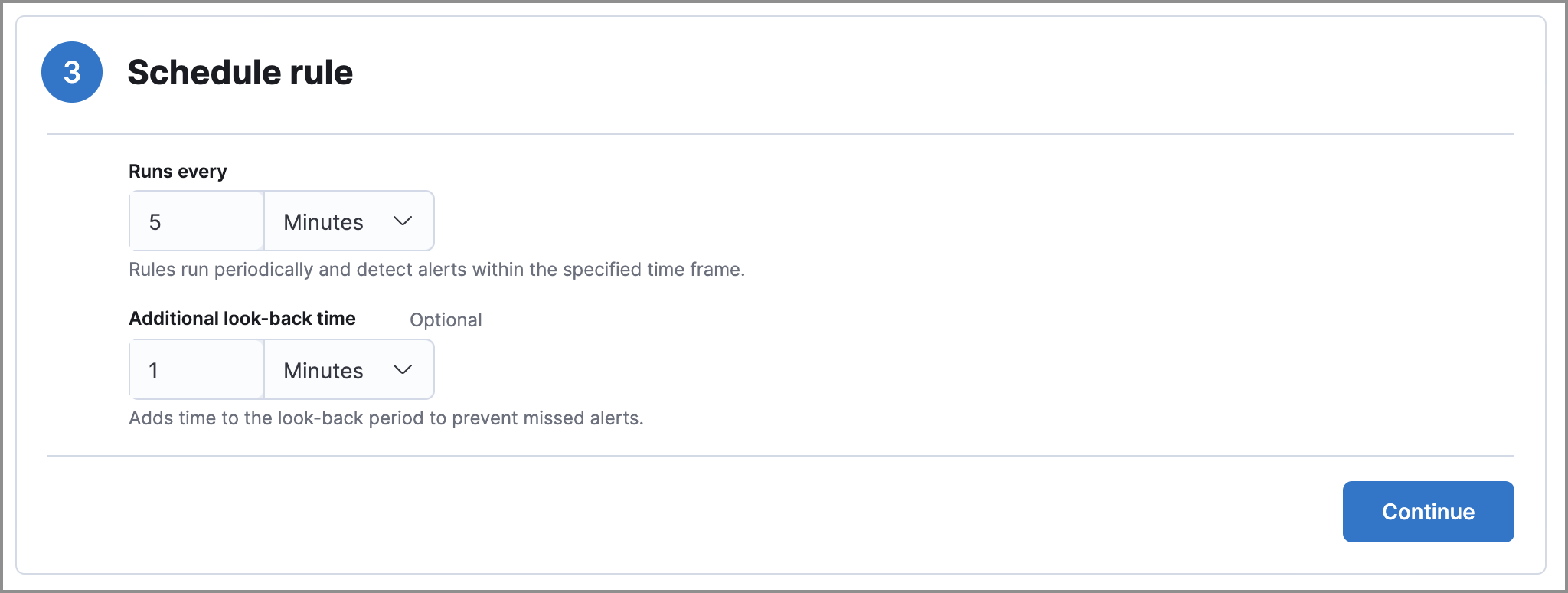
Set the rule’s schedule
edit- Select how often the rule runs.
-
Optionally, add
Additional look-back timeto the rule. When defined, the rule searches indices with the additional time.For example, if you set a rule to run every 5 minutes with an additional look-back time of 1 minute, the rule runs every 5 minutes but analyzes the documents added to indices during the last 6 minutes.
It is recommended to set the
Additional look-back timeto at least 1 minute. This ensures there are no missing alerts when a rule does not run exactly at its scheduled time.Elastic Security prevents duplication. Any duplicate alerts that are discovered during the
Additional look-back timeare not created. -
Click Continue. The Rule actions pane is displayed.
-
Do either of the following:
- Continue onto setting up alert notifications and Response Actions (optional).
- Create the rule (with or without activation).
Set up alert notifications (optional)
editUse Kibana Actions to set up notifications sent via other systems when alerts are generated.
To use Kibana Actions for alert notifications, you need the appropriate license and your role needs All privileges for the Action and Connectors feature. For more information, see Cases prerequisites.
