From endpoint to XDR: Operationalize Jamf Protect data in Elastic Security
Enhance your threat detection, investigation, and response capabilities by integrating Jamf Protect macOS data within Elastic Security.
.jpg)
Security teams often struggle to detect and respond to macOS threats with endpoint data alone. The integration with Jamf Protect changes that.
Jamf Protect delivers rich macOS telemetry and built-in protections like Threat Prevention and Network Protection, powered by Jamf Threat Labs. By unifying this endpoint intelligence with Elastic Security’s AI-driven analytics, threat detection, and response capabilities, organizations gain comprehensive visibility across endpoints, networks, cloud, and identity systems.
This integration eliminates data silos, reduces tool sprawl, and helps teams investigate and respond to threats faster, all within a single platform. With detection rules from hundreds of sources (backed by Elastic Security Labs), real-time alerts, and powerful Elastic Defend response actions, defenders can quickly connect Jamf Protect telemetry to broader attack campaigns and stop threats before they escalate.
Together, Elastic and Jamf provide a modern, scalable approach to securing macOS devices as part of a holistic XDR strategy.
Get detailed security insights for macOS devices with Jamf Protect
The Jamf Protect integration enables security teams to ingest and normalize macOS endpoint telemetry directly into Elastic Security. Jamf Protect generates detailed security insights for macOS devices, including endpoint alerts on suspicious behavior, system and process activity data, and telemetry that helps identify macOS-specific threats and vulnerabilities. But this integration goes beyond just alert ingestion; it also provides detailed process telemetry, configuration change events, and endpoint context that analysts can pivot during investigations.
Jamf Protect data normalized into Elastic Common Schema
