Elevating public sector cyber defense with AI-powered threat hunting
_(1).png)
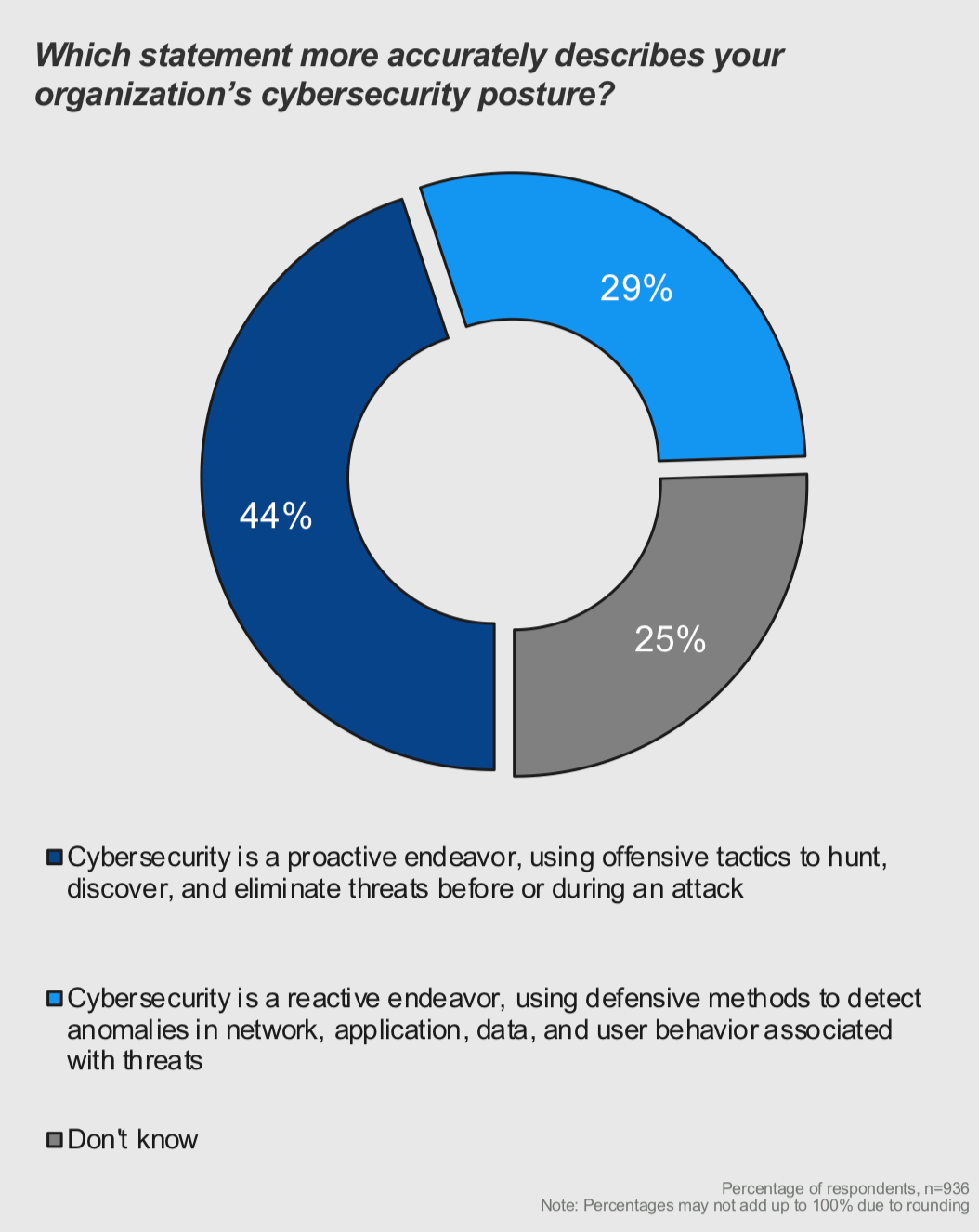
Public sector organizations face sophisticated, persistent threats — 38% of public sector organizations say their cyber resilience is insufficient compared to 10% of medium to large private businesses. With sensitive data and critical infrastructure at stake, agencies need tools that enable proactive detection and rapid investigation, all while keeping data inside a secure boundary.
Elastic Security — recently named a Visionary in the 2025 Gartner Magic Quadrant for SIEM — offers a comprehensive platform that empowers public sector organizations to strengthen their threat hunting capabilities. In this blog, we'll explore real-life examples, proven workflows, and AI-powered features that demonstrate how Elastic can be a game changer in threat hunting.
The necessity of threat hunting for public sector
Threat hunting is a proactive cybersecurity strategy that involves searching for threats that may have slipped past traditional security defenses. Unlike reactive measures, threat hunting focuses on anticipating, identifying, and neutralizing threats before they can cause harm. For public sector organizations, this proactive approach is essential to safeguarding sensitive data and maintaining the resilience of critical infrastructure.
