Introducing Elastic SIEM
Editor’s Note — August 19, 2020: The Elastic SIEM solution mentioned in this post is now referred to as Elastic Security. The broader Elastic Security solution delivers SIEM, endpoint security, threat hunting, cloud monitoring, and more. If you're looking for more specific information on Elastic Security for SIEM use cases, visit our SIEM solution page.
We are excited to announce the arrival of Elastic SIEM — the first big step in building our vision of what a SIEM should be. The launch of Elastic SIEM builds on the momentum and success that the Elastic Stack already enjoys in the security analytics market. The initial launch of Elastic SIEM introduces a new set of data integrations for security use cases, and a new dedicated app in Kibana that lets security practitioners investigate and triage common host and network security workflows in a more streamlined way.
Oh, and it’s available for free to our users as a part of our default distribution. Elastic SIEM is being introduced as a beta in the 7.2 release of the Elastic Stack and is available immediately on the Elasticsearch Service on Elastic Cloud, or for download.
A journey that started years ago
Over the past few years, the Elastic Stack has become a popular choice with security practitioners for protecting their systems and data from cyber threats. Bell Canada and Slack use the Elastic Stack for security analytics. Cisco Talos has Elasticsearch at the heart of their threat hunting program. OmniSOC, a shared cybersecurity operations center built by the Big Ten Academic Alliance, and Oak Ridge National Laboratory chose to use the Elastic Stack as the core of their SIEM solutions. And we've seen open source projects like RockNSM, HELK, and others form around the Elastic Stack to support security operators.
We were excited to see what a great fit the Elastic Stack was for security data. We were inspired by the community that formed around these use cases and invested in building foundational features to better serve them — as we have done for other solutions like logging and APM. Starting with the collection of security information and events, we expanded the set of host-based security data we collect with