-
Select a connector type to determine how notifications are sent. For example, if you select the Jira connector, notifications are sent to your Jira system.
Each action type requires a connector. Connectors store the information required to send the notification from the external system. You can configure connectors while creating the rule or in Stack Management → Connectors. For more information, see Action and connector types.

-
After you select a connector, set its action frequency to define when notifications are sent:
-
Summary of alerts: Select this option to get a report that summarizes generated alerts, which you can review at your convenience. Alert summaries will be sent at the specified time intervals.
When setting a custom notification frequency, do not choose a time that is shorter than the rule’s execution schedule.
- For each alert: Select this option to ensure notifications are sent every time new alerts are generated.
-
-
(Optional) Specify additional conditions that need to be met for notifications to send. Click the toggle to enable a setting, then add the required details:
- If alert matches query: Enter a KQL query that defines field-value pairs or query conditions that must be met for notifications to send. The query only searches alert documents in the indices specified for the rule.
- If alert is generated during timeframe: Set timeframe details. Notifications are only sent if alerts are generated within the timeframe you define.
-
Complete the required connector type fields. Here is an example with Jira:
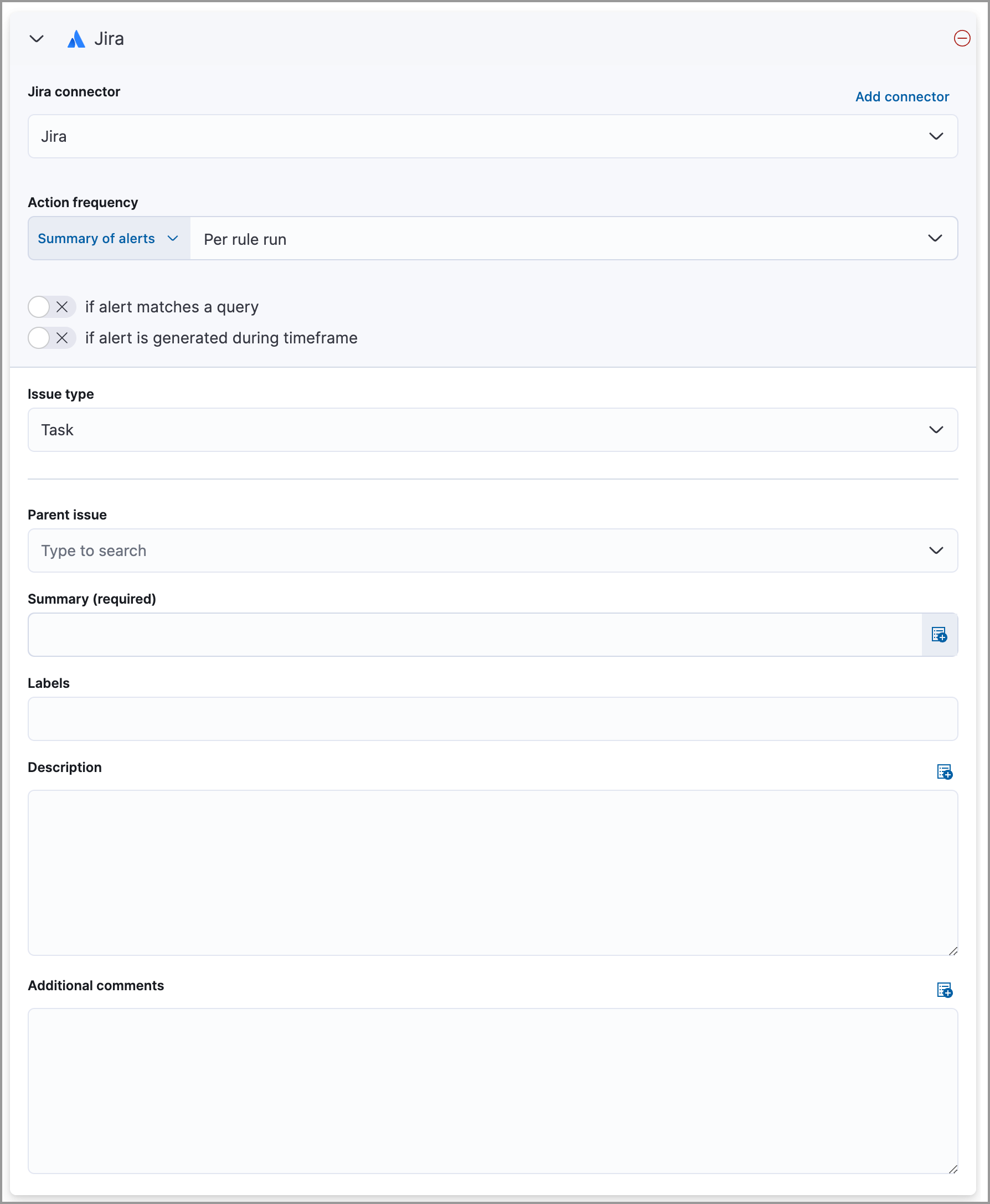
- Use the default notification message or customize it. You can add more context to the message by clicking the icon above the message text box and selecting from a list of available alert notification variables.