Once ingested, all Jamf Protect data is normalized into the Elastic Common Schema (ECS), making it instantly compatible with Elastic Security detection rules, dashboards, and analytics. ECS alignment ensures that Jamf Protect telemetry can be correlated with other data sources across the enterprise, providing a unified view of macOS activity in the broader context of your environment.
For example, analysts can filter and pivot on ECS fields using the event.module field to distinguish Jamf Protect alerts from other endpoint or data sources.
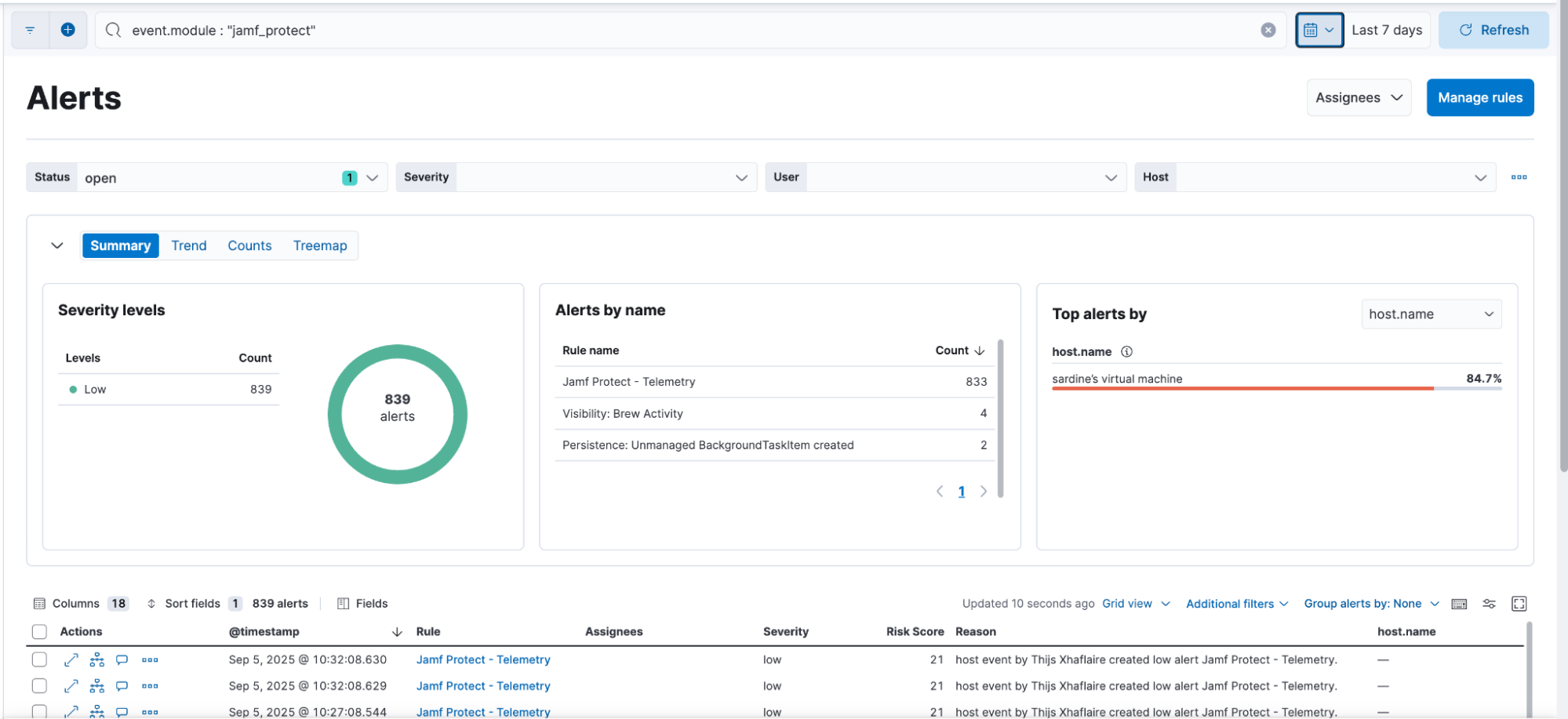
Threat detection with Elastic's AI-driven security analytics
Elastic Security provides prebuilt detection rules allowing security teams to quickly use their Jamf Protect macOS endpoint data without needing to build their own analytics from scratch.
Elastic's machine learning jobs can detect anomalies in Jamf Protect telemetry and identify suspicious behaviors that traditional rule-based detections may miss. Analysts can also create custom rules specific to their organization's environment to enrich Jamf Protect alerts with additional security context. Using Elastic's open, extensible data model allows security teams to apply unified detections across endpoints, networks, cloud workloads, and identity systems, enabling true cross-domain threat detection.
Investigate Jamf Protect data with Elastic Security
Elastic AI Assistant provides AI-driven investigations for your security team
Elastic AI Assistant extends investigations with generative AI that acts as both a guide and a knowledge base for security teams. Instead of limiting its role to querying data, the assistant helps analysts understand alerts, determine next steps, and even identify who in the organization should take action.
For example, when Jamf Protect raises an alert about suspicious persistence activity on a macOS device, an analyst can ask the assistant: “What does this alert mean, and how should I respond?” The assistant explains why the alert was generated, highlights the potential impact, and suggests remediation steps, such as isolating the endpoint or searching for related indicators of compromise across the fleet.
Analysts of any skill level can rely on the assistant for both explanations and decision-making guidance, ensuring that alerts are not just investigated but resolved quickly and effectively.
