ServiceNow ITSM connector and action
editServiceNow ITSM connector and action
editThe ServiceNow ITSM connector uses the import set API to create ServiceNow incidents. You can use the connector for rule actions and cases.
Prerequisites
editAfter upgrading from Elastic Stack version 7.15.0 or earlier to version 7.16.0 or later, you must complete the following steps within your ServiceNow instance before creating a new ServiceNow ITSM connector or updating an existing one:
- Install Elastic for ITSM from the ServiceNow Store.
- Create a ServiceNow integration user and assign it the appropriate roles.
- Create a Cross-Origin Resource Sharing (CORS) rule.
-
If you use open authorization (OAuth), you must also:
Create a ServiceNow integration user
editTo ensure authenticated communication between Elastic and ServiceNow, create a ServiceNow integration user and assign it the appropriate roles.
- In your ServiceNow instance, go to System Security → Users and Groups → Users.
- Click New.
- Complete the form, then right-click on the menu bar and click Save.
- Go to the Roles tab and click Edit.
-
Assign the integration user the following roles:
-
import_set_loader -
import_transformer -
personalize_choices -
x_elas2_inc_int.integration_user
-
- Click Save.
Create a CORS rule
editA CORS rule is required for communication between Elastic and ServiceNow. To create a CORS rule:
- In your ServiceNow instance, go to System Web Services → REST → CORS Rules.
- Click New.
-
Configure the rule as follows:
- Name: Name the rule.
-
REST API: Set the rule to use the Elastic ITSM API by choosing
Elastic ITSM API [x_elas2_inc_int/elastic_api]. - Domain: Enter the Kibana URL.
- Go to the HTTP methods tab and select GET.
- Click Submit to create the rule.
Create an RSA keypair and add an X.509 certificate
editThis step is required to use OAuth for authentication between Elastic and ServiceNow.
Create an RSA keypair:
-
Use OpenSSL to generate an RSA private key:
-
Use OpenSSL to generate the matching public key:
openssl req -new -x509 -key example-private-key.pem -out example-sn-cert.pem -days 360
Add an X.509 certificate to ServiceNow:
- In your ServiceNow instance, go to Certificates and select New.
-
Configure the certificate as follows:
- Name: Name the certificate.
- PEM Certificate: Copy the generated public key into this text field.
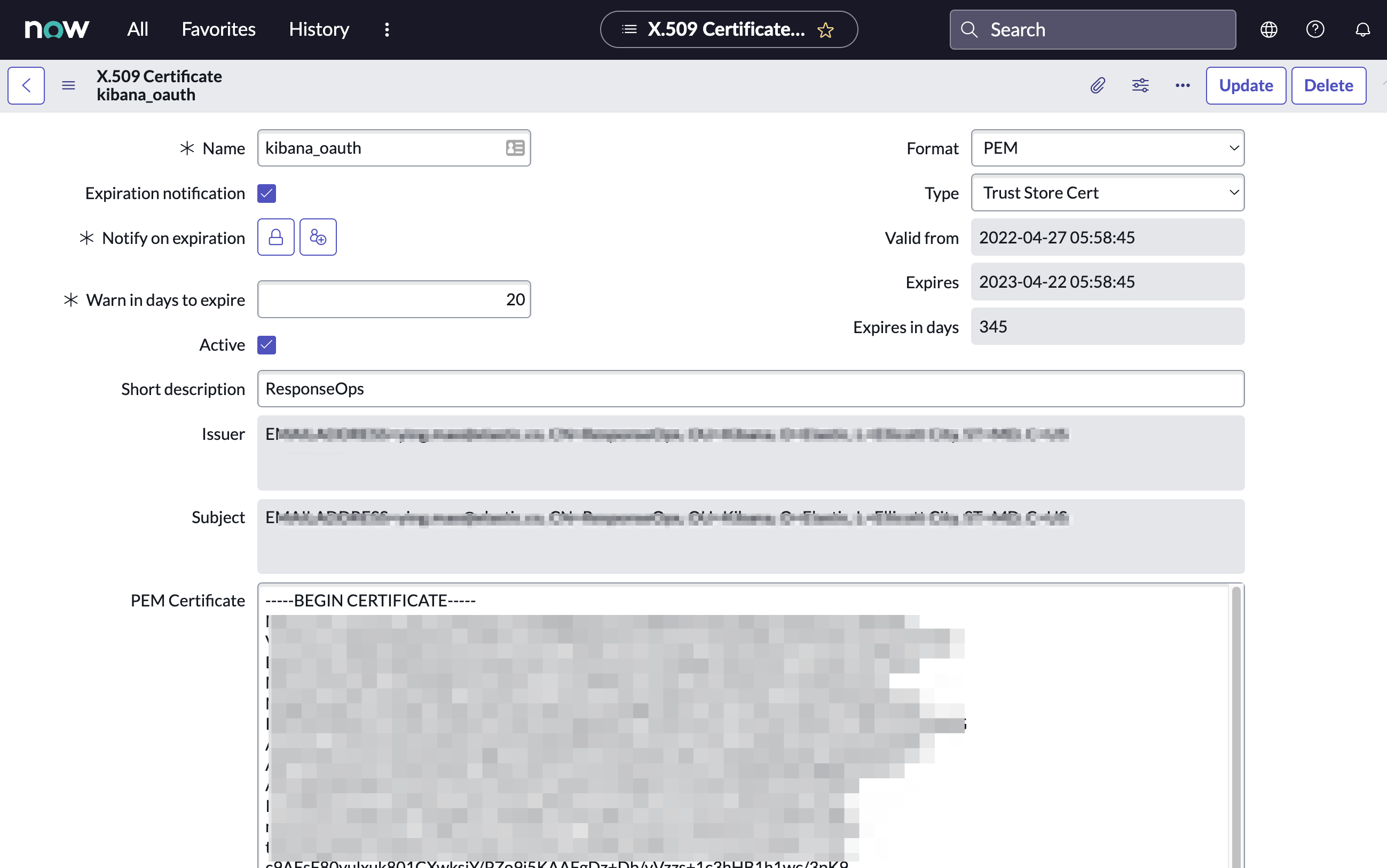
- Click Submit to create the certificate.