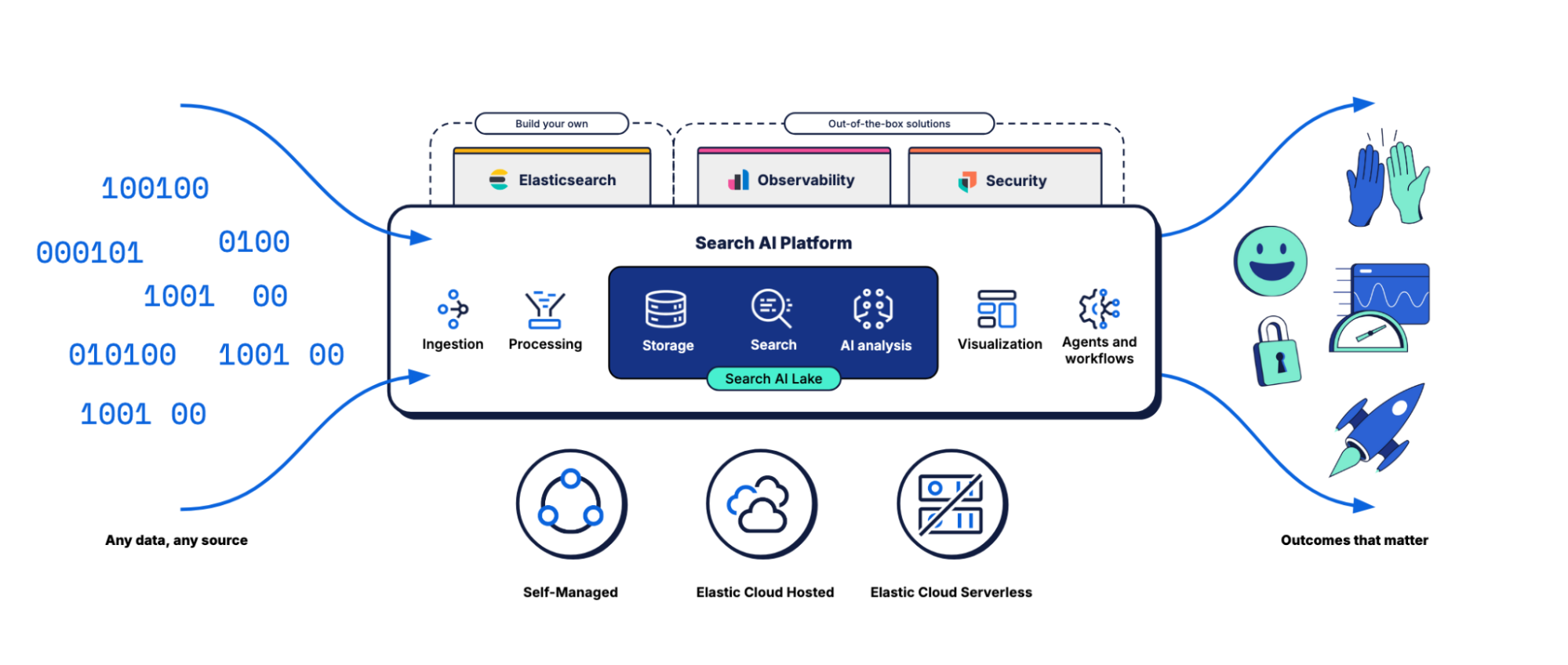
The technical backbone
Elastic provides a suite of tools that are ideal for proactive threat detection and investigation. Let's dive into the technical features that make it indispensable:
1. Distributed data mesh architecture: Elastic enables seamless ingestion and processing of massive data volumes from diverse sources. In the public sector, a distributed data mesh approach allows security teams to rapidly ingest, process, and analyze vast, diverse data streams from multiple agencies and regions. This ensures scalable, resilient, and real‑time threat detection across critical infrastructure.
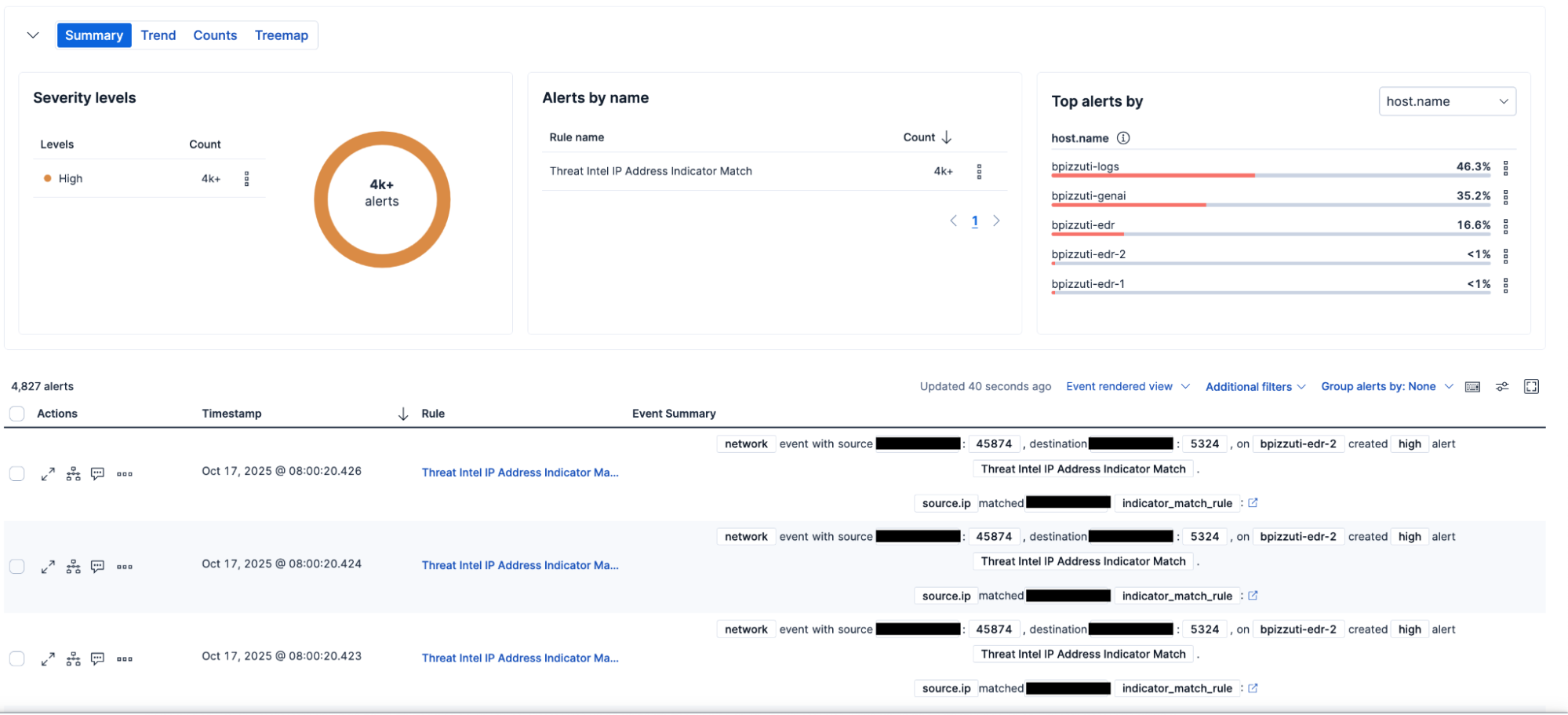
2. Kibana for visualization: Kibana, Elastic’s intuitive dashboard and visualization tool, enables public sector organizations to quickly spot anomalies, trends, and correlations in complex security data. This visibility empowers more informed threat hunting decisions across diverse systems, jurisdictions, and classification levels.
