Release Notes
editRelease Notes
edit7.13.3
editBug fixes and enhancements
edit- Fixes the JavaScript error that occurred when users opened an alert’s detailed view while an event’s detailed view was still open (#103970).
7.13.2
editKnown issue
editThe following Machine learning rules contain incorrectly configured ML job IDs (underscores were used instead of dashes between words) and cannot be successfully activated after they are enabled. Running these rules will cause an error message to display, indicating that an error occurred during the rule’s execution. This issue is present in Elastic Stack 7.13, 7.13.1, and 7.13.2. (#102146)
-
high-count-by-destination-country -
high-count-network-denies -
high-count-network-events -
rare-destination-country
To ensure these rules can sucessfully run, duplicate the rule and edit it using these steps:
- Go to the Detections page and select Manage detection rules.
-
Filter the Rules table to only display rules with the
MLtag and search for the ML rule you want to duplicate. - Select the rule you want to duplicate and click Bulk actions → Duplicate selected.
- Select the duplicated rule and click Edit rule settings.
-
From the Definition tab, enter the correct ML job ID. For example, to fix the incorrectly configured
high_count_by_destination_countryML rule job ID, remove the current job ID and enterhigh-count-by-destination-country. Click Save changes after you’ve finished. - Delete the prebuilt ML job.
7.13.0
editFeatures
edit- A new Osquery Manager integration is now available as a beta in Fleet. Osquery provides a search box into hosts, leveraging security, compliance, and operations use cases. The integration enables users to centrally manage osquery deployment to Elastic Agents, run live queries against those agents, and schedule recurring queries. For more information about this new integration see the package readme.
- Adds pre-packaged rule updates through the "Prebuilt Security Detection Rules" Fleet integration (#96698).
- Filters the Alerts table by threat presence (#96096).
-
Populates
threat.indicator.eventwithsource.eventdata (#95697). - Adds the threat summary to the Summary tab in the Alert details flyout and introduces the Threat Intel tab (#95604) (#97185).
- Updates Cloud plugin to handle new config values in kibana.yml (#95569).
Bug fixes and enhancements
edit- Fetches detection adoption metrics (#97789).
- Updates fields with Beats metadata (#97719).
- Updates detection alert mappings to ECS 1.9 (#97573).
- ML rules accept multiple ML job IDs (#97073).
- Adds the Security Network ML Module to the list of available jobs (#97014).
- Updates MITRE tactics, techniques, and subtechniques (#97011).
- Improves user experience duplicating rules (#96760).
- Introduces a nested CTI row renderer (#96275).
- Rebuilds nested fields structure from field’s response (#96187).
- Combines multiple timestamp searches into a single request (#96078).
- Adds the Indicator Match Timeline template (#95840).
- Fetches additional detection rule adoption metrics (#95659).
- Adds HTTP endpoints for the Timeline (#95036).
- Updates the agent status labels and colors (#99314).
-
Fixes an issue where many
ORclauses take up too much vertical space (#98706). - Adds network responses to error toasters (#97945).
- Fixes issue where long hostnames were truncated in the agent detail flyout.(#97253).
- Fixes a bug with DNS query that caused additional terms to be accidentally requested. (#97069).
- Allows a preview of query results when creating a new rule or editing an existing one. (#94018).
- Fixes the rule details page to show the rule details loading when the Activated switch is toggled. (#94010).
-
Sets the default date time on the timepicker to
todayinstead ofLast 24 hoursto enable cachability. Also fixes a date math bug in the URL (#93548). - Fixes size issue with detection rule telemetry (#99900).
- Excludes meta fields from the fields API request(#99443).
Known issues
edit-
A histogram cannot be generated for these fields because their mappings have changed:
-
dll.Ext.mapped_address -
dll.Ext.mapped_size -
process.thread.Ext.start_address
-
7.12.1
editBug fixes and enhancements
edit-
Removes empty values in the
threshold.fieldarray for threshold rules (#97111). - Fixes the issue where the Read Less button in the Event Details flyout is rendered below the fold if an event’s message field is too large (#96524).
- Resolves regression where Elastic Endgame rules would warn about the unmapped timestamp override field (#96394).
- Standardizes process fields in Endpoint Security telemetry (#95836).
-
Adds
threshold_resultto the alert notification context (#95354). - Updates the threshold preview to account for threshold field groups and cardinality (#94224).
- Fixes bug for pre-populated endpoint exceptions (#94025).
7.12.0
editFeatures
editBug fixes and enhancements
edit- Enables the Microsoft Team’s action type for the detection engine (#94239).
- Fixes bug for pre-populated endpoint exceptions (#94025).
- Pushes ServiceNow ITSM comments on cases and alerts as work notes and improves error messaging (#93916).
- Alert migrations can be finalized and cleaned up in all spaces (#93809).
- Updates error handling logic to produce a cleaner message when deeply nested fields in KQL queries are greater than the default or what is set for the config property (#93536).
- Updates shellcode telemetry for schema adjustment (#93143).
- Fixes bug in the allowlist layout for security telemetry (#92850).