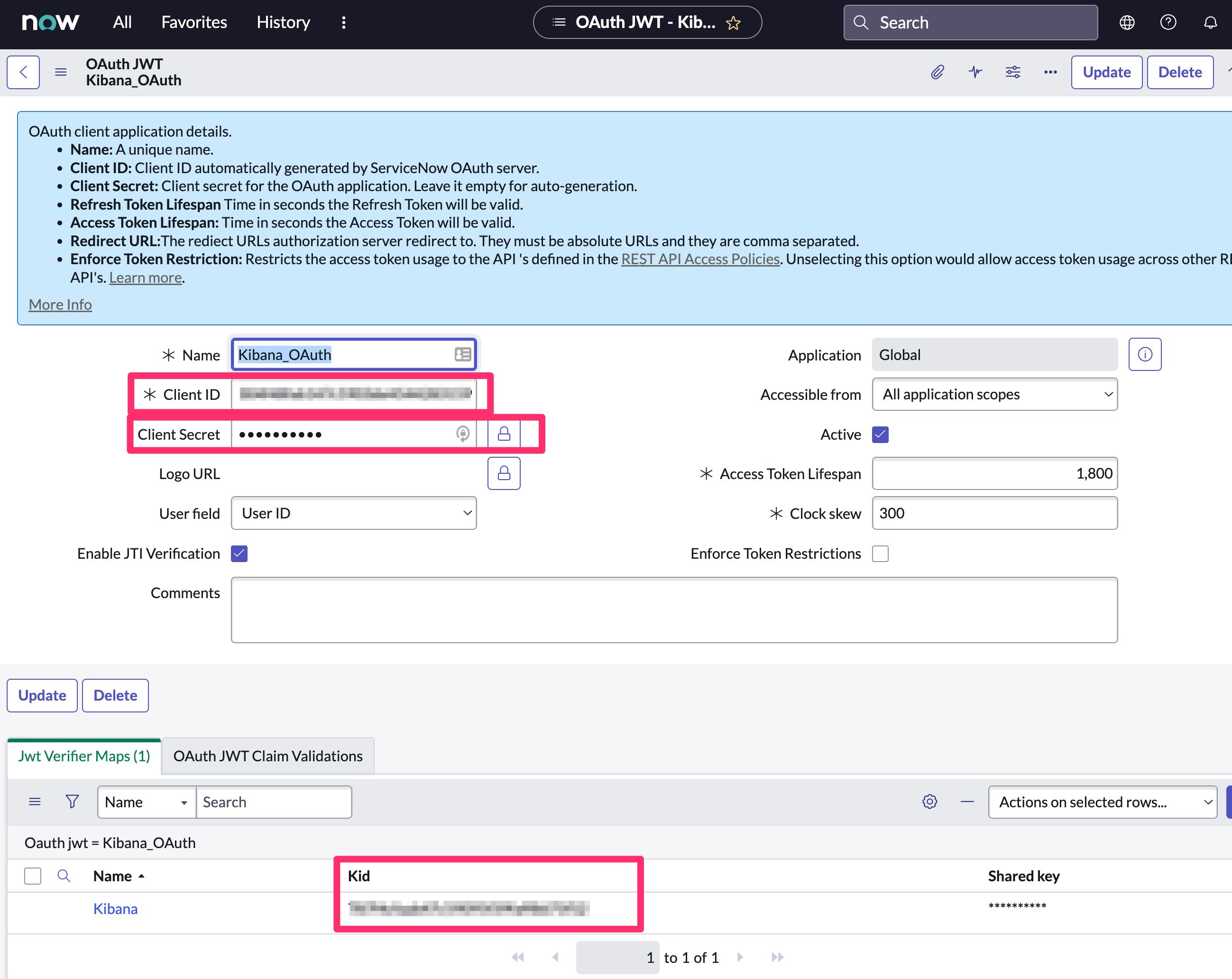
Create an OAuth JWT API endpoint for external clients with a JWT Verifiers Map
editThis step is required to use OAuth for authentication between Elastic and ServiceNow.