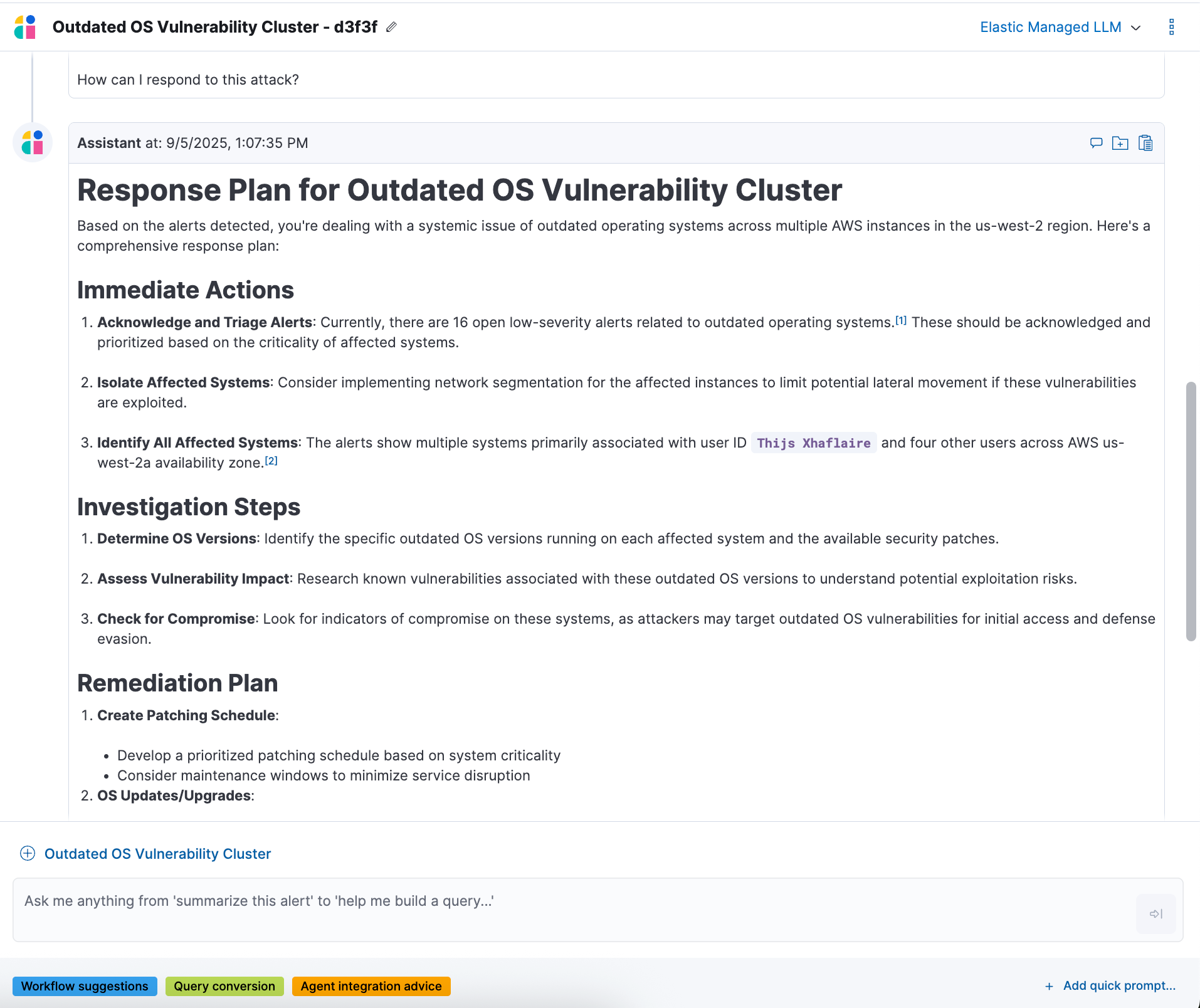
The AI Assistant can also integrate with custom knowledge sources, such as internal playbooks, wikis, or past incident reports. This allows analysts to ask environment-specific questions like “Who in our IT team is responsible for handling macOS device remediation?” By searching indexed organizational knowledge, the assistant provides answers tailored to each customer’s practices and threat landscape.
Elastic Managed LLM makes AI-driven context available from day one
Now, with the introduction of the Elastic Managed LLM, these capabilities are even more accessible. The Elastic Managed LLM is the default large language model (LLM) connector available and provides immediate access to generative AI features without requiring any external setup, manual connector configuration, or API key management. Analysts can start using natural-language investigation workflows out of the box, reducing friction and ensuring that AI-driven context is available from day one.
Attack Discovery automates threat correlation and context
Elastic Security’s Attack Discovery automates one of the most time-consuming aspects of threat investigation: correlating isolated signals into a coherent picture of an attack campaign. Teams can schedule attack discoveries to continuously analyze incoming data, including Jamf Protect telemetry, and surface patterns that suggest coordinated attacker behavior and map it to MITRE ATT&CK® tactics and techniques.
For example, a Jamf Protect alert about a suspicious process execution on a macOS device might be linked with anomalous network activity from the same host and unusual authentication attempts in an identity provider.
By connecting these dots automatically, Elastic helps analysts move from single-event investigation to campaign-level detection. This capability ensures that macOS activity is not viewed in isolation but rather in the context of the larger attack surface, giving defenders the visibility they need to anticipate the attacker’s next move.