3. Elastic’s performance: For public sector agencies, Elastic’s powerful and trusted search capabilities make it possible to query and correlate vast, multisource datasets from different departments, jurisdictions, and critical infrastructure systems. This enables faster detection of coordinated attacks and significantly reduces response times to threats that could impact public safety or national security. Elastic Security has helped customers achieve the following outcomes:
36% reduction in annual risk exposure
90% reduction in security events and incidents
74% reclamation of full-time security employees' hours, allowing teams to focus on more strategic initiatives
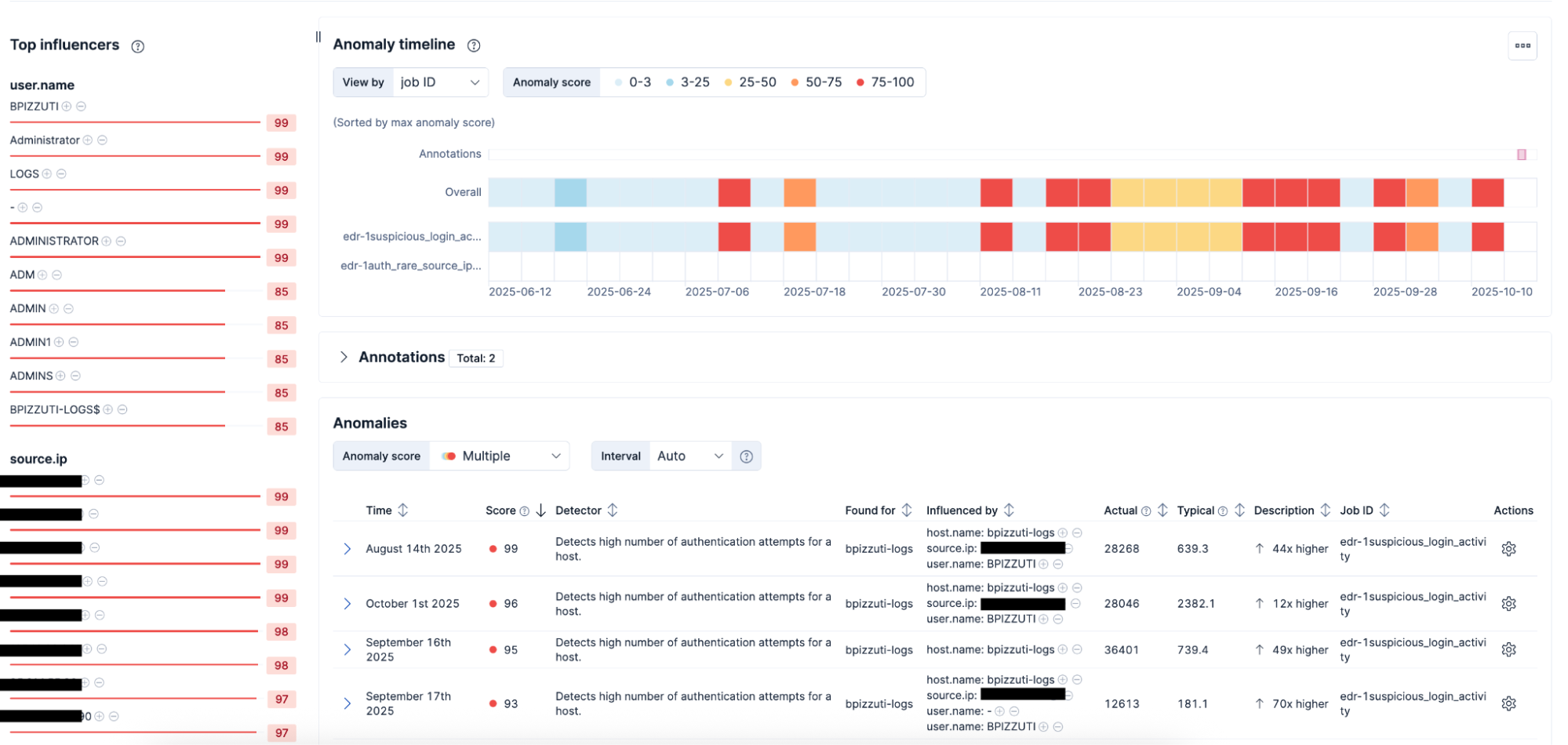
4. Machine learning (ML) for anomaly detection: Elastic’s ML capabilities automatically identify deviations from normal behavior, helping public sector security teams uncover threats, reduce false positives, and detect subtle attack patterns early. By continuously adapting to evolving environments, ML strengthens defenses for critical infrastructure and citizen services. In fact, customers have reported a 75% reduction in false positives with Elastic Security’s machine learning-powered anomaly detection.
Threat hunting with Elastic Security’s AI features
Elastic Security integrates AI-driven capabilities that accelerate detection, investigation, and response. Before exploring Elastic’s AI features, it’s important to understand the foundation behind Elastic Managed Large Language Model (LLM).
Elastic Managed LLM: Secure, scalable AI for security workflows
In addition to being able to implement your own LLM models, Elastic Managed LLM brings the power of generative AI directly into your security operations without the complexity of hosting or maintaining AI infrastructure.
Key features of Elastic Managed LLM include:
Fully managed and secure: Hosted within Elastic Cloud and designed to meet public sector compliance and security requirements. Note: All data is encrypted in transit. The LLM is configured for zero data retention — none of the prompts or outputs are stored by the model.
Optimized for security use cases: Fine-tuned to understand threat intelligence, log data, and incident response workflows
Seamless integration: Works natively with Elastic Security features like Attack Discovery and Elastic AI Assistant
Scalable performance: Handles large volumes of data and queries without impacting operational speed
With Elastic Managed LLM, public sector security teams can use advanced AI capabilities while maintaining control, privacy, and compliance.
Attack Discovery: Uncover coordinated threats with AI
Elastic’s Attack Discovery capability uses AI to reveal hidden links between events, exposing coordinated threats that might otherwise go unnoticed. By uncovering these connections early, public sector security teams can disrupt complex attacks, protect critical systems, and safeguard the services that communities depend on.