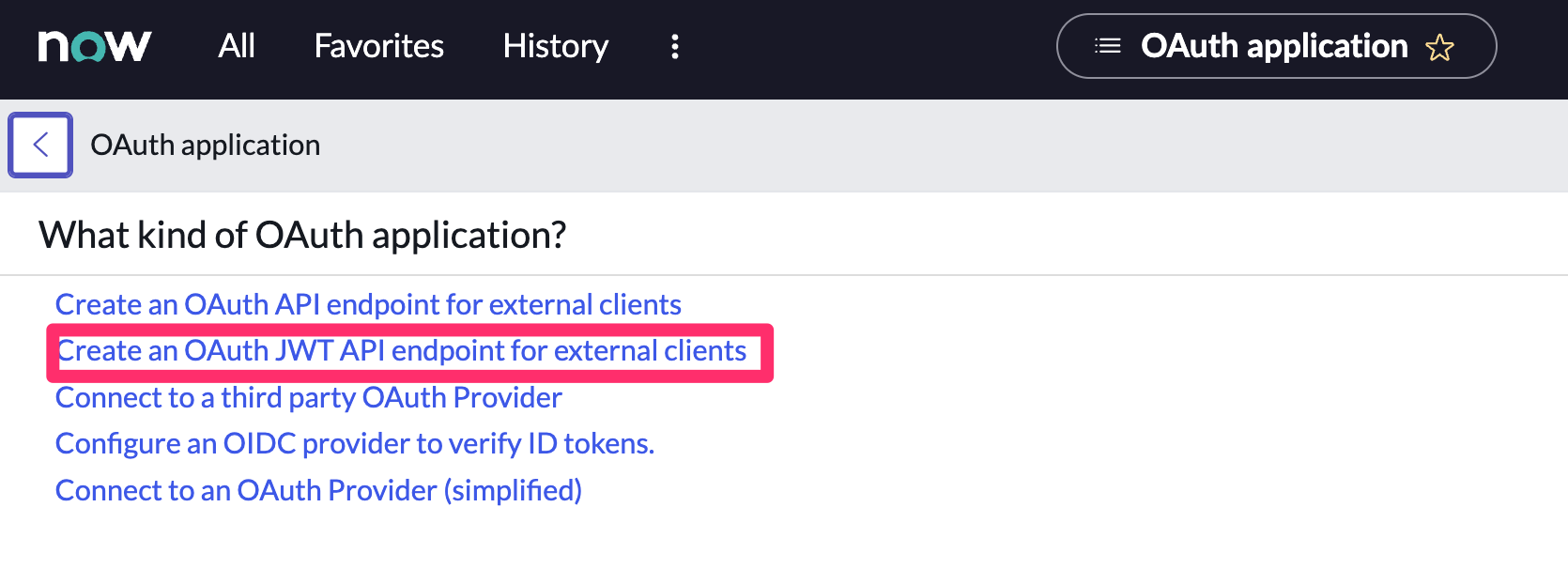
- In your ServiceNow instance, go to Application Registry and select New.
-
Select Create an OAuth JWT API endpoint for external clients from the list of options.
-
Configure the application as follows:
- Name: Name the application.
- User field: Select the field to use as the user identifier.
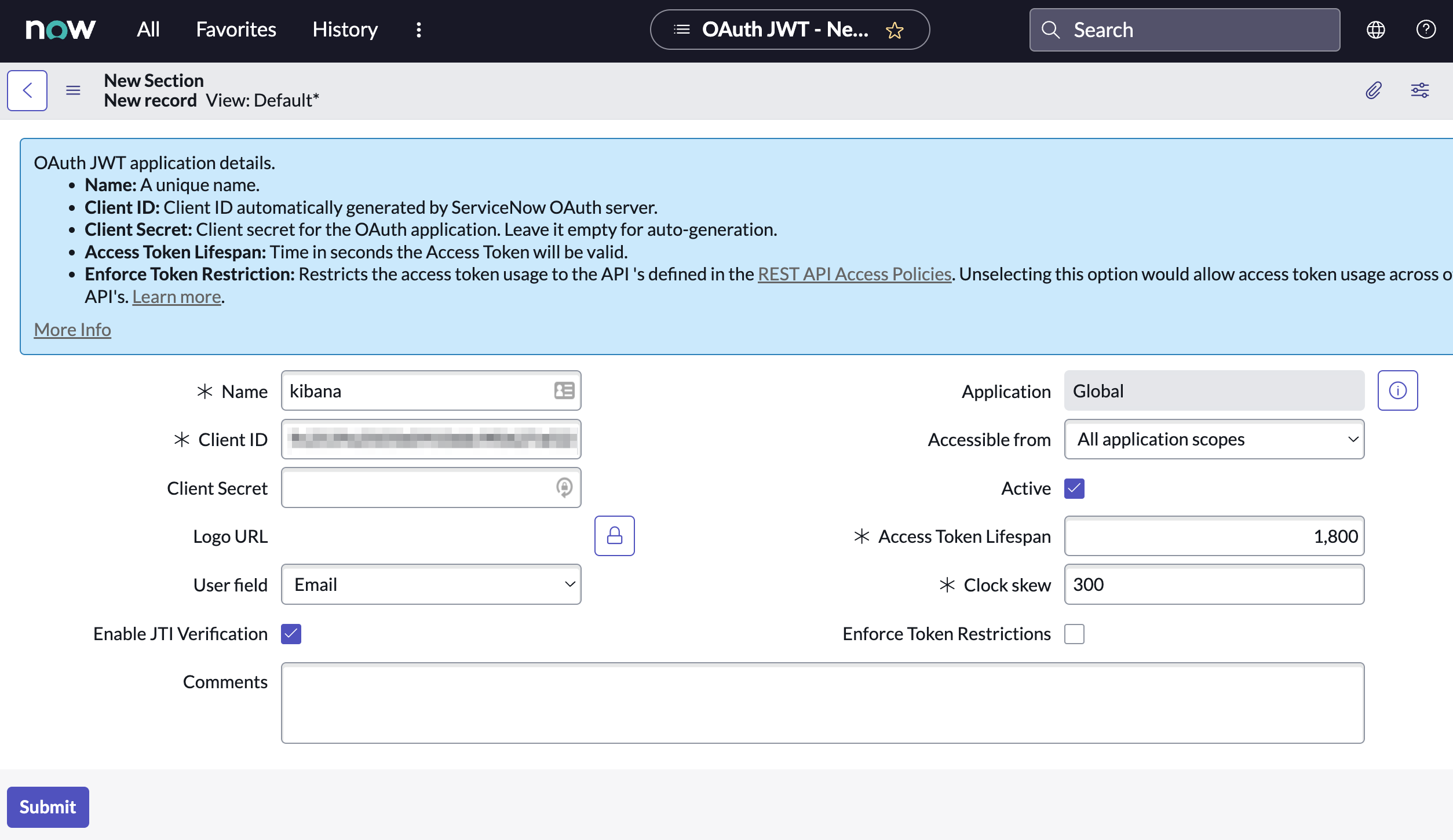
Remember the selected user field. You will use this as the User Identifier Value when creating the connector. For example, if you selected Email for User field, you will use the user’s email for the User Identifier Value.
- Click Submit to create the application. You will be redirected to the list of applications.
- Select the application you just created.