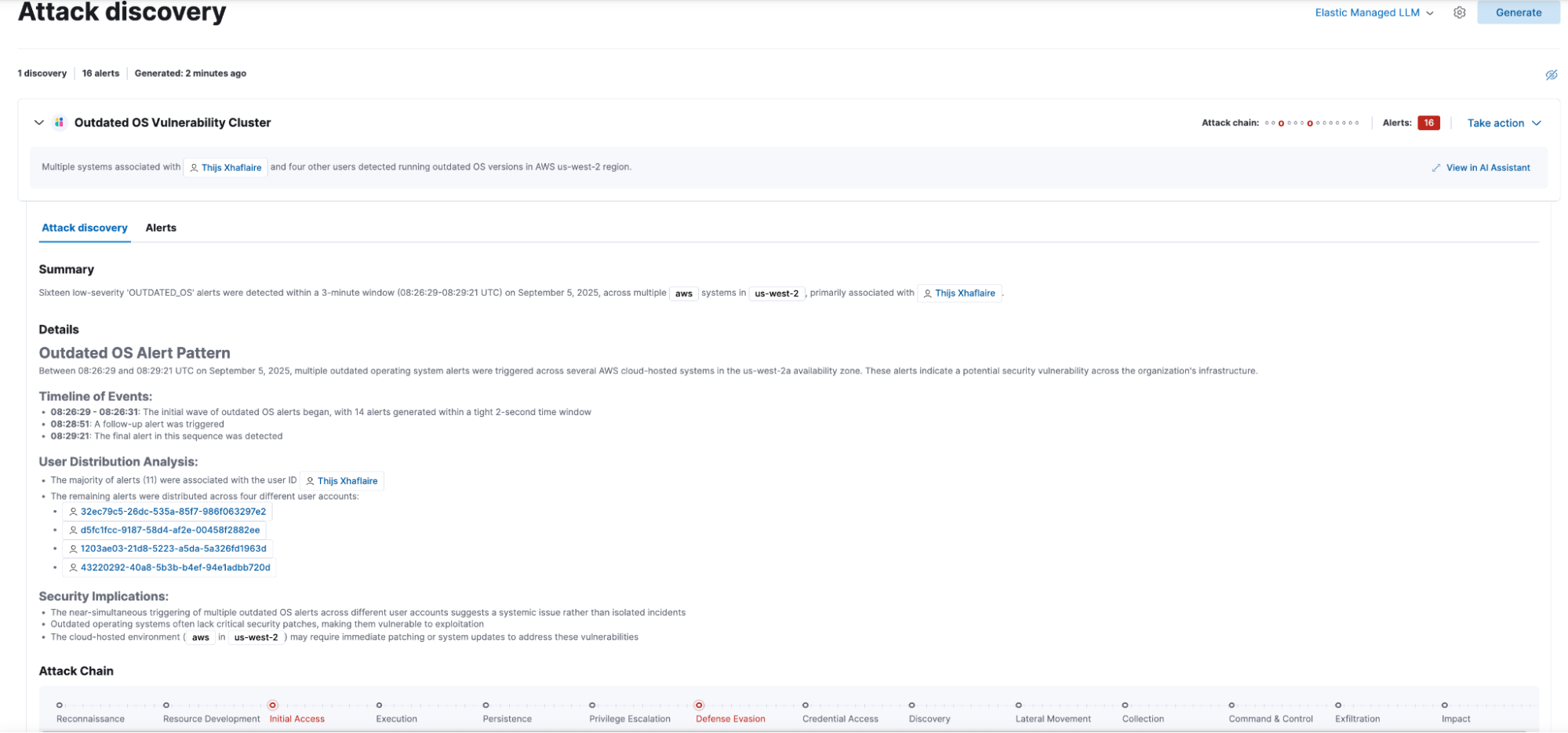
Elastic Security timelines expands Jamf Protect data in full view
A timeline in Elastic Security transforms raw telemetry into a clear, event-driven narrative. Analysts can take an alert generated by Jamf Protect and expand it into a full view of related process activity, file changes, or configuration modifications on the same host. This allows defenders to see not only the suspicious process flagged by Jamf Protect but also investigate associated events, what network connections were established, and if there were any files modified, among others. By stitching these signals together, analysts can reconstruct the attack sequence on a macOS device and correlate it with activity happening on other endpoints, servers, or cloud workloads. This reduces the guesswork and shortens the time to the root cause.