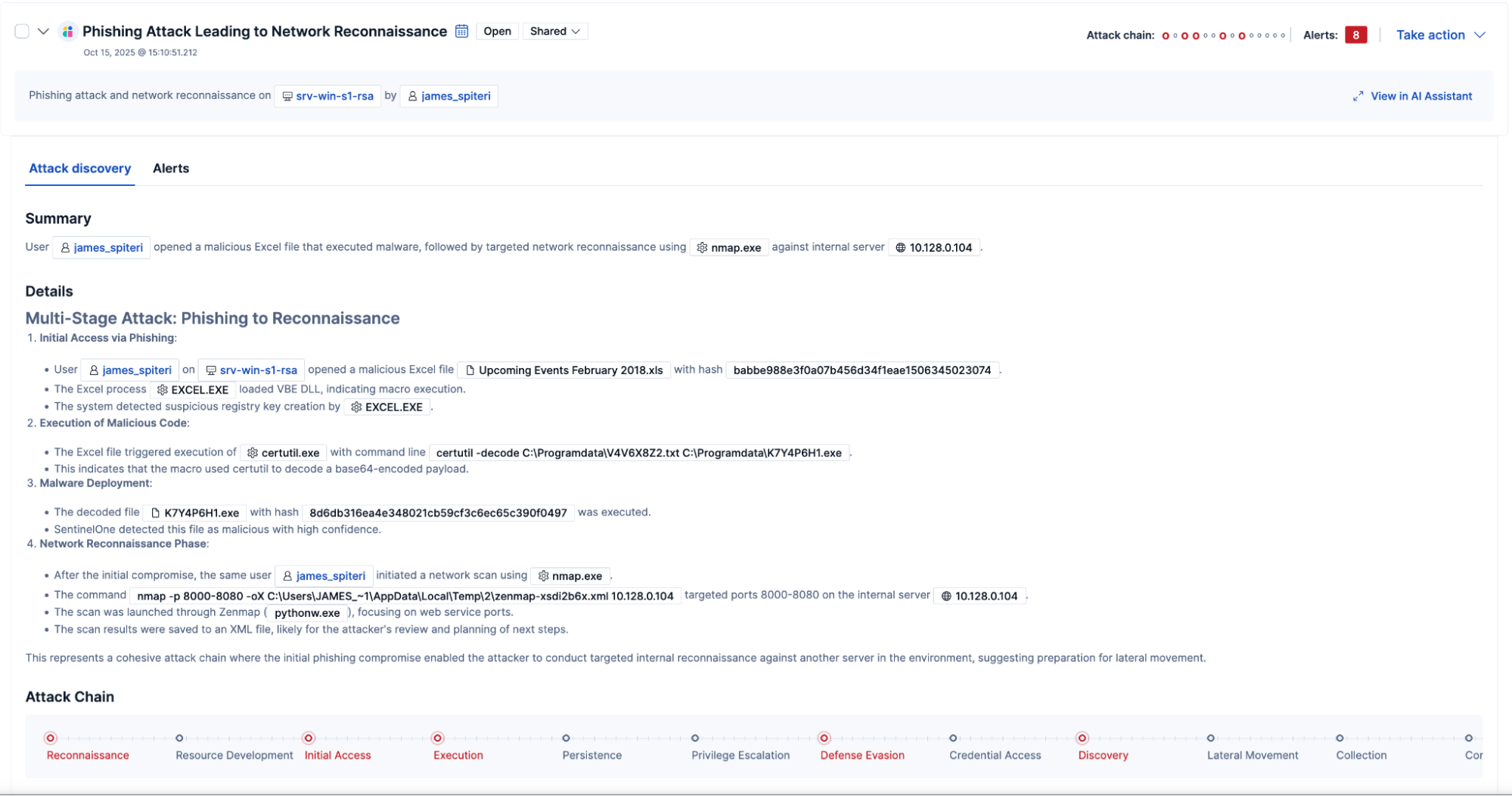
Elastic AI Assistant: Your copilot for security operations
Elastic AI Assistant gives public sector security teams the ability to turn complex data into clear, actionable intelligence. By guiding investigations, highlighting suspicious activity, and providing instant context, it helps analysts move from detection to resolution faster — strengthening the defense of critical infrastructure and the services citizens rely on every day.
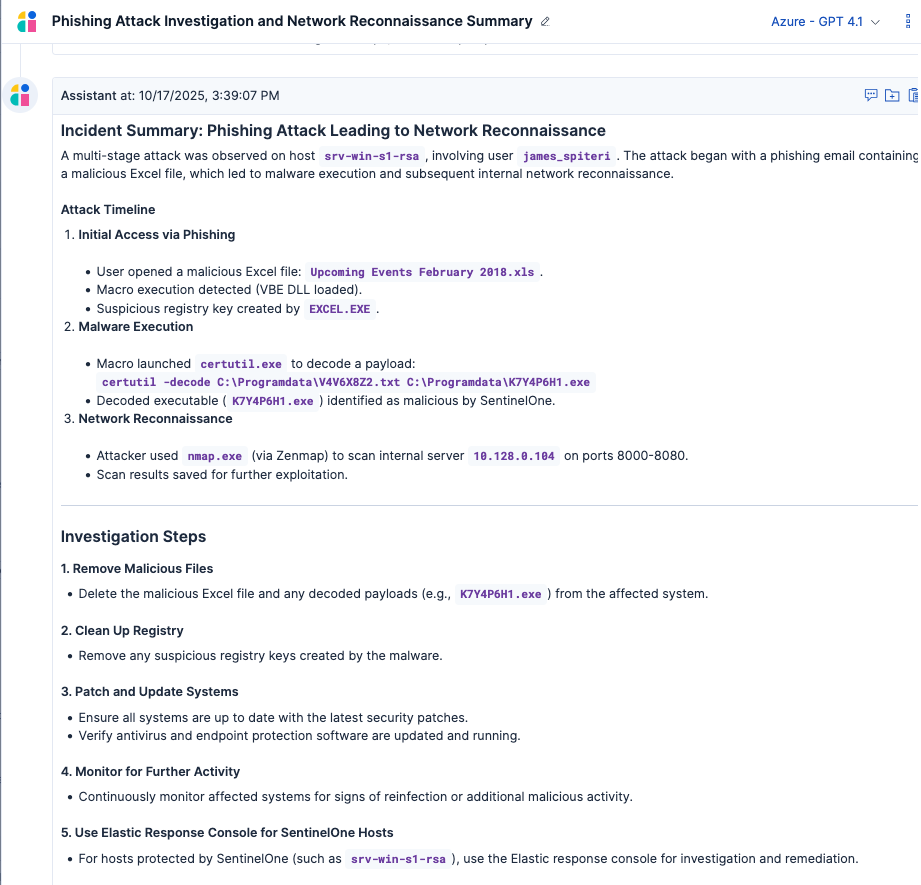
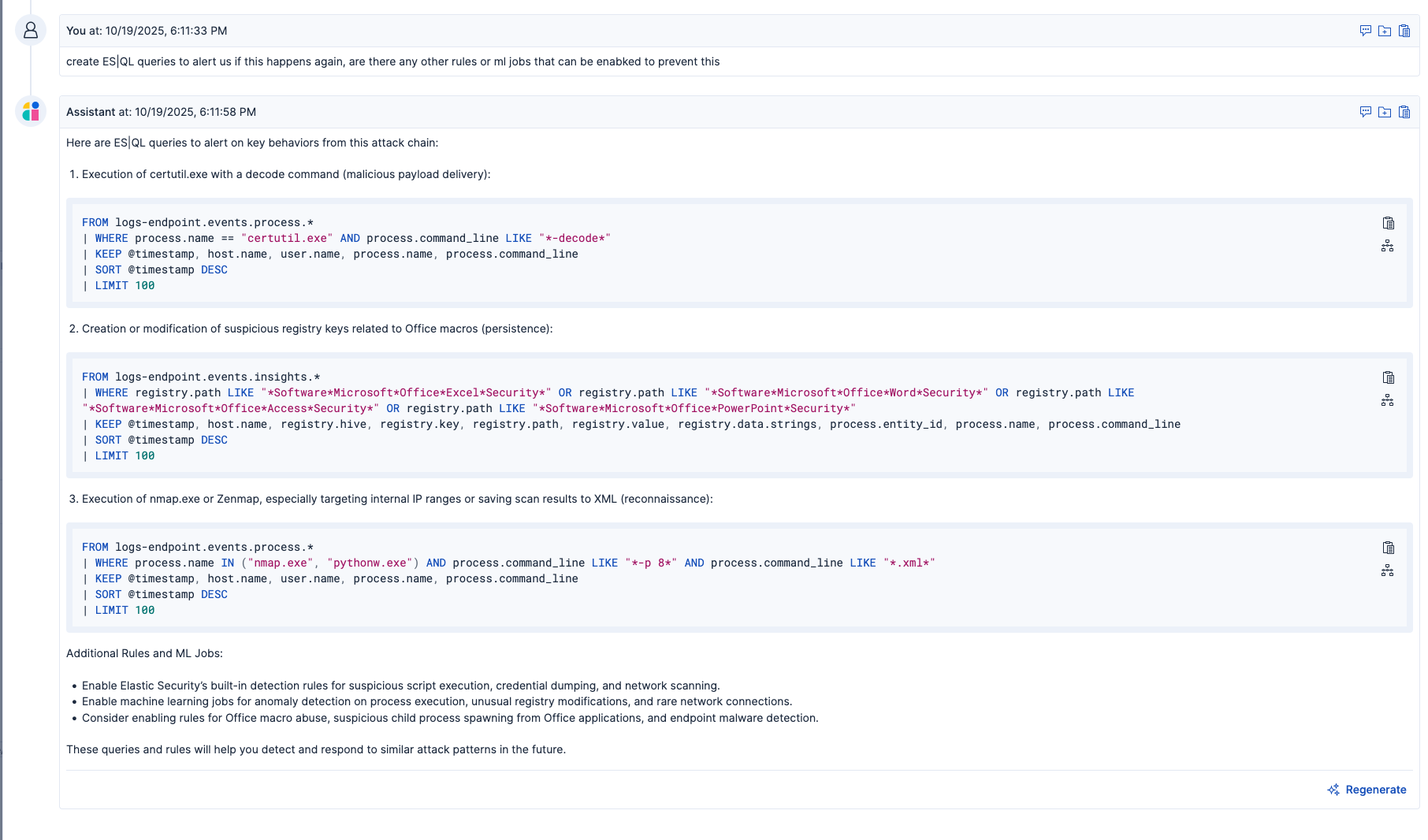
How Elastic detects and responds to coordinated phishing attacks
