User risk score
editUser risk score
editThis page refers to the original user and host risk score modules. If you have the original modules installed, and you’re running Elastic Stack version 8.11 or newer, you can upgrade to the latest risk scoring engine. For information about the latest risk engine, refer to Entity risk scoring.
This feature is available for Elastic Stack versions 8.3.0 and newer and requires a Platinum subscription or higher.
The user risk score feature highlights risky usernames in your environment. It utilizes a transform with a scripted metric aggregation to calculate user risk scores based on alerts generated within the past 90 days. The transform runs hourly to update scores as new alerts are generated.
Each alert’s contribution to the user risk score is based on the alert’s risk score (signal.rule.risk_score). The risk score is calculated using a weighted sum where rules with higher time-corrected risk scores also have higher weights. Each risk score is normalized on a scale of 0 to 100.
The following table shows how risk levels are applied to a username, based on the normalized risk score:
| Risk level | User risk score |
|---|---|
Unknown |
< 20 |
Low |
20-40 |
Moderate |
40-70 |
High |
70-90 |
Critical |
> 90 |
Enable user risk score
editYou can enable user risk score from the following places in the Elastic Security app:
- The Entity Analytics dashboard
- The User risk tab on the Users page
- The User risk tab on a user’s details page
Or, in Kibana, you can enable user risk score in Console.
To enable user risk score from the Entity Analytics dashboard:
- In the Elastic Security app, go to Dashboards → Entity Analytics.
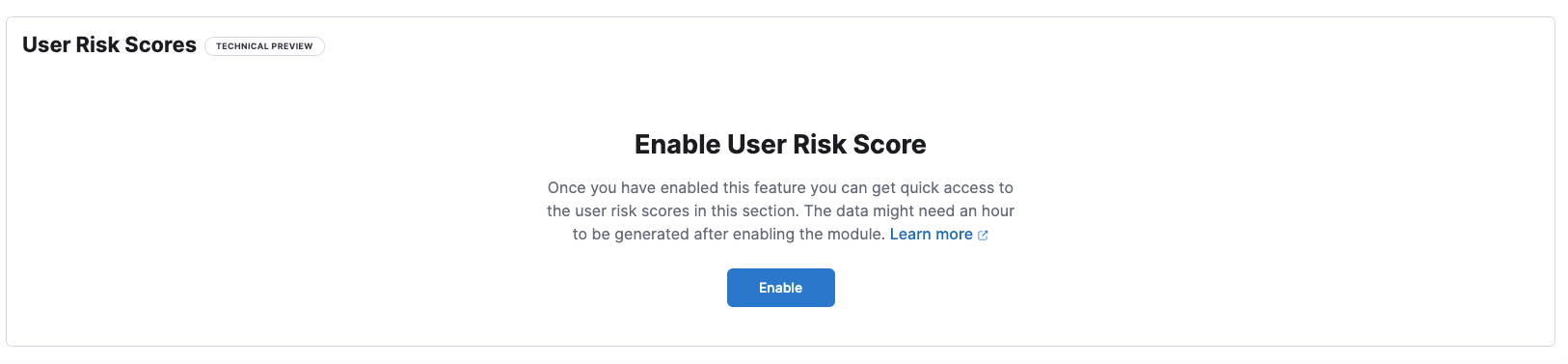
- In the User Risk Scores section, click Enable to install the module.
To enable user risk score from the Users page:
- Go to Explore → Users.
- Select the User risk tab, then click Enable to install the module.
To enable user risk score from a user’s details page:
- Go to Explore → Users.
- Select the All users tab, then click a user name.
- On the details page, scroll down to the data tables, then select the User risk tab.
- Click Enable to install the module.
To enable user risk score from Console in Kibana, open a browser window and enter the following URL:
{KibanaURL}/s/{spaceID}/app/dev_tools#/console?load_from={KibanaURL}/s/{spaceID}/internal/risk_score/prebuilt_content/dev_tool/enable_user_risk_score
If there’s existing content in Console, scroll to the bottom to find the output loaded.
If you receive an error message during the installation process, delete the user risk score module manually, and then re-enable it. Refer to Troubleshooting for more information.
Upgrade user risk score
editIf you previously enabled user risk score and you’re upgrading to Elastic Stack version 8.11 or newer, you can upgrade to the latest risk scoring engine.
Before upgrading, note the following:
-
Since older data is not preserved, previous user risk scores will be deleted, and new scores will be created. However, if you want to retain old user risk scores, you can reindex them before upgrading. To learn how, refer to Reindex API. New data will be stored in the
ml_user_risk_score_<space-id>andml_user_risk_score_latest_<space-id>indices. -
You must edit your Kibana user settings and remove the
xpack.securitySolution.enableExperimental:['riskyUsersEnabled']feature flag.
After this is done, you can proceed with upgrading the user risk score feature from any of the following places in the Elastic Security app:
- The Entity Analytics dashboard
- The User risk tab on the User page
- The User risk tab on a user’s details page
After you enable or upgrade user risk score, you might get a message that says, "No user risk score data available to display." To verify that the transform that installs the user risk score module is picking up data, refer to Verify that user risk score data installed successfully.