- Updates exceptions modal to use existing lists plug-in (#92348).
- Moves PE details out of Ext context (#92146).
- Fixes loading indicators in the rules management table (#91925).
- Adds missing fields for security telemetry (#91920).
- Fixes issues when pushing a case, that has alerts attached, to an external service (#91638).
- Updates error banner when refreshing the rule status (#91051).
- Fixes bug in the exceptions builder UI that causes invalid values to overwrite other values (#90634).
- Fixes issues with searching the Exceptions list table by name (#88701).
- Threshold rule fixes (#93553)(#92667).
- Adds sub cases to the case list and a case details page (#91434).
- Upgrades to use the IndexPatternService to get fields (#91153).
- Adds new fields to the allowlist for alert telemetry (#90868).
-
Adds support for multiple
termsaggregations within a Threshold Rule, as well as an additionalcardinalityaggregation for matching a specific number of unique values across a field. (#90826). - Introduces the network details and host details to the side panel. (#90064).
- Adds ransomware exceptions (#89974).
- Extends the daily usage collection to include perf and run information on active security ML jobs. (#89705).
-
Reduces the detection engine’s reliance on
_source(#89371). - Pushes a new case to the connector when created (#89131).
- Disallows JIRA labels with spaces (#90548).
- Fixes "Error loading data" displaying under Analyze Event (#91718).
Known Issues
edit- Pagination does not work in the All Cases table. To circumvent this, increase the total number of rows that are displayed per page by selecting an option from the Rows per page menu. Alternatively, decrease the number of rows displayed in the table by filtering the list of cases that are returned. Finally, if you know which case you want to view, enter descriptive text about it into the search bar at the top of the table. (#94929).
7.11.2
editBug fixes and enhancements
edit- Updates warning message when no indices match provided index patterns (#93094).
-
Fixes rule edit bug with
max_signals(#92748). - Fixes issue where the file name in a value modal list would be truncated (#91952).
- Adds an overflow text wrap for rule descriptions (#91945).
- Fixes issue in detection search where searching with the timestamp override field would yield a 400 error(#91597).
-
Replaces
partial failurewithwarningfor rule statuses (#91167).
7.11.0
editBreaking changes
editReferential integrity issues when deleting value lists
The /api/lists DELETE API has been updated to check for references before removing the specified resource(s) from value lists and will now return a 409 conflict if any references exist. Set the new ignoreReferences query param to true to maintain the behavior of deleting value list(s) without performing any additional checks.
Bug fixes and enhancements
edit- Corrects look-back time logic now displays whatever unit the user selects (#81383).
- Fixes a bug where mapping browser fields were automatically reduced (#81675).
- Allows both status data for enabled and disabled rules are now fetchable (#81783).
- Allows autorefresh to be toggled in Advanced Settings (#82062).
- Makes severity and risk score overrides more flexible (#83723).
- Improves DE query build times for large lists (#85051).
- Adds skeleton exceptions list tab to all rules page (#85465).
- Fixes export on exceptions functionality list view (#86135).
- Fixes exception list table referential deletion (#87231).
- Disables delete button for endpoint exceptions (#87694).
Known issues
edit-
The Elastic Endpoint Security rule will report a failure status until the Endpoint sends an alert for the first time. At that point, the next rule execution will succeed.
logs-endpoint.alerts-*index pattern does not get created until the Endpoint sends the first alert (#90401). - In the Alert Details Summary view, values for some fields appear truncated. You’ll only be able to see the first character (#90539).
7.10.1
editBug fixes and enhancements
edit7.10.0
editPost upgrade requirements
editWhen upgrading the Elastic Stack to version 7.10.0 from a previous minor version (7.9.x), perform the following:
-
Grant
view_index_metadatapermissions to any Elastic Security users. This is required to enable event correlation rules. Other previously activated detection rules will continue to run after upgrade.
Breaking changes
editSignals template updated for rollover indices
The create_index_route now checks if the template needs to be upgraded
before creating the index. If the index already exists and the template was upgraded,
the index rolls over so that the write index has the upgraded mapping.
This breaks the old mappings that have risk_score mapped as a keyword.
In the new mapping, signal.rule.risk_score is a float. After rolling over,
there is a conflict between the old and new signal.rule.risk_score for some
features, such as aggregations.
This requires the view_index_metadata permission in Kibana. See (#80019) for details.
Connect incident fields allowed when cases are sent
You can now specify connector incident fields when cases are sent. This includes: * Jira: issue type, priority, and parent issue in the case of a subtask. * IBM Resilient: issue types, and severity. * ServiceNow: urgency, severity, and impact.
See (#77327) for details.
Bug fixes and enhancements
edit- Adds Metadata and Discovery Analysis Jobs to Security Integration (#76023).
- Improves Alert Telemetry for the Security app (#77200).
- Allows passwords to be visible on security screens (#77394).
- Groups features for role management (#78152).
- Warns users when security is not configured (#78545).
- Enhancements for saved object management workflows (#75444).
- Adds EQL search strategy for security (#78645).
- Fetches related events from specified devices (#78780).