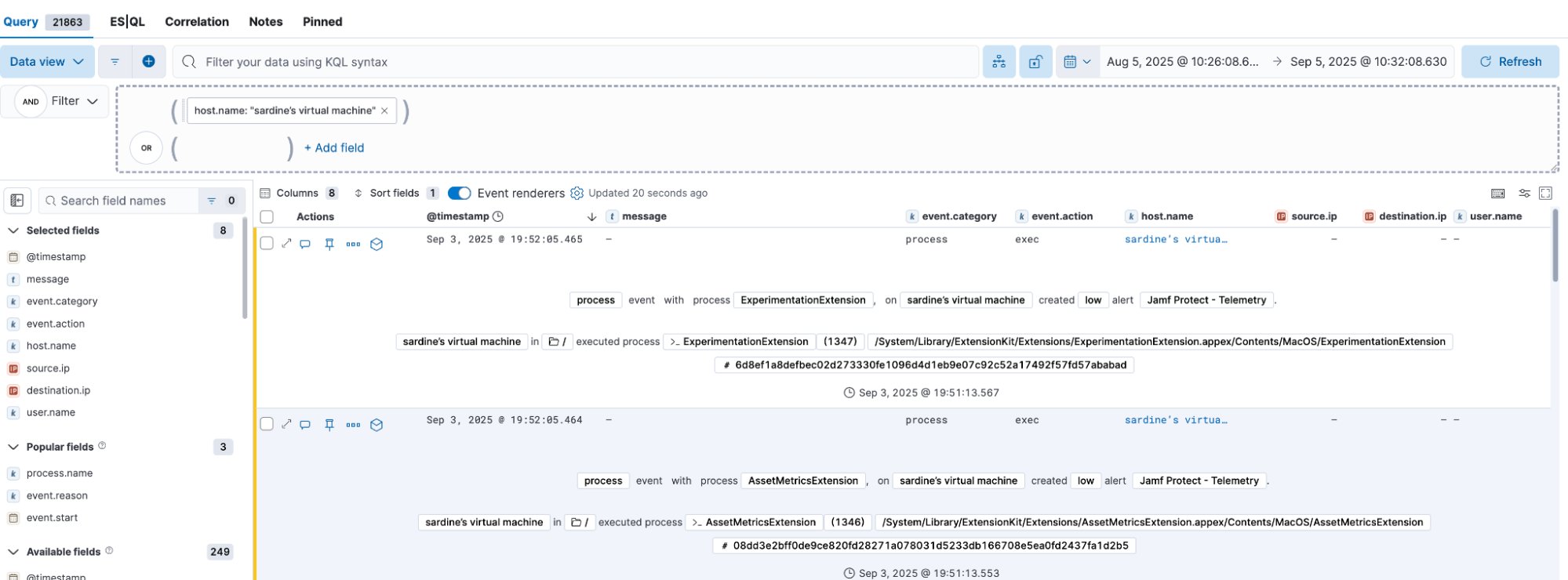
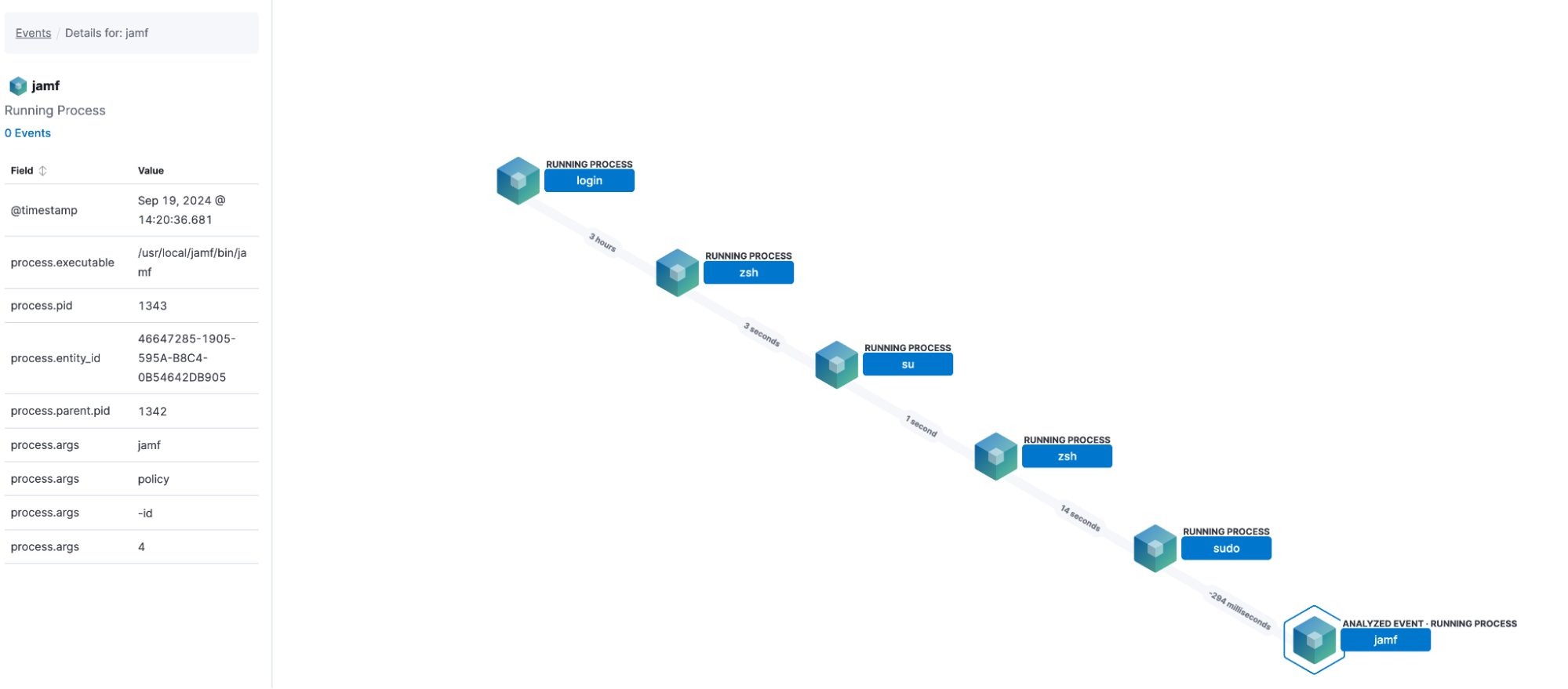
Visualize Jamf Protect macOS-specific data with Elastic Security analyzer
Elastic’s visual event analyzer gives analysts a powerful way to visually explore Jamf Protect alerts and their related process activity. When a suspicious event is ingested, the Analyzer view automatically maps the process tree, showing parent and child relationships, command-line arguments, and file or network interactions. This graphical representation makes it easy to spot unusual behaviors, such as privilege escalation or persistence techniques, and quickly pivot into deeper investigation. By enriching Jamf Protect telemetry with additional context from other data sources, analyzer helps analysts validate whether an alert represents an isolated anomaly or part of a broader attack sequence.
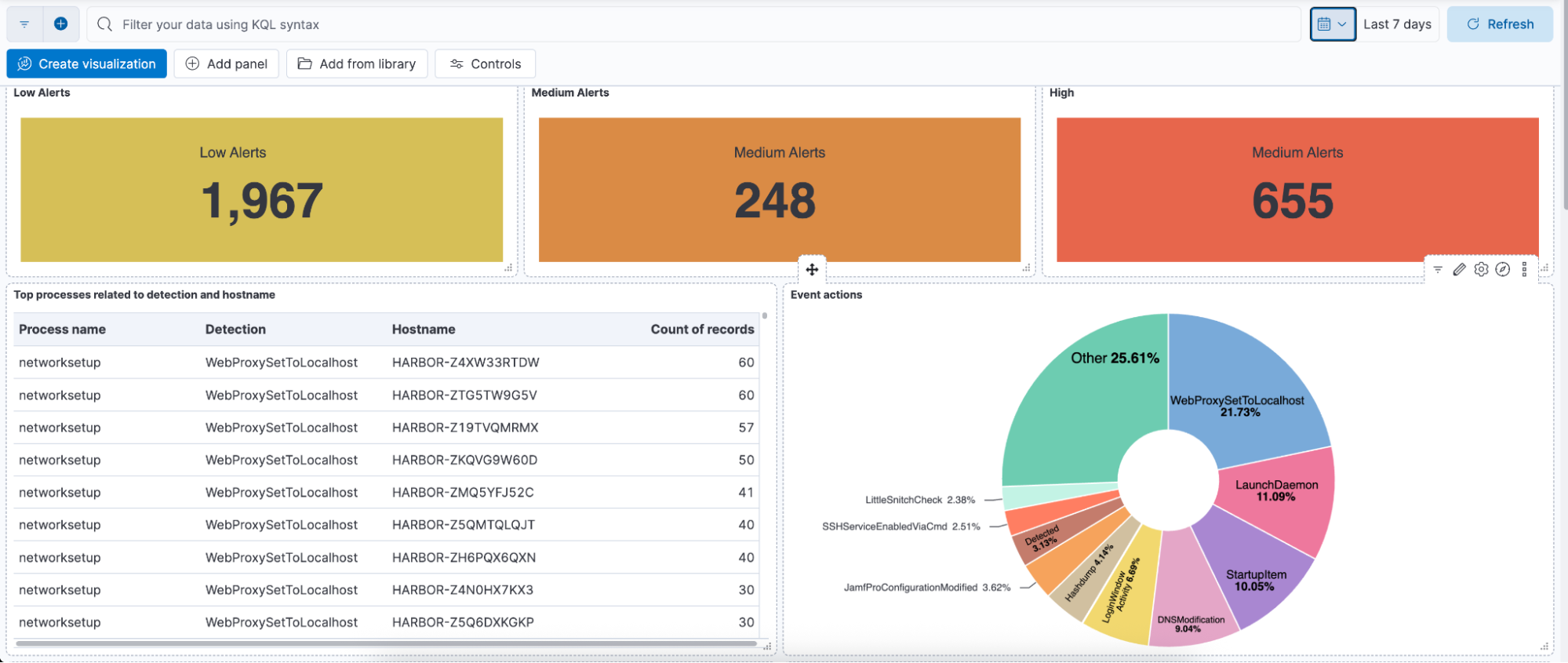
Interactive dashboards and visualizations
Elastic Security provides prebuilt Kibana dashboards for endpoint data and gives teams the flexibility to build their own custom views. Jamf Protect telemetry ingested into Elastic can be visualized alongside Windows, Linux, network, and cloud signals to give analysts a true cross-environment perspective.