If you receive an error message during the installation process, delete the user risk score module manually, and then re-enable it. Refer to Troubleshooting for more information.
Analyze user risk score data
editIt is recommended you analyze users with the highest risk scores first — those in the Critical and Moderate categories. User risk score data appears in the following places in the Elastic Security app:
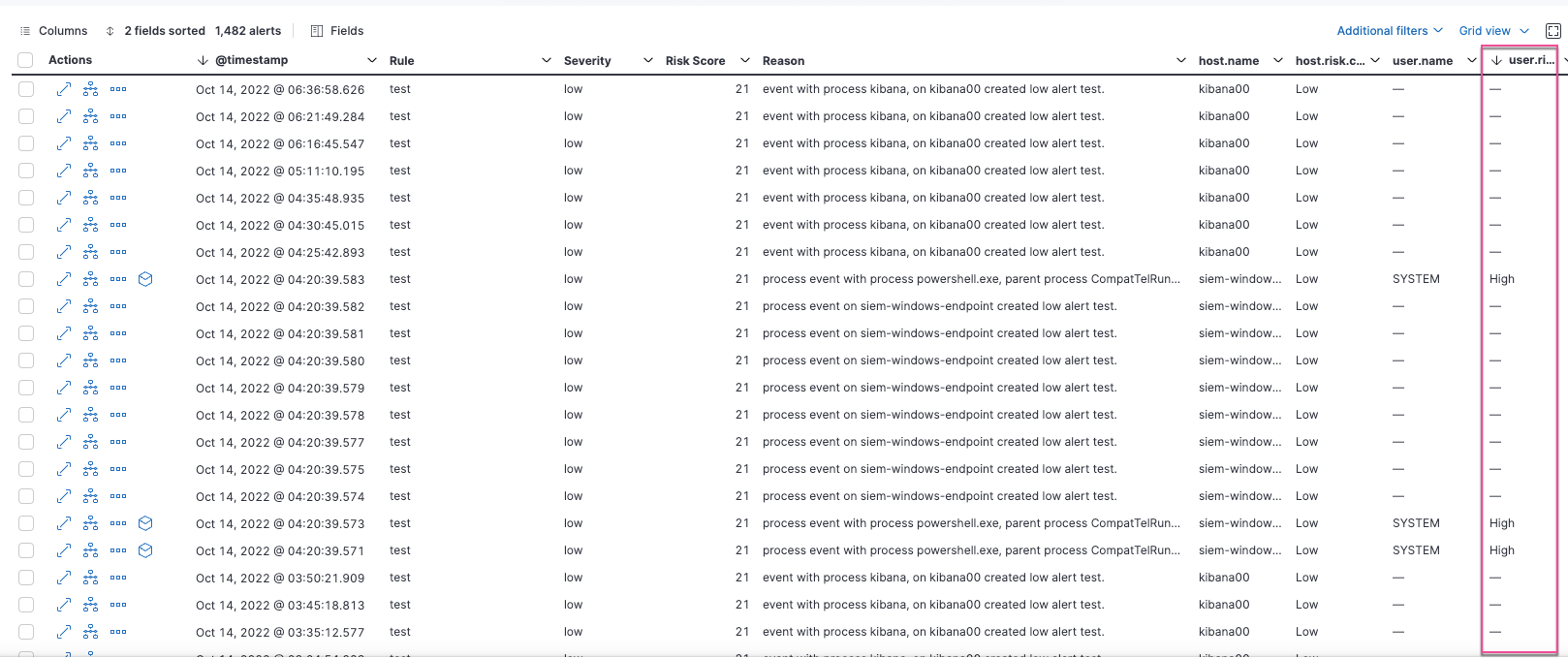
The user.risk.calculated_level column in the Alerts table:
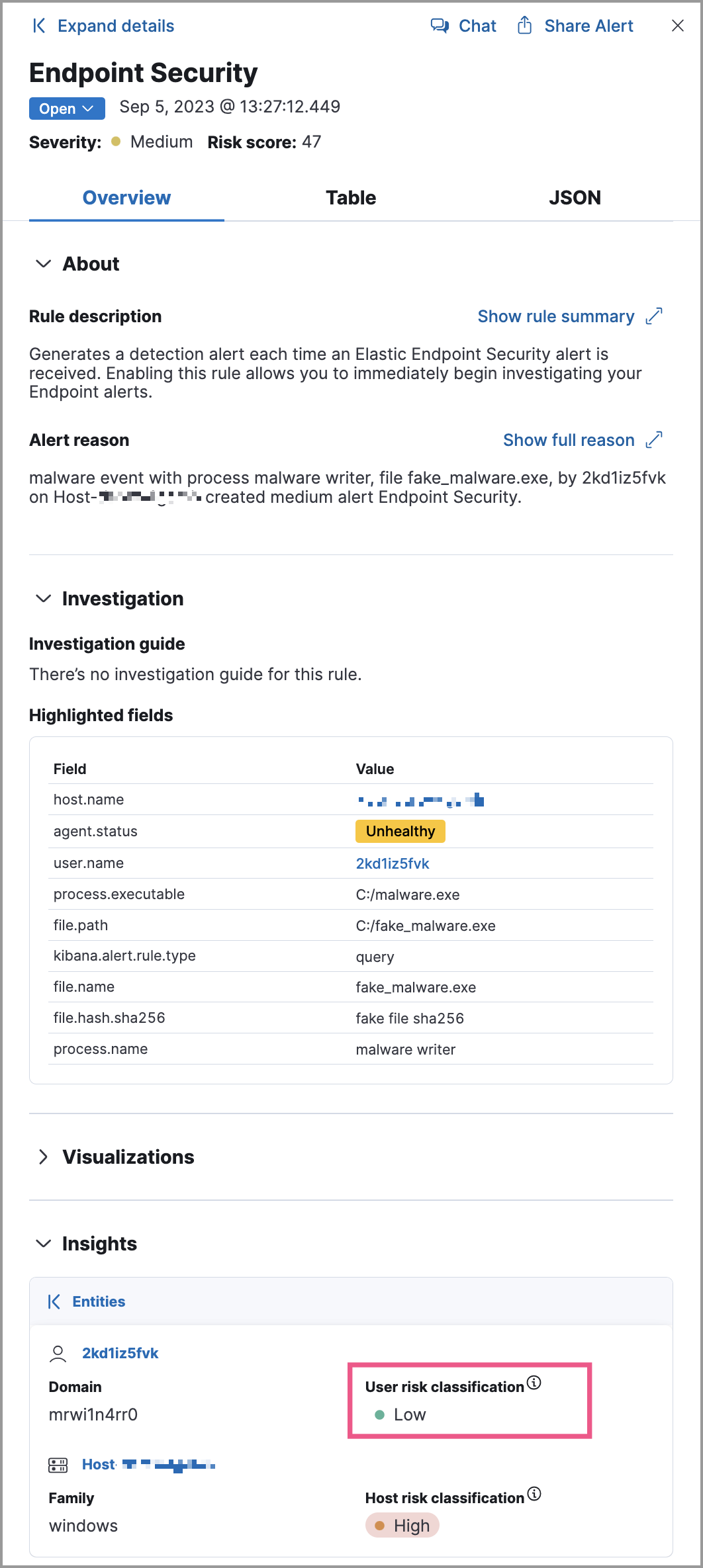
The Insights → Entities section on the Overview tab within the alert details flyout
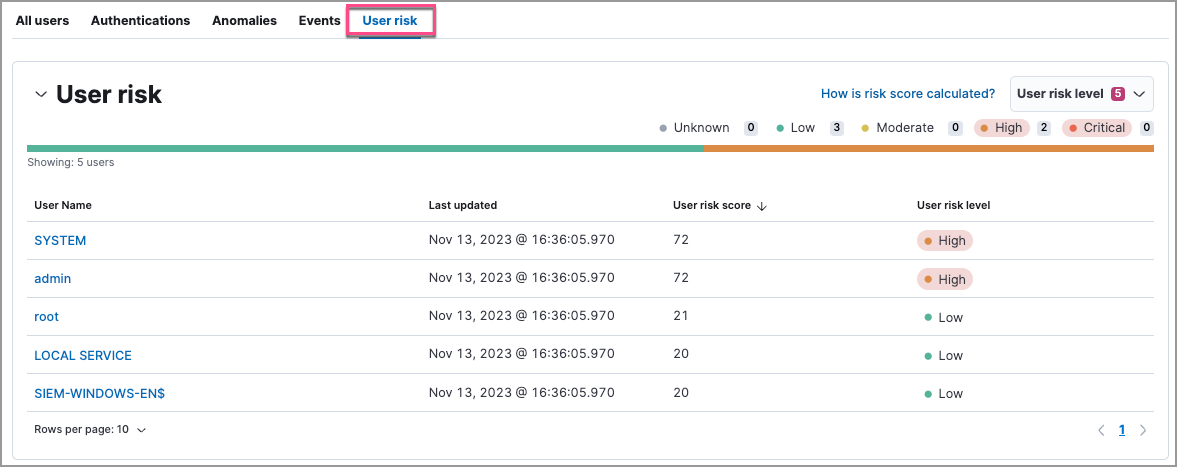
The User risk tab on the Users page:
The Overview section on the user details page:
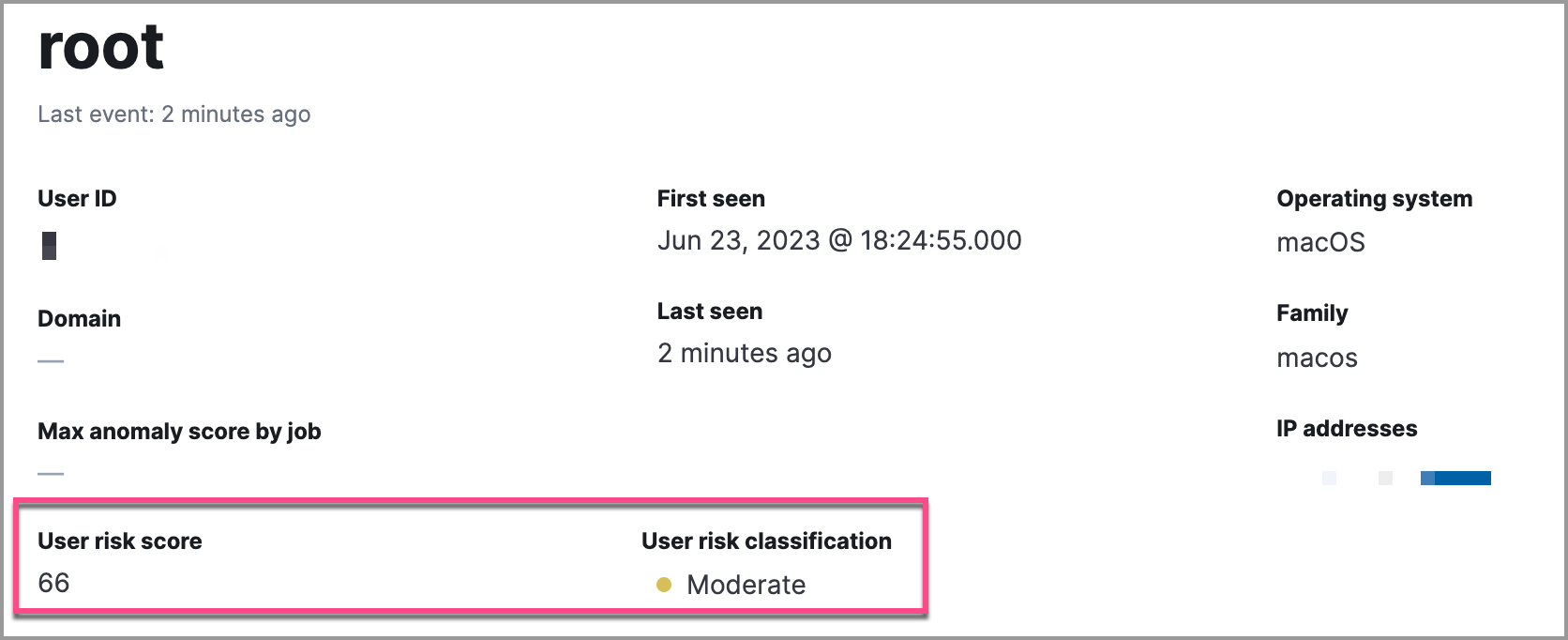
The User risk tab on the user details page:
You can also visualize user risk score data using prebuilt dashboards that are automatically imported when the feature is enabled.
To access the dashboards:
-
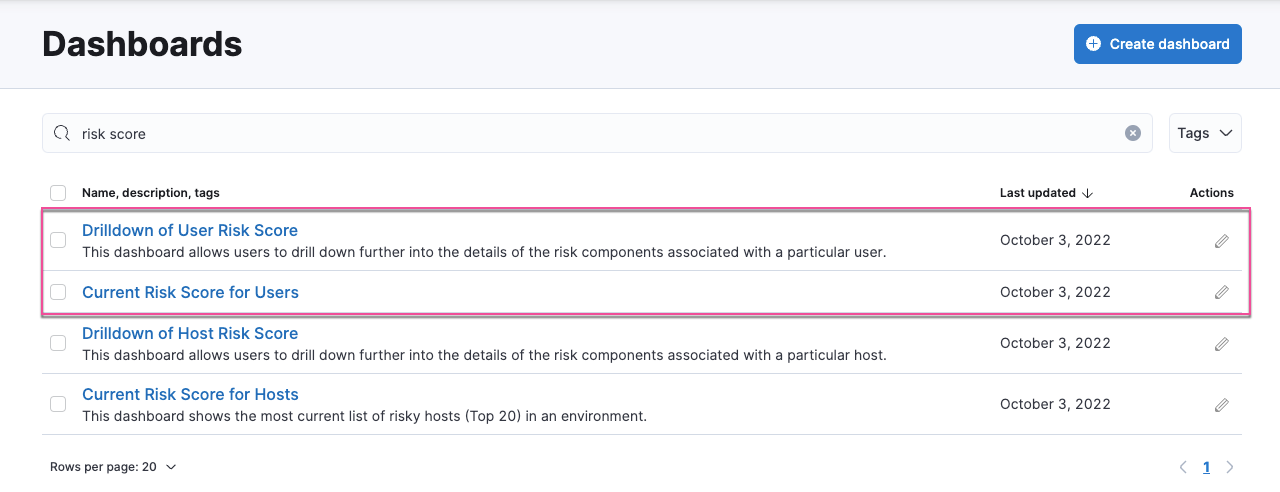
In Kibana, go to Analytics → Dashboard, then search for
risk score. - Select Drilldown of User Risk Score to analyze the risk components of a user, or Current Risk Score for Users to display a list of current risky users in your environment.