- Find the Jwt Verifier Maps tab and click New.
-
Configure the new record as follows:
- Name: Name the JWT Verifier Map.
- Sys certificate: Click the search icon and select the name of the certificate created in the previous step.
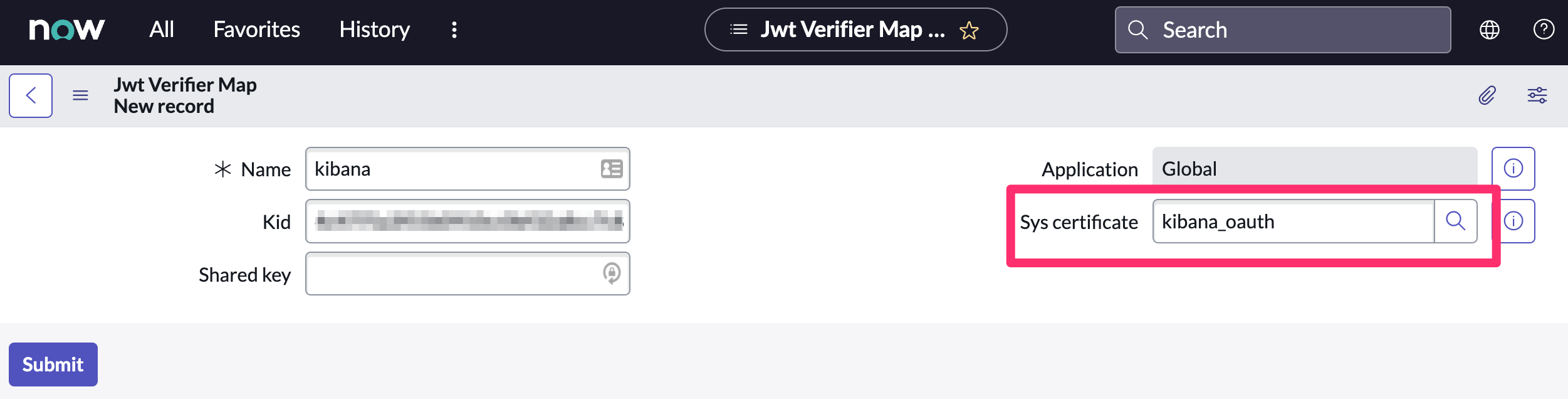
- Click Submit to create the verifier map.
-
Note the Client ID, Client Secret and JWT Key ID. You will need these values to create your ServiceNow connector.
Update a deprecated ServiceNow ITSM connector
editServiceNow ITSM connectors created in Elastic Stack version 7.15.0 or earlier are marked as deprecated after you upgrade to version 7.16.0 or later. Deprecated connectors have a yellow icon after their name and display a warning message when selected.