Here’s how Elastic’s capabilities work together to detect and respond to a coordinated phishing attack.
1. ML flags unusual logins: Your ML job detects a spike in failed logins from a foreign region followed by a sudden rise in successful logins for the same accounts within minutes.
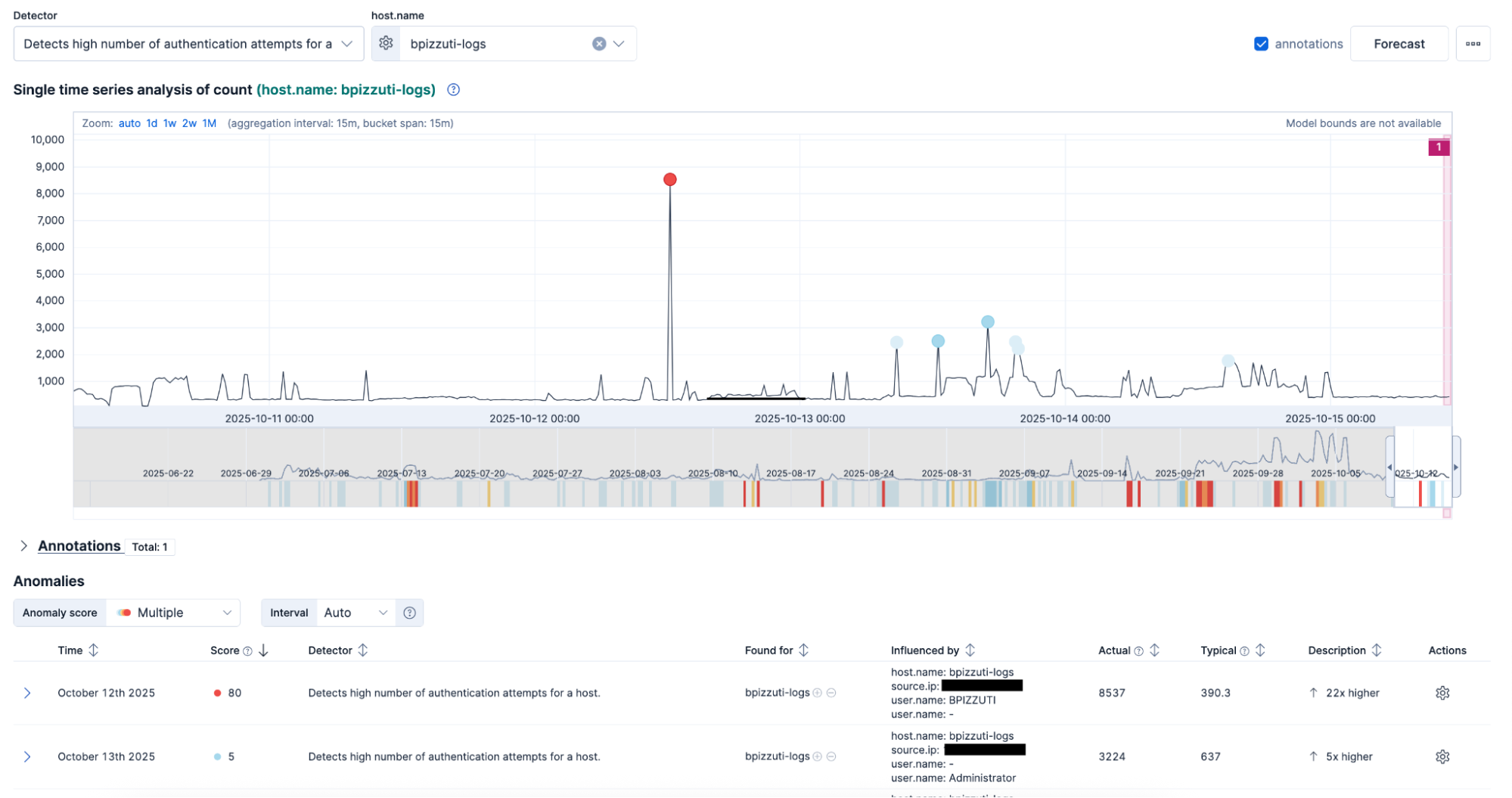
2. Timeline and dashboards confirm a pattern: In Kibana, a timeline view reveals coordinated login attempts across multiple users and endpoints. You identify common user agents and overlapping IP ranges, confirming that the activity is part of a broader organized campaign.