For example, a custom dashboard might highlight macOS process execution trends, correlate them with suspicious login attempts from identity providers, and overlay network connection data for context. This type of visualization turns macOS telemetry into a powerful hunting tool, helping analysts quickly spot anomalies that would be difficult to detect in raw log format. Dashboards also support operational needs, such as tracking endpoint coverage, identifying outdated devices, or monitoring for recurring attack patterns.
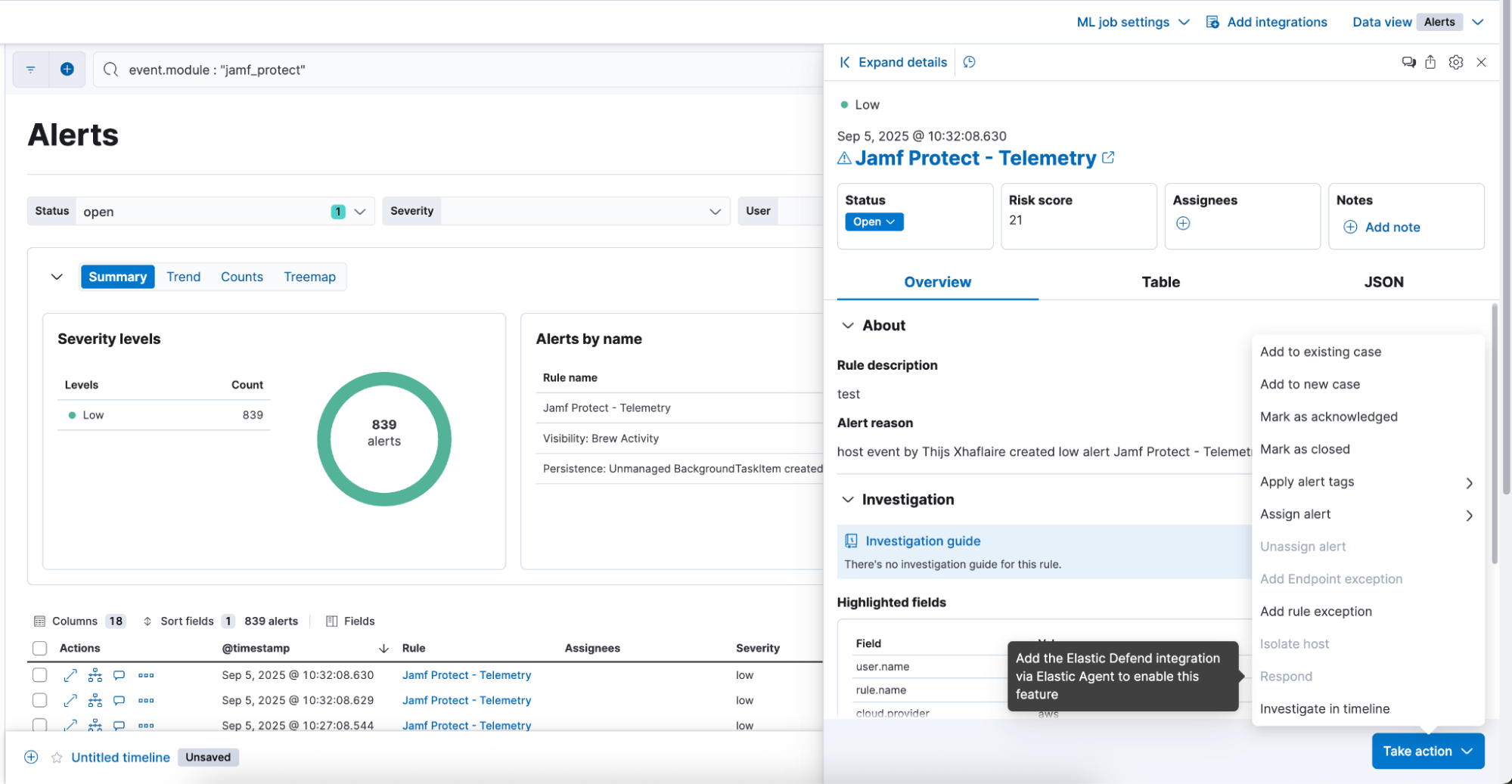
Elastic Defend delivers full response across macOS endpoints
While Jamf Protect provides strong macOS visibility, response capabilities are limited. Elastic Defend can be layered on top to deliver full response across macOS endpoints.
With Elastic Defend, analysts can isolate or release macOS devices, acquire files, see a process list, kill malicious processes, or execute remote scripts and commands directly from the Elastic Response Console. This closes the gap between detection and remediation, ensuring teams can act quickly and decisively.
By combining Jamf Protect’s macOS coverage with Elastic Defend’s advanced response actions, security teams gain complete visibility and remediation capabilities across their Apple fleet. At the same time, Elastic Defend also responds on Windows and Linux to ensure a true XDR experience.