-
Create the rule with or without activation.
When you activate a rule, it is queued, and its schedule is determined by its initial run time. For example, if you activate a rule that runs every 5 minutes at 14:03 but it does not run until 14:04, it will run again at 14:09.
Alert notification placeholders
editYou can use mustache syntax to add variables to notification messages. The action frequency you choose determines the variables you can select from.
The following variables can be passed for all rules:
Refer to Action frequency: Summary of alerts to learn about additional variables that can be passed if the rule’s action frequency is Summary of alerts.
-
{{context.alerts}}: Array of detected alerts -
{{{context.results_link}}}: URL to the alerts in Kibana -
{{context.rule.anomaly_threshold}}: Anomaly threshold score above which alerts are generated (machine learning rules only) -
{{context.rule.description}}: Rule description -
{{context.rule.false_positives}}: Rule false positives -
{{context.rule.filters}}: Rule filters (query rules only) -
{{context.rule.id}}: Unique rule ID returned after creating the rule -
{{context.rule.index}}: Indices rule runs on (query rules only) -
{{context.rule.language}}: Rule query language (query rules only) -
{{context.rule.machine_learning_job_id}}: ID of associated machine learning job (machine learning rules only) -
{{context.rule.max_signals}}: Maximum allowed number of alerts per rule execution -
{{context.rule.name}}: Rule name -
{{context.rule.query}}: Rule query (query rules only) -
{{context.rule.references}}: Rule references -
{{context.rule.risk_score}}: Default rule risk scoreThis placeholder contains the rule’s default values even when the Risk score override option is used.
-
{{context.rule.rule_id}}: Generated or user-defined rule ID that can be used as an identifier across systems -
{{context.rule.saved_id}}: Saved search ID -
{{context.rule.severity}}: Default rule severityThis placeholder contains the rule’s default values even when the Severity override option is used.
-
{{context.rule.threat}}: Rule threat framework -
{{context.rule.threshold}}: Rule threshold values (threshold rules only) -
{{context.rule.timeline_id}}: Associated Timeline ID -
{{context.rule.timeline_title}}: Associated Timeline name -
{{context.rule.type}}: Rule type -
{{context.rule.version}}: Rule version -
{{date}}`: Date the rule scheduled the action -
{{kibanaBaseUrl}}: Configuredserver.publicBaseUrlvalue, or empty string if not configured -
{{rule.id}}: ID of the rule -
{{rule.name}}: Name of the rule -
{{rule.spaceId}}: Space ID of the rule -
{{rule.tags}}: Tags of the rule -
{{rule.type}}: Type of rule -
{{state.signals_count}}: Number of alerts detected
The following variables can only be passed if the rule’s action frequency is for each alert:
-
{{alert.actionGroup}}: Action group of the alert that scheduled actions for the rule -
{{alert.actionGroupName}}: Human-readable name of the action group of the alert that scheduled actions for the rule -
{{alert.actionSubgroup}}: Action subgroup of the alert that scheduled actions for the rule -
{{alert.id}}: ID of the alert that scheduled actions for the rule -
{{alert.flapping}}: A flag on the alert that indicates whether the alert status is changing repeatedly
Alert placeholder examples
editTo understand which fields to parse, see the Detections API to view the JSON representation of rules.