Filebeat, Winlogbeat, and Auditbeat. We also expanded the range of network-based security event collection by adding integrations with popular network monitoring and Intrusion Detection Systems (IDS) such as Bro/Zeek and Suricata.
As we broadened the set of data integrations, we realized how important it is to have a common way to represent data across different sources. We spent the last 18 months, along with our community and partners, developing the Elastic Common Schema (ECS) — an extensible field mapping specification that makes it easy to normalize data from disparate sources to enable cross-source correlation, search, and analysis.
With easy ways to collect a number of security data sources and a common schema in which to store them, the next obvious step in our journey was a user interface that brought these pieces together in a single place and delivered a user experience that was tailored to the needs of security practitioners.
Say heya to Elastic SIEM!
Introducing Elastic SIEM
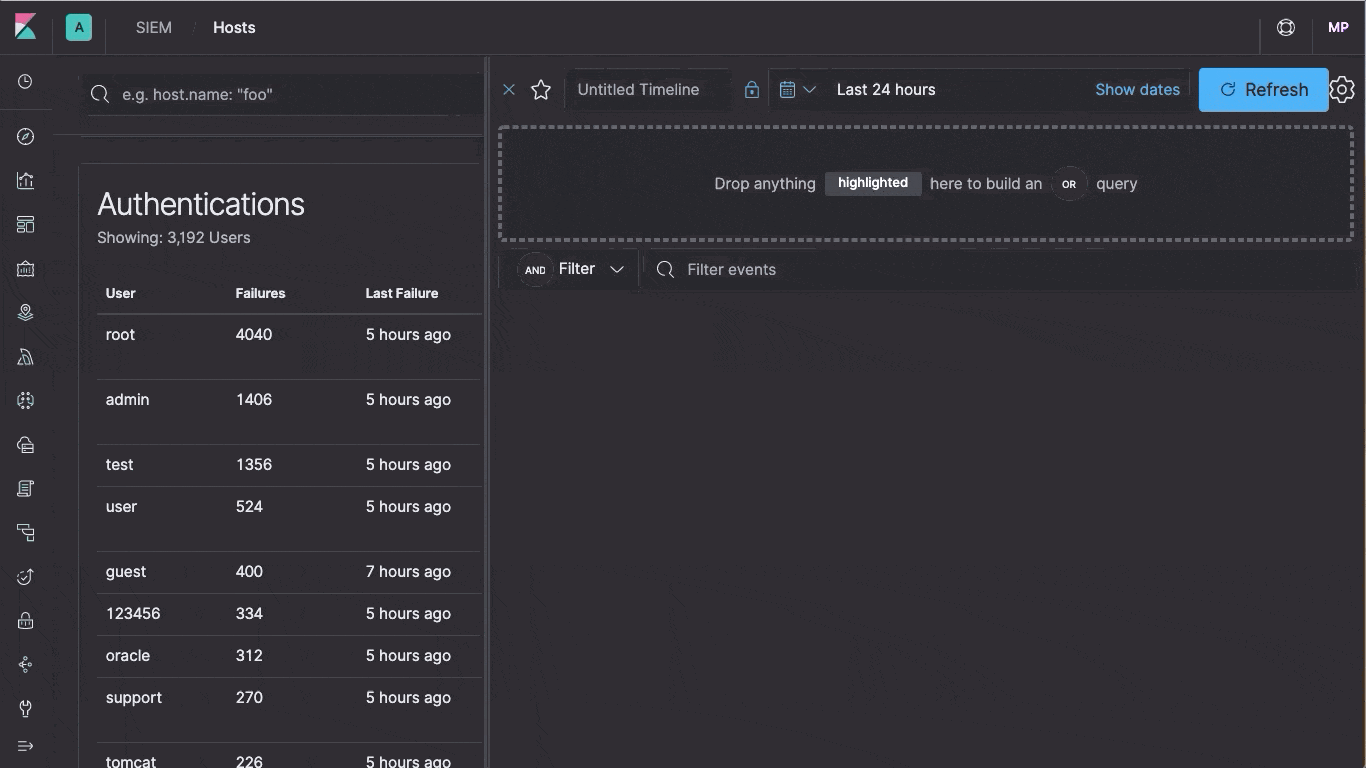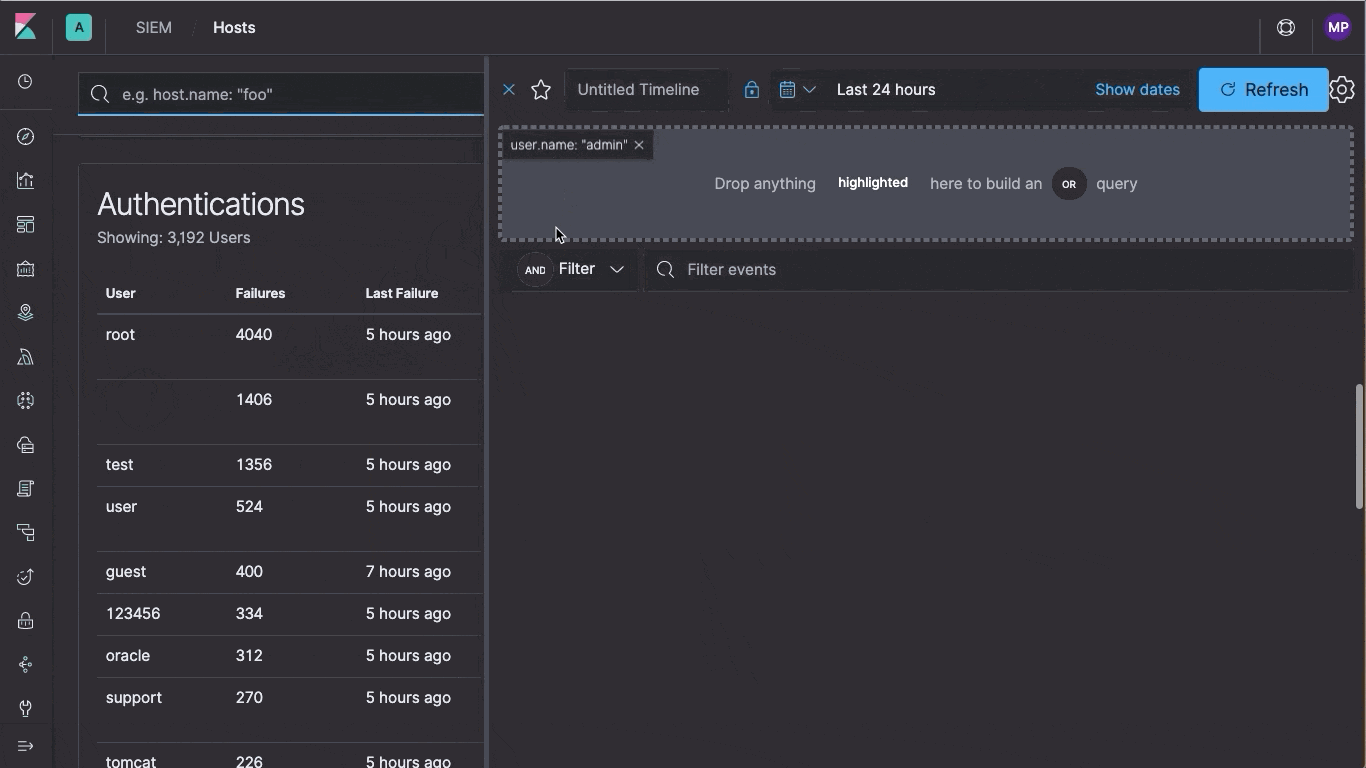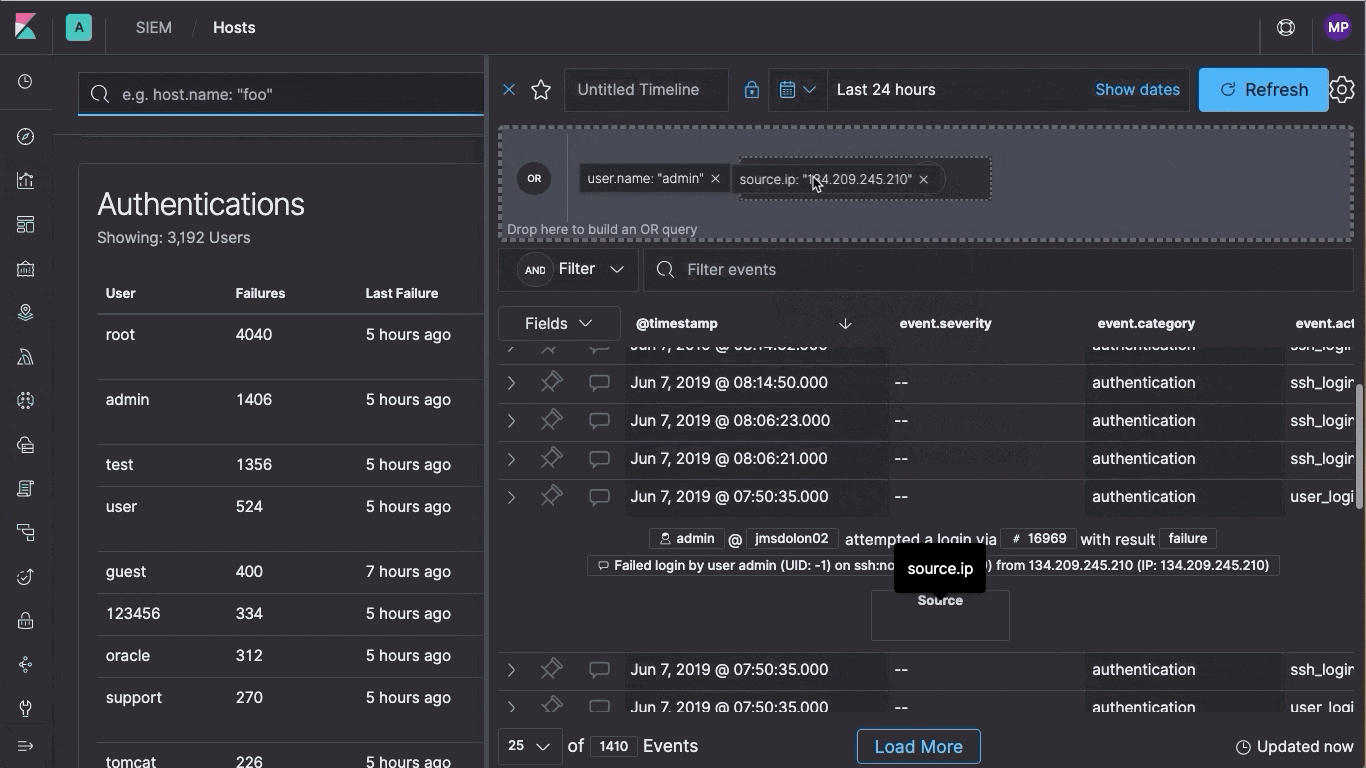