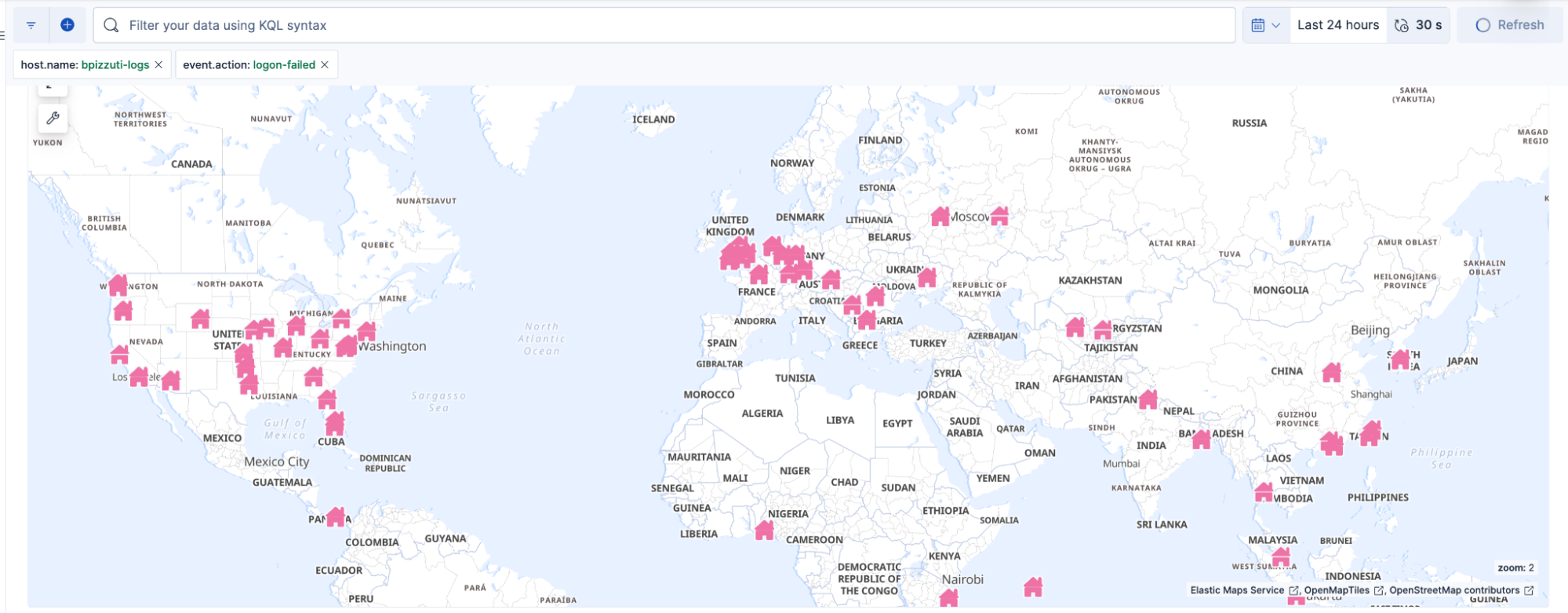
3. Attack Discovery connects the campaign: Attack Discovery clusters the failed and successful logins, related email gateway alerts, and endpoint sign-ins into a single, correlated incident. It identifies a likely phishing lure, credential harvesting activity, and subsequent access to internal resources.
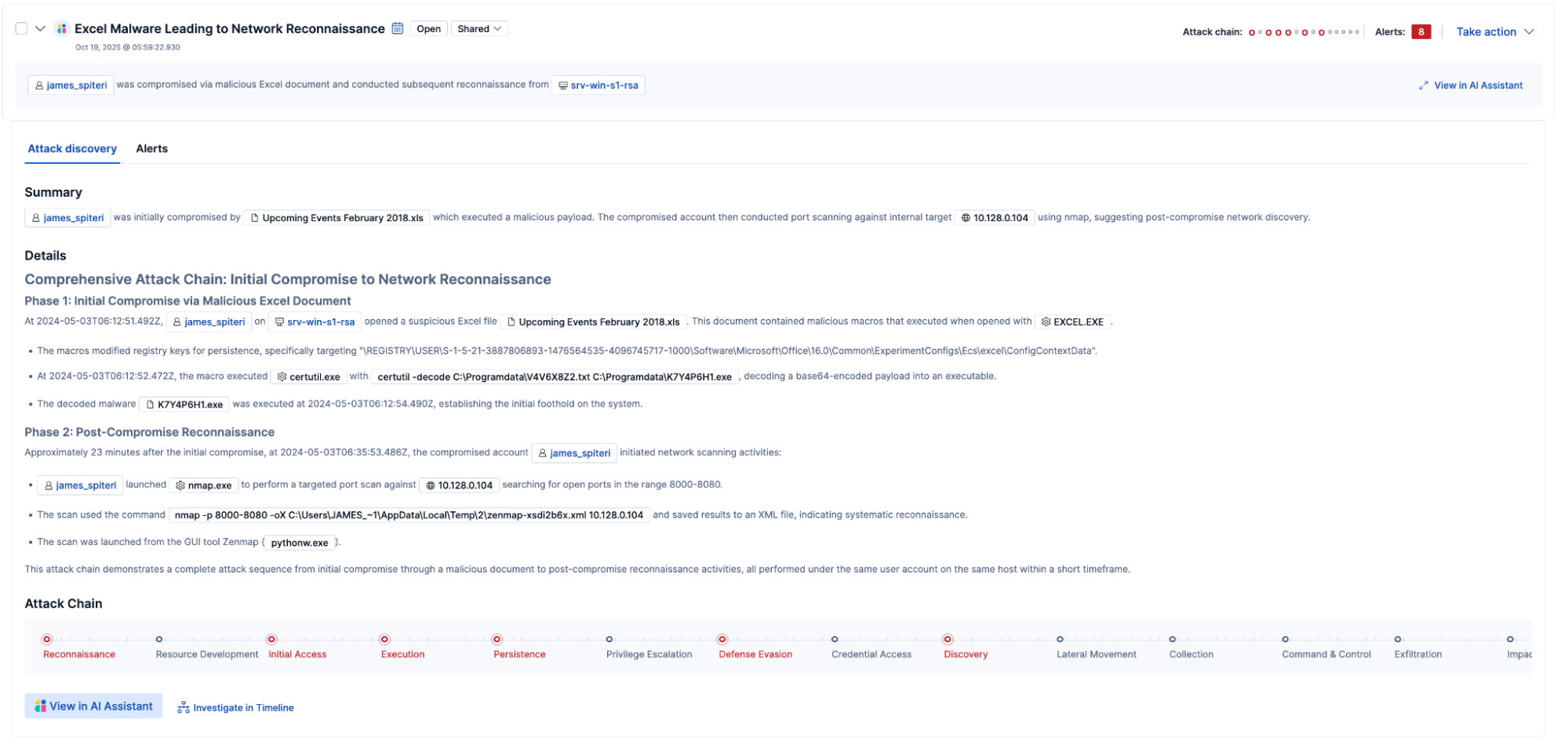
4. Elastic AI Assistant accelerates investigation: The assistant generates a structured incident brief detailing impacted accounts, entry vectors, time windows, and risky follow-on activity. It also recommends containment actions, such as forced password resets, session revocation, and review of multifactor authentication (MFA) enrollment.