Example using {{context.rule.filters}} to output a list of filters:
{{#context.rule.filters}}
{{^meta.disabled}}{{meta.key}} {{#meta.negate}}NOT {{/meta.negate}}{{meta.type}} {{^exists}}{{meta.value}}{{meta.params.query}}{{/exists}}{{/meta.disabled}}
{{/context.rule.filters}}
Example using {{context.alerts}} as an array, which contains each alert generated since the last time the action was executed:
{{#context.alerts}}
Detection alert for user: {{user.name}}
{{/context.alerts}}
Example using the mustache "current element" notation {{.}} to output all the rule references in the signal.rule.references array:
{{#signal.rule.references}} {{.}} {{/signal.rule.references}}
Set up response actions (optional)
editUse Response Actions to set up additional functionality that will run whenever a rule executes.
This functionality is in technical preview and may be changed or removed in a future release. Elastic will work to fix any issues, but features in technical preview are not subject to the support SLA of official GA features.
The Osquery Response Action allows you to include live Osquery queries with a custom query rule. When an alert is generated, Osquery automatically collects data on the system related to the alert. Refer to Add Osquery Response Actions to learn more.

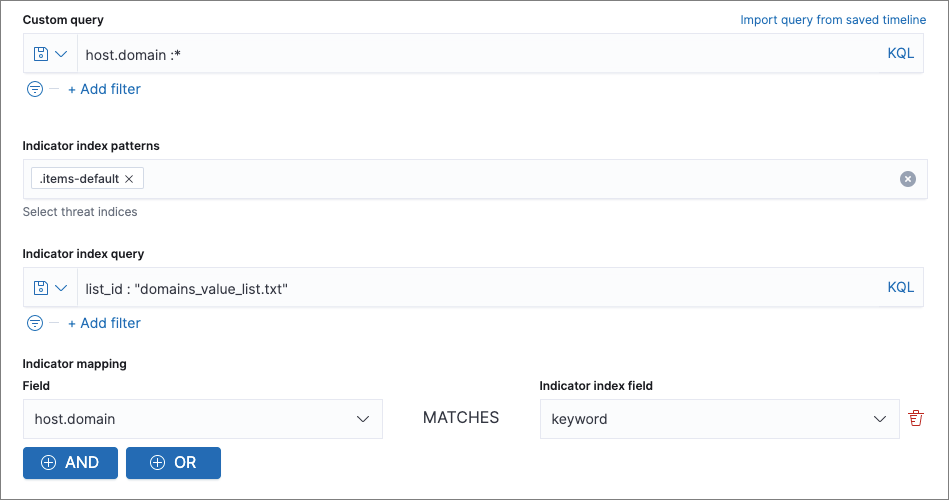
Use value lists with indicator match rules
editWhile there are numerous ways you can add data into indicator indices, you can use value lists as the indicator match index in an indicator match rule. Take the following scenario, for example:
You uploaded a value list of known ransomware domains, and you want to be notified if any of those domains matches a value contained in a domain field in your security event index pattern.
- Upload a value list of indicators.
-
Create an indicator match rule and fill in the following fields:
- Index patterns: The Elastic Security event indices on which the rule runs.
-
Custom query: The query and filters used to retrieve the required results from the Elastic Security event indices (e.g.,
host.domain :*). -
Indicator index patterns: Value lists are stored in a hidden index called
.items-<Kibana space>. Enter the name of the Kibana space in which this rule will run in this field. -
Indicator index query: Enter the value
list_id :, followed by the name of the value list you want to use as your indicator index (uploaded in Step 1 above). -
Indicator mapping
- Field: Enter the field from the Elastic Security event indices to be used for comparing values.
-
Indicator index field: Enter the type of value list you created (i.e.,
keyword,text, orIP).If you don’t remember this information, go to Manage → Rules → Import value lists. Locate the appropriate value list and note the field in the corresponding
Typecolumn. (Examples include keyword, text, and IP.)