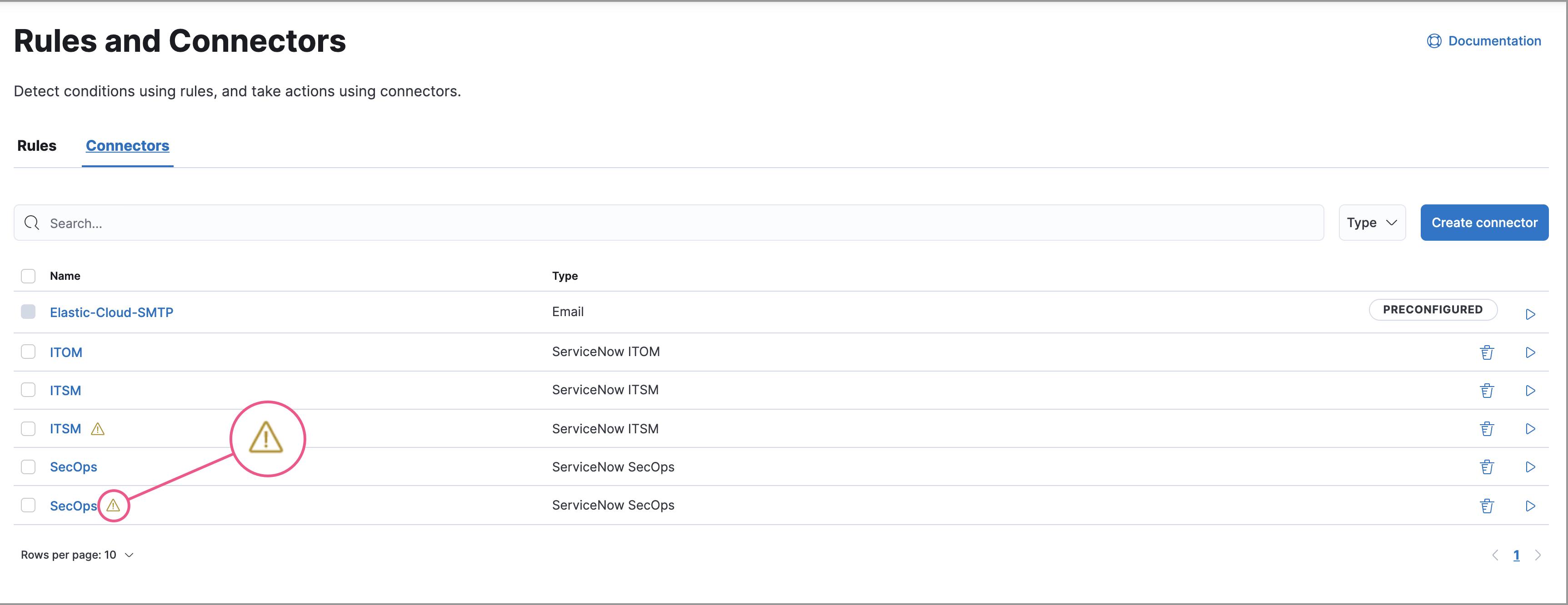
Deprecated connectors will continue to function with the rules they were added to and can be assigned to new rules. However, it is strongly recommended to update deprecated connectors or create new ones to ensure you have access to connector enhancements, such as updating incidents.
To update a deprecated connector:
- Open the main menu and go to Stack Management → Rules and connectors → Connectors.
- Select the deprecated connector to open the Edit connector flyout.
- In the warning message, click Update this connector.
-
Complete the guided steps in the Edit connector flyout.
- Install Elastic for ITSM and complete the required prerequisites.
- Enter the URL of your ServiceNow instance.
- Enter the username and password of your ServiceNow instance.
- Click Update.