In addition, the Elastic AI Assistant is deeply integrated with your organization’s context. You can use it to query past incidents, review firewall configurations, and access organization-specific operational data, ensuring that every recommendation and insight is relevant to your unique environment.
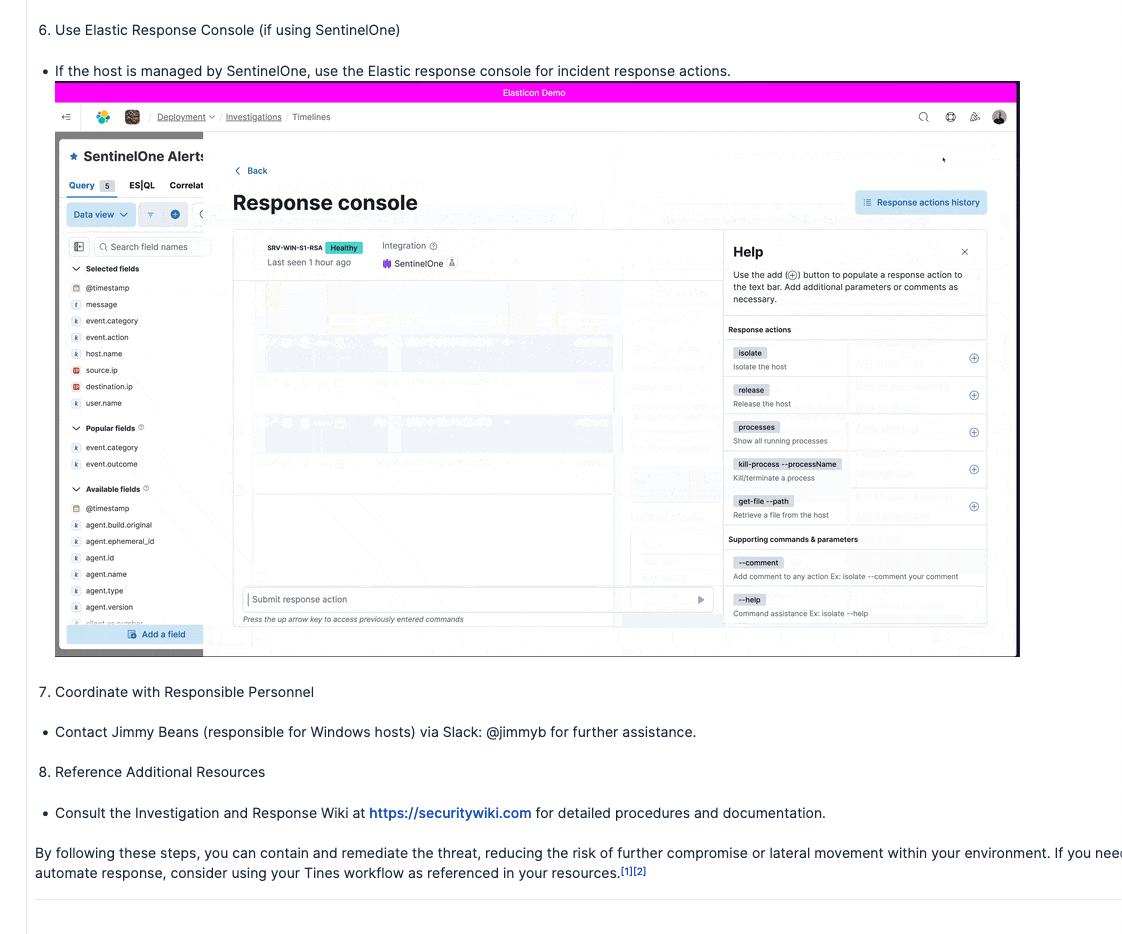
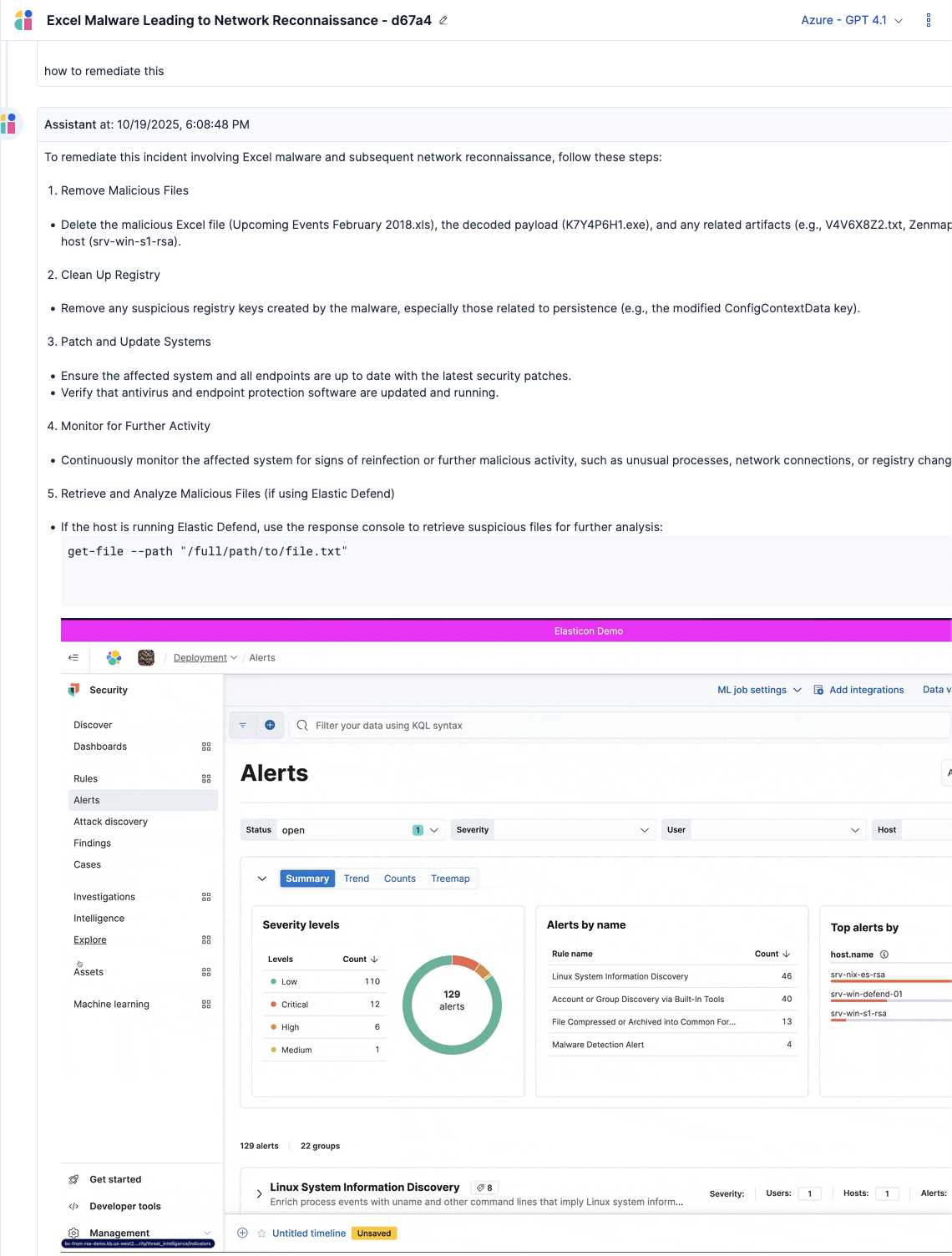
5. Analysts validate and contain: Using Discover, analysts verify Elastic AI Assistant’s recommendations by reviewing MFA bypass events, newly created inbox rules, and abnormal OAuth grants. Based on this information, security analysts can disable compromised accounts, revoke tokens, quarantine affected endpoints, and block malicious IPs.