In this example, we’ll explore the Drilldown of User Risk Score dashboard.
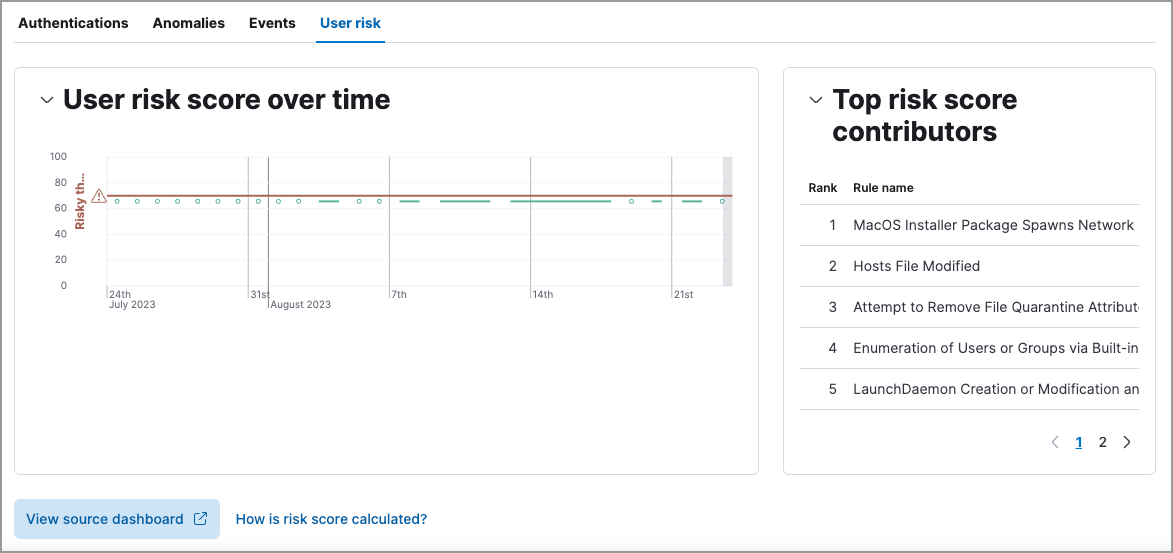
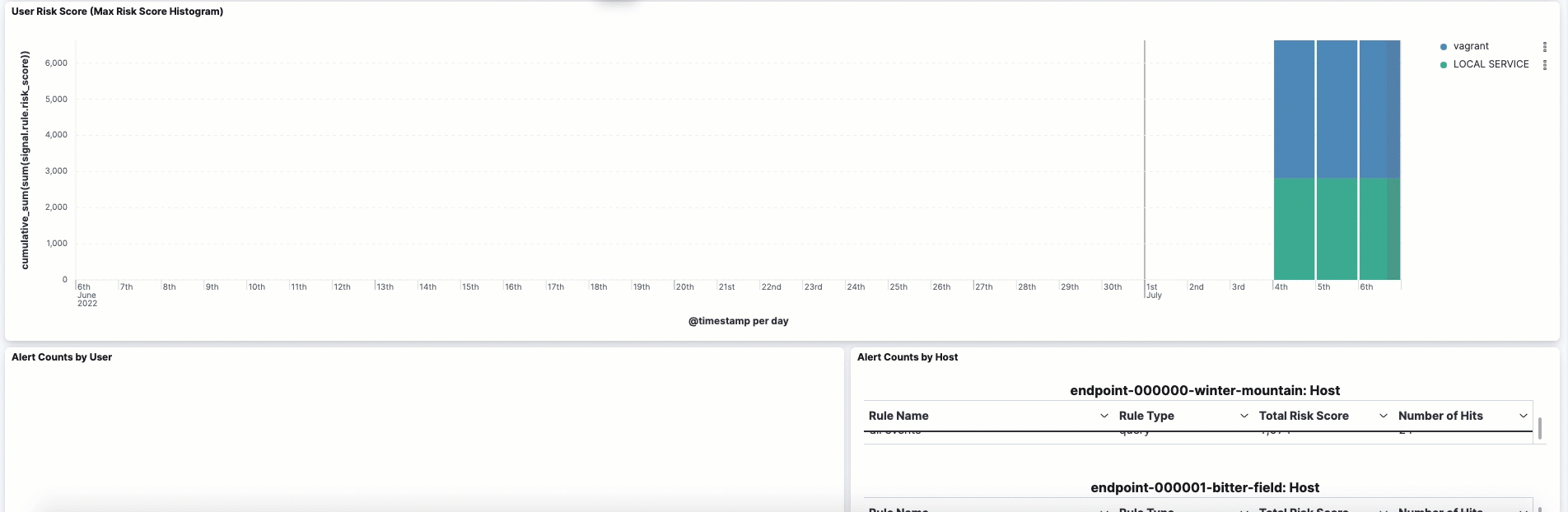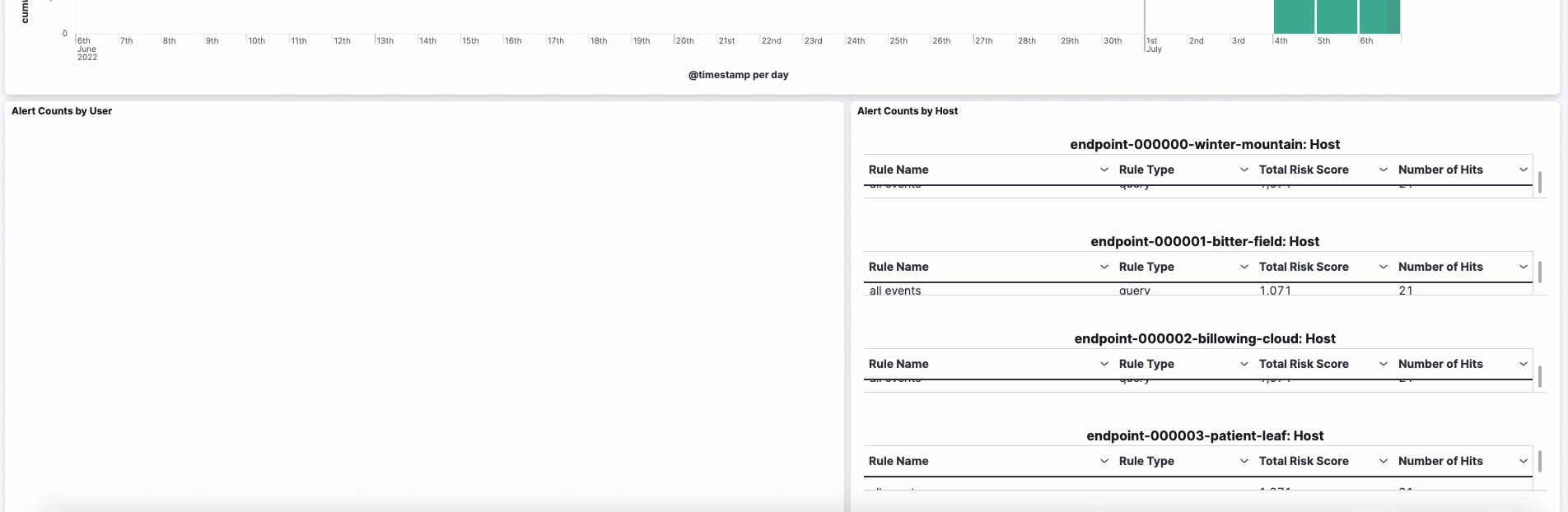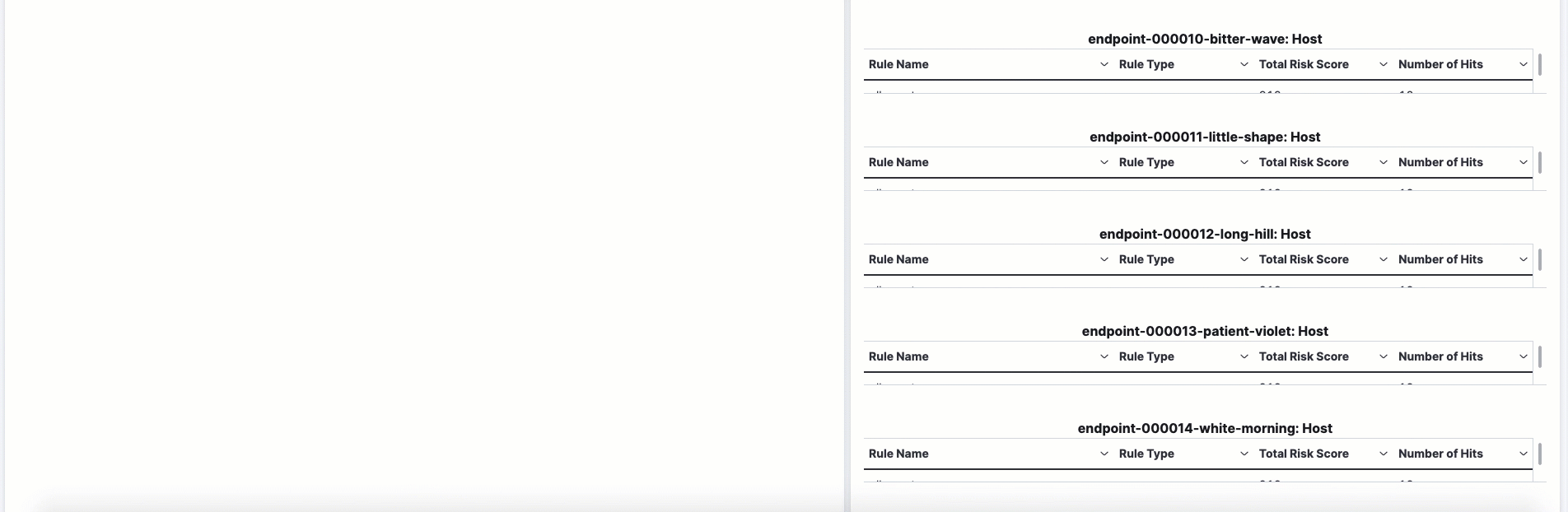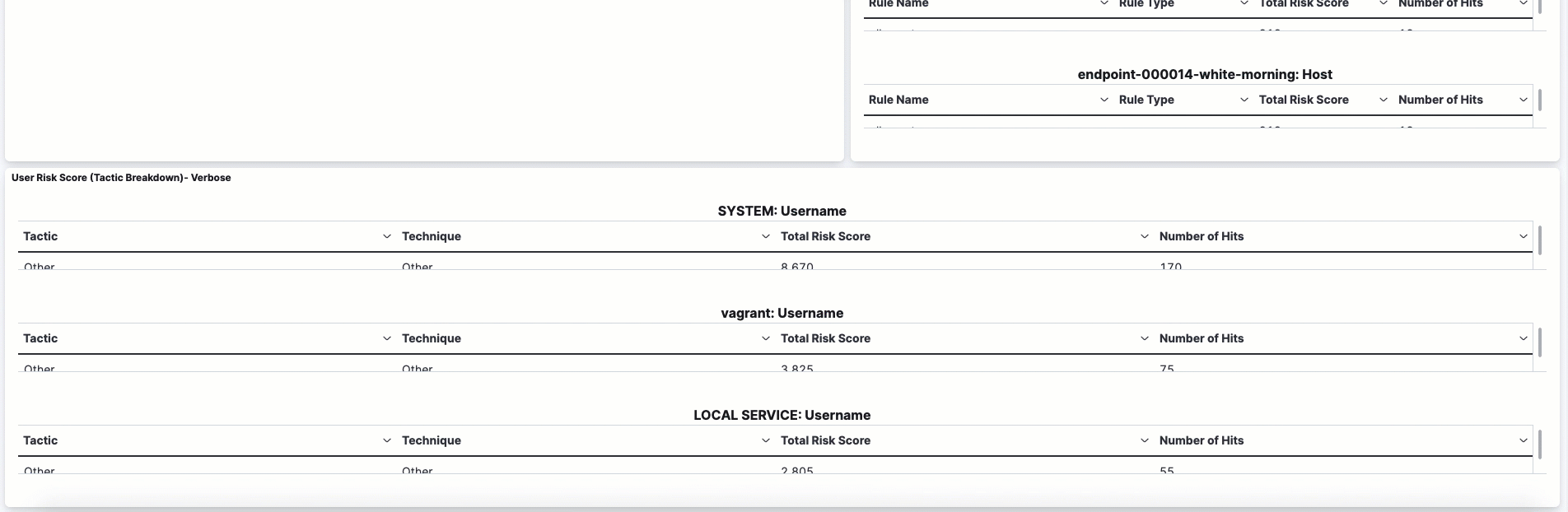
The histogram shows historical changes in a particular user’s risk score(s). To specify a date range, use the date and time picker, or drag and select a time range within the histogram. Click View source dashboard to view the top values of user.name and risk.keyword.
The data tables beneath the histogram display associated rules, users, and MITRE ATT&CK tactics seen for risky users. By default, the tables are sorted by risk, with the highest total risk scores at the top. Use this information to triage your highest risk users.
Troubleshooting
editDuring the installation or upgrade process, you may receive the following error messages:
-
Saved object already exists -
Transform already exists -
Ingest pipeline already exists
In this case, we recommend that you manually delete the user risk score module, and then re-enable it. To manually delete the module:
-
Delete the user risk score saved objects:
- From the Kibana main menu, go to Stack Management → Kibana → Saved Objects.