Connector configuration
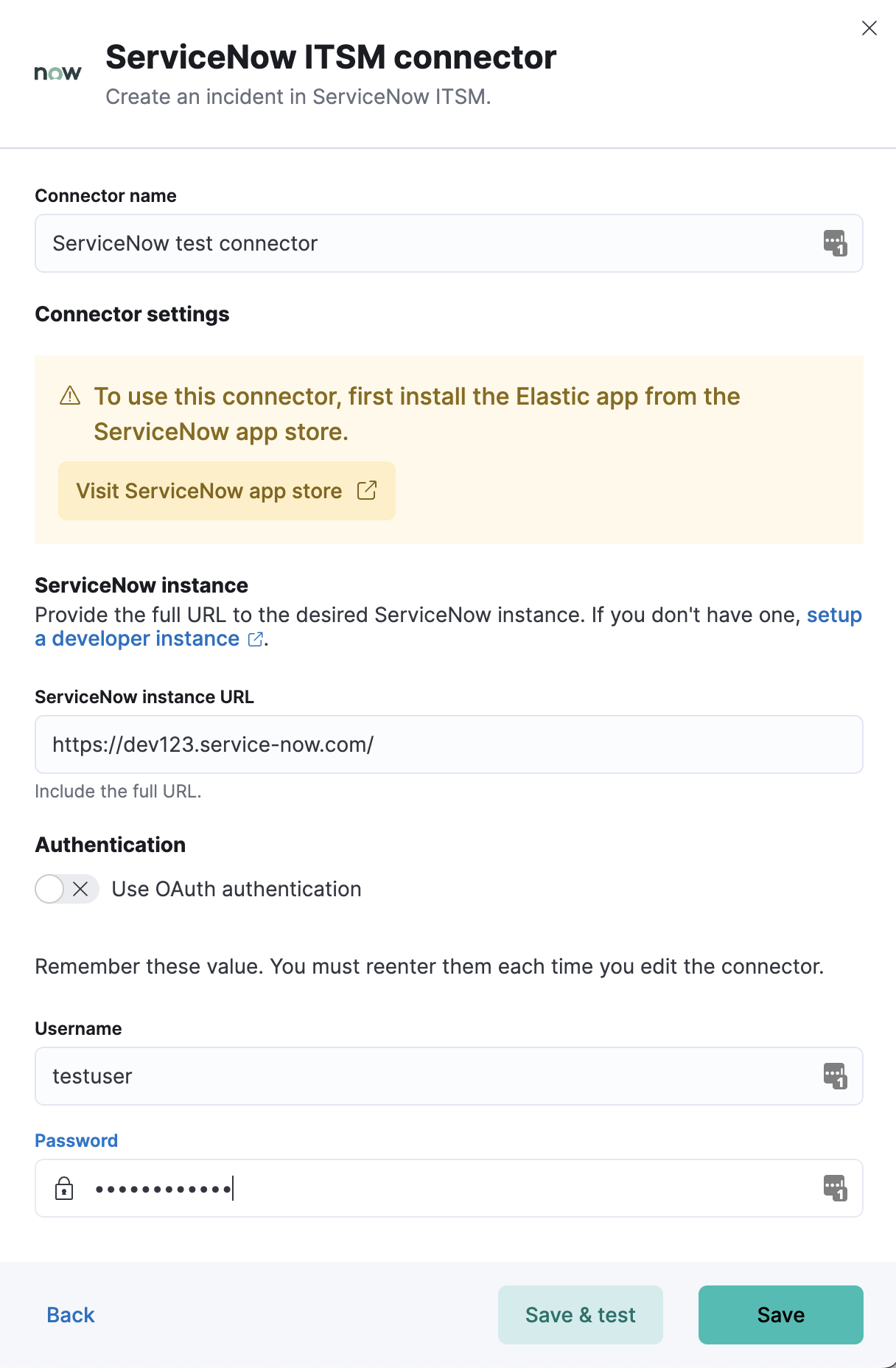
editServiceNow ITSM connectors have the following configuration properties.
- Name
- The name of the connector. The name is used to identify a connector in the Stack Management UI connector listing, and in the connector list when configuring an action.
- Is OAuth
- The type of authentication to use.
- URL
- ServiceNow instance URL.
- Username
- Username for HTTP Basic authentication.
- Password
- Password for HTTP Basic authentication.
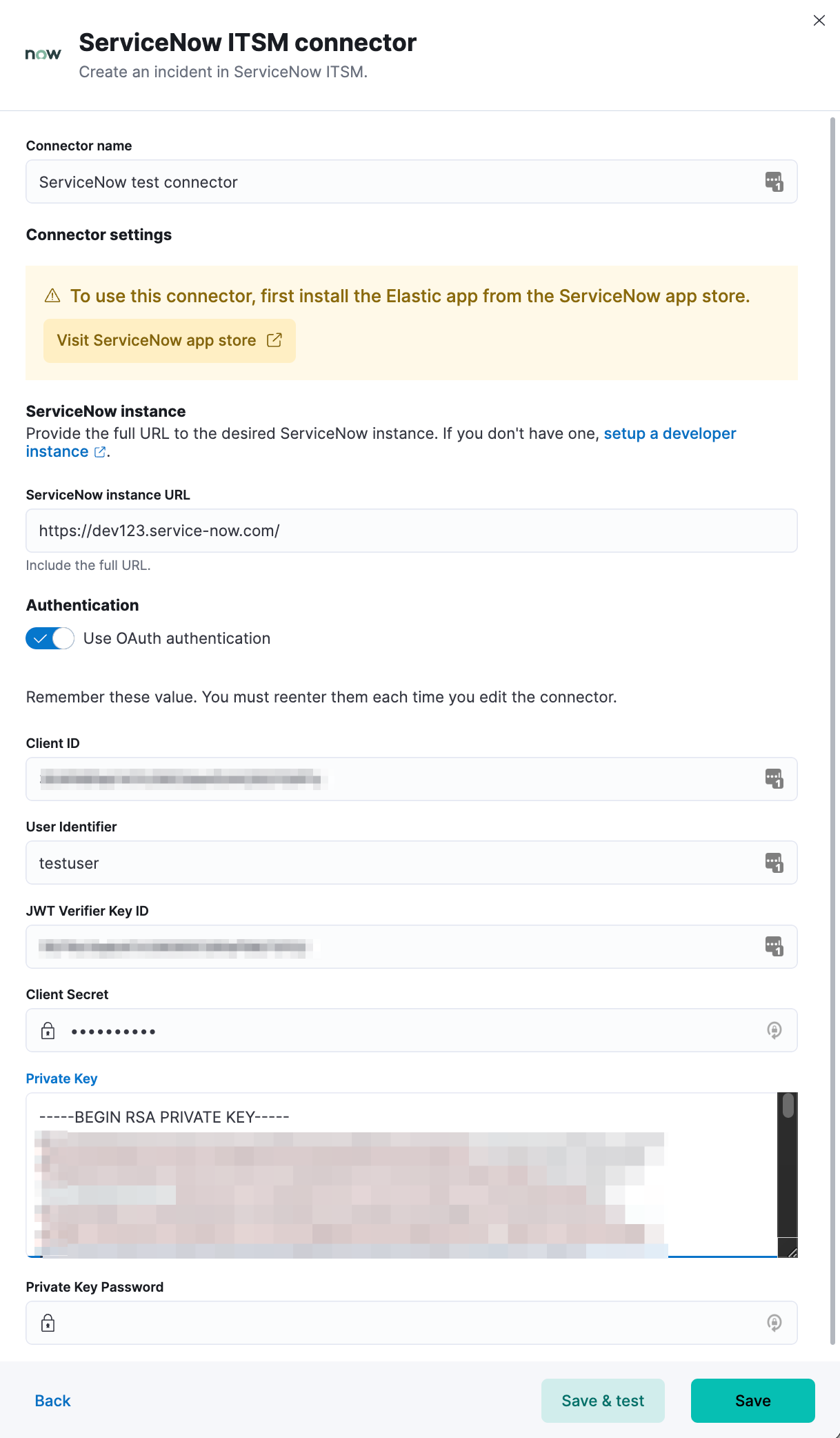
- User Identifier
- Identifier to use for OAuth type authentication. This identifier should be the User field you selected during setup. For example, if the selected User field is Email, the user identifier should be the user’s email address.
- Client ID
- The client ID assigned to your OAuth application.
- Client Secret
- The client secret assigned to your OAuth application.
- JWT Key ID
- The key ID assigned to the JWT Verifier Map of your OAuth application.
- Private Key
- The RSA private key generated during setup.
- Private Key Password
- The password for the RSA private key generated during setup, if set.
Connector networking configuration
editUse the Action configuration settings to customize connector networking configurations, such as proxies, certificates, or TLS settings. You can set configurations that apply to all your connectors or use xpack.actions.customHostSettings to set per-host configurations.
Preconfigured connector type
editConnector using Basic Authentication
my-servicenow:
name: preconfigured-servicenow-connector-type
actionTypeId: .servicenow
config:
apiUrl: https://example.service-now.com/
usesTableApi: false
secrets:
username: testuser
password: passwordkeystorevalue
Connector using OAuth
my-servicenow:
name: preconfigured-oauth-servicenow-connector-type