6. Investigation concludes with a formal writeup: The investigation concludes with a concise report that covers scope, blast radius, current status, and recommended next steps. This summary provides a clear record for compliance, executive review, and continuous improvement of security posture.
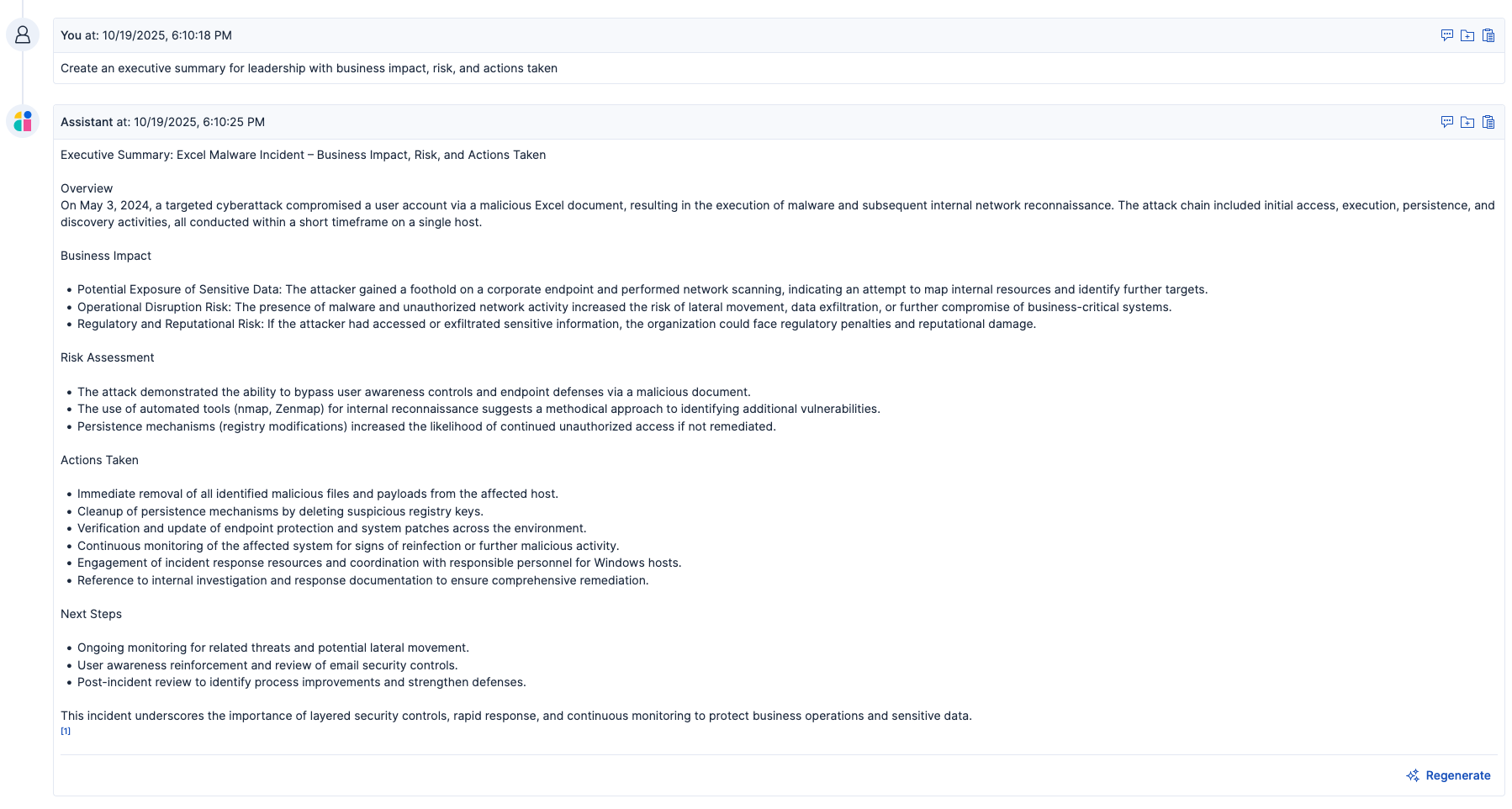
7. Analysts augment processes for future detection: Analysts tag relevant artifacts, create new detection rules for the lure indicators, and tune ML jobs with new examples to improve accuracy. They also track time to detect and time to respond as key metrics.
Key takeaways for Elastic threat hunting in public sector
Elastic Security provides a comprehensive, AI-enhanced platform for public sector organizations to elevate their threat hunting capabilities. By combining distributed data mesh architecture, powerful search, advanced ML, and AI features like Attack Discovery and Elastic AI Assistant, agencies can proactively identify and mitigate threats — protecting sensitive data and critical infrastructure while maintaining public trust.
Elastic Managed LLM is designed to meet the unique needs of public sector organizations. It combines advanced AI capabilities with the security, compliance, and scalability required for government environments. Operating within Elastic’s secure architecture, it enables natural language querying, contextual threat analysis, and automated investigation assistance without exposing sensitive data to external systems. By tailoring the model to handle diverse, multisource datasets common in public sector threat hunting, Elastic ensures agencies can use AI to accelerate detection and response while maintaining strict data governance and regulatory compliance.
Related resources:
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos or registered trademarks of Elasticsearch B.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.