- Excludes cloud alias index from EQL query (#81551).
- Telemetry: Displays collected security event sample (#78963).
- Analyze Events: Requests data from new event API (#78782).
- Detections: Handle conflicts on alert status update (#75492).
Known issues
edit-
If you edit a rule while that rule is running, the rule fails. Subsequent successful runs will retain the previous failure message (#82320).
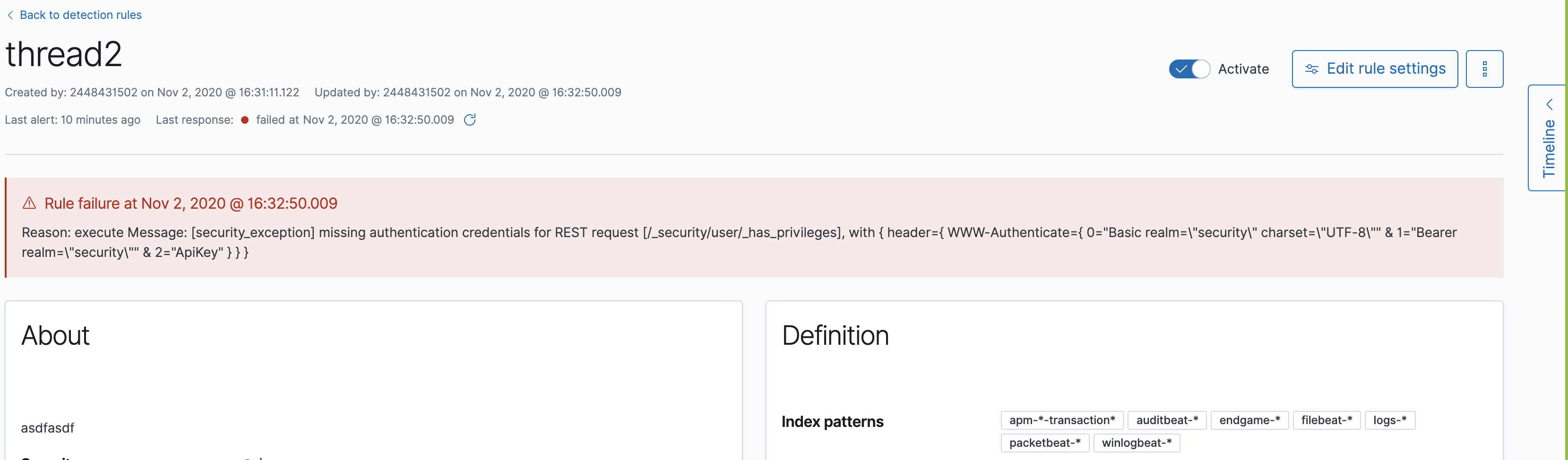
-
When adding a rule exception, you cannot select value lists of type
ip_range. Lists of typeip_rangewill not appear in the Add Exception dropdown as possible values after selecting the is in list operator. (#79511).
7.9.1
editPost upgrade requirements
editAfter upgrading the Elastic Stack to version 7.9.0 and 7.9.1 from a previous minor release (7.8.x, 7.7.x, and so on), you need to:
- Enable access to the Detections page. Previously activated detection rules continue to run after upgrading, and this is only required to enable the UI.
- Enable the process analyzer. This is only required if you want to view graphical representations of process relationships.
Bug fixes and enhancements
edit- Fixes closing alerts via exceptions (#76145).
- Fixes selecting all alerts issue (#75945).
- Fixes issues when exceptions are no longer associated with a rule (#76012).
- Prevents adding exceptions to unsupported rule types (#75802).
- Corrects error messages for insufficient machine learning permissions (#74582).
-
Increases permissions granularity for the
.listssystem index (#75378).
7.9.0
editBreaking changes
editActions API
When you create a ServiceNow connector via the Actions API:
-
The
casesConfigurationobject is obsolete. Instead, useincidentConfiguration. -
To see ServiceNow connectors in the UI, you must use the
isCaseOwnedfield.
These changes only apply to ServiceNow connectors.
Known issues
edit-
After changing the
xpack.encryptedSavedObjects.encryptionKeysetting value and restarting Kibana, you must restart all detection rules (#74393). - When selecting all alerts on the Detections page, some alerts are not marked as selected in the UI (#75194).
- When creating rules, if you have more than one Timeline template the template drop-down list is truncated (#75196).
- Exceptions cannot be added to or viewed in imported rules when the exception list has been deleted or does not exist in the Kibana space (#75182).
- Updates to a Timeline may not be saved when you immediately close the Timeline or navigate to a different page (#75292).
Bug fixes and enhancements
edit-
Fixes rule tags to accept special characters and keywords:
AND,OR,(,),", and*(#74003). - Fixes broken link from the Network map to Kibana index management (#73757).
-
Fixes unresponsive Timeline issues when dragging the
process.hash.sha256field to Timeline (#72142). - Fixes Timeline page scrolling with saved queries issue (#69433).
- Fixes a UI issue with opening and closing alerts (#69217).
- Fixes display of long rule reference URLs (#68640).