actionTypeId: .servicenow
config:
apiUrl: https://example.service-now.com/
usesTableApi: false
isOAuth: true
userIdentifierValue: [email protected]
clientId: abcdefghijklmnopqrstuvwxyzabcdef
jwtKeyId: fedcbazyxwvutsrqponmlkjihgfedcba
secrets:
clientSecret: secretsecret
privateKey: -----BEGIN RSA PRIVATE KEY-----\nprivatekeyhere\n-----END RSA PRIVATE KEY-----
Config defines information for the connector type.
-
apiUrl - An address that corresponds to URL.
-
usesTableApi - A boolean that indicates if the connector uses the Table API or the Import Set API.
If usesTableApi is set to false, the Elastic application should be installed in ServiceNow.
-
isOAuth - A boolean that corresponds to Is OAuth and indicates if the connector uses Basic Authentication or OAuth.
-
userIdentifierValue -
A string that corresponds to User Identifier. Required if
isOAuthis set totrue. -
clientId -
A string that corresponds to Client ID, used for OAuth authentication. Required if
isOAuthis set totrue. -
jwtKeyId -
A string that corresponds to JWT Key ID, used for OAuth authentication. Required if
isOAuthis set totrue.
Secrets defines sensitive information for the connector type.
-
username -
A string that corresponds to Username. Required if
isOAuthis set tofalse. -
password -
A string that corresponds to Password. Should be stored in the Kibana keystore. Required if
isOAuthis set tofalse. -
clientSecret -
A string that corresponds to Client Secret. Required if
isOAuthis set totrue. -
privateKey -
A string that corresponds to Private Key. Required if
isOAuthis set totrue. -
privateKeyPassword - A string that corresponds to Private Key Password.
Define connector in Stack Management
editDefine ServiceNow ITSM connector properties. Choose whether to use OAuth for authentication.
Test ServiceNow ITSM action parameters.