-
Delete the saved objects that have the
User Risk Score - <space-id>tag.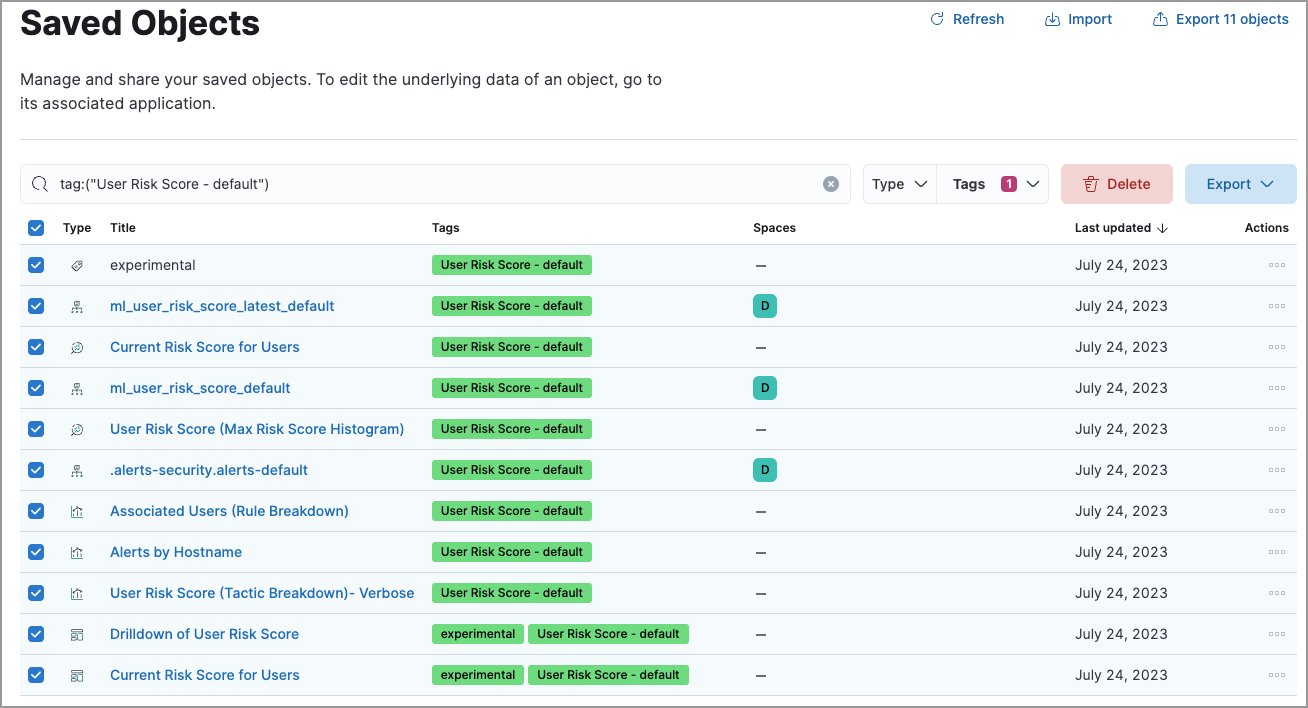
-
Delete the
User Risk Score - <space-id>tag.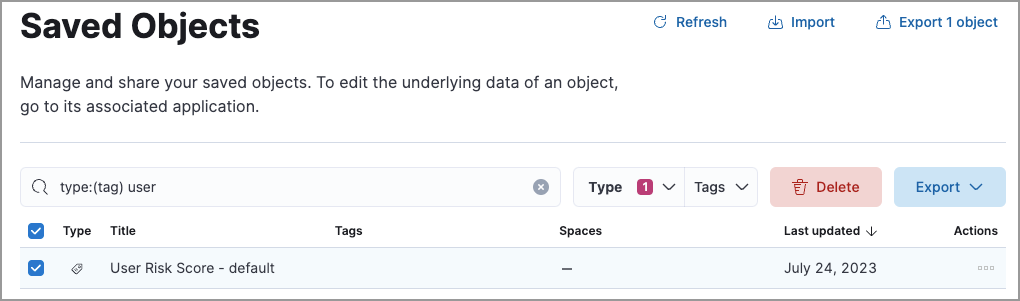
-
Stop and delete the user risk score transforms. You can do this using the Kibana UI or the Stop transform API and Delete transform API.
-
To delete the user risk score transforms using the Kibana UI:
- From the Kibana main menu, go to Stack Management → Data → Transforms.
-
Stop the following transforms, then delete them:
-
ml_userriskscore_latest_transform_<space-id> -
ml_userriskscore_pivot_transform_<space-id>
-
-
To delete the user risk score transforms using the API, run the following commands in Console:
-
Stop and delete the latest transform:
POST _transform/ml_userriskscore_latest_transform_<space-id>/_stop DELETE _transform/ml_userriskscore_latest_transform_<space-id>
-
Stop and delete the pivot transform:
POST _transform/ml_userriskscore_pivot_transform_<space-id>/_stop DELETE _transform/ml_userriskscore_pivot_transform_<space-id>
-
-
-
Delete the user risk score ingest pipeline. You can do this using the Kibana UI or the Delete pipeline API.
-
To delete the user risk score ingest pipeline using the Kibana UI:
- From the Kibana main menu, go to Stack Management → Ingest → Ingest Pipelines.
-
Delete the
ml_userriskscore_ingest_pipeline_<space-id>ingest pipeline.
-
To delete the user risk score ingest pipeline using the Delete pipeline API, run the following command in Console:
DELETE /_ingest/pipeline/ml_userriskscore_ingest_pipeline_<space-id>
-
-
Delete the stored user risk score scripts using the Delete stored script API. In Console, run the following commands:
DELETE _scripts/ml_userriskscore_levels_script_<space-id> DELETE _scripts/ml_userriskscore_map_script_<space-id> DELETE _scripts/ml_userriskscore_reduce_script_<space-id>
After manually deleting the user risk score saved objects, transforms, ingest pipeline, and stored scripts, follow the steps to re-enable the user risk score module.