Long-term visibility and advanced analytics
Storing Jamf Protect data in Elastic Security provides more than immediate detection. Cross-cluster search (CCS) provides teams the ability to hunt and analyze threats over longer time frames with the option to correlate it across multiple Elastic deployments. With Elastic’s scalable architecture, defenders can retain macOS telemetry in a cost-effective way, using searchable snapshots to store historical data in low-cost object storage. This ensures investigations are not limited by retention windows and allows defenders to revisit past activity when new threat intelligence becomes available.
This cost-effective, long-term data retention is especially important for macOS environments, where advanced threats may stay undetected for months before indicators are uncovered. With Elastic, analysts can query historical Jamf Protect data, enrich it with new detection rules, and with Elastic’s Search AI Lake, apply advanced search and machine learning models to identify subtle attack patterns that were previously missed.
Reduce blind spots with Elastic Defend
In hybrid environments, many organizations have deployed Jamf Protect only on some endpoints. Elastic Security provides a unified approach by allowing teams to deploy Elastic Defend on endpoints not covered by Jamf Protect. This ensures consistent security monitoring, regardless of endpoint coverage, and enables defenders to analyze all endpoint telemetry within the same workflow.
Elastic Defend and Jamf Protect together provide comprehensive endpoint protection, while allowing security teams to investigate and respond using a single platform. Analysts can use the same detection rules, correlation logic, and automated workflows to simplify security operations in diverse environments, regardless of whether they are ingesting Jamf Protect alerts or collecting data from Elastic Defend agents.
Make Jamf Protect part of your XDR strategy
Jamf Protect provides critical visibility into macOS devices, and Elastic Security amplifies its value by operationalizing that telemetry within a broader XDR platform. By ingesting Jamf Protect data into Elastic Security, defenders gain AI-driven analytics, scalable storage, advanced investigation tools, and enterprise-grade response capabilities.
Elastic Security transforms Jamf Protect from a standalone endpoint product into a key piece of an integrated defense strategy, empowering security teams to stop threats at scale. Learn more about the Jamf Protect integration, or start a free trial of Elastic Security to experience the benefits.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.