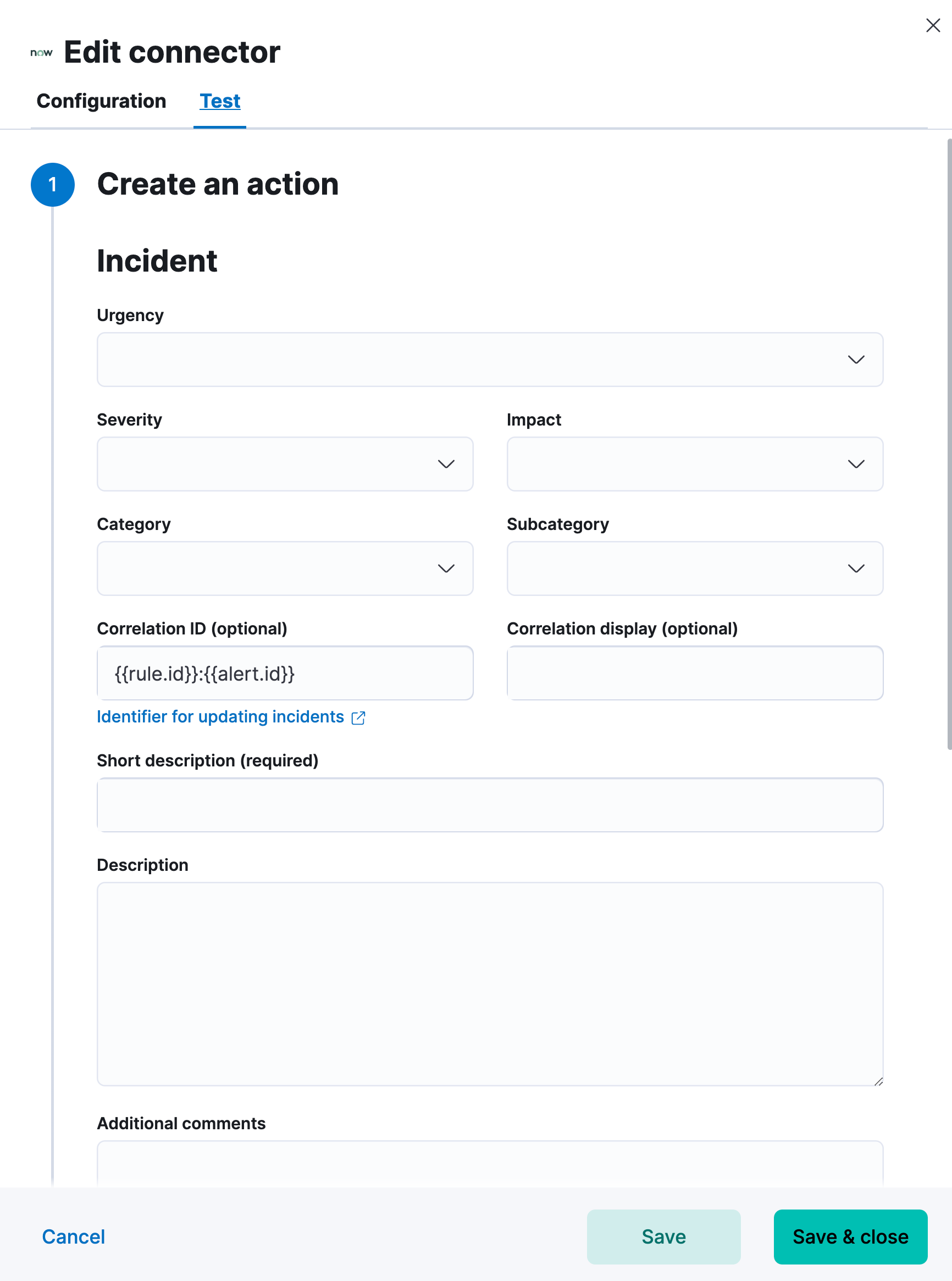
Action configuration
editServiceNow ITSM actions have the following configuration properties.
- Urgency
- The extent to which the incident resolution can delay.
- Severity
- The severity of the incident.
- Impact
- The effect an incident has on business. Can be measured by the number of affected users or by how critical it is to the business in question.
- Category
- The category of the incident.
- Subcategory
- The category of the incident.
- Correlation ID
-
Connectors using the same Correlation ID will be associated with the same ServiceNow incident. This value determines whether a new ServiceNow incident will be created or an existing one is updated. Modifying this value is optional; if not modified, the rule ID and alert ID are combined as
{{ruleID}}:{{alert ID}}to form the Correlation ID value in ServiceNow. The maximum character length for this value is 100 characters.
Using the default configuration of {{ruleID}}:{{alert ID}} ensures that ServiceNow will create a separate incident record for every generated alert that uses a unique alert ID. If the rule generates multiple alerts that use the same alert IDs, ServiceNow creates and continually updates a single incident record for the alert.
- Correlation Display
- A descriptive label of the alert for correlation purposes in ServiceNow.
- Short description
- A short description for the incident, used for searching the contents of the knowledge base.
- Description
- The details about the incident.
- Additional comments
- Additional information for the client, such as how to troubleshoot the issue.
Configure ServiceNow
editServiceNow offers free Personal Developer Instances, which you can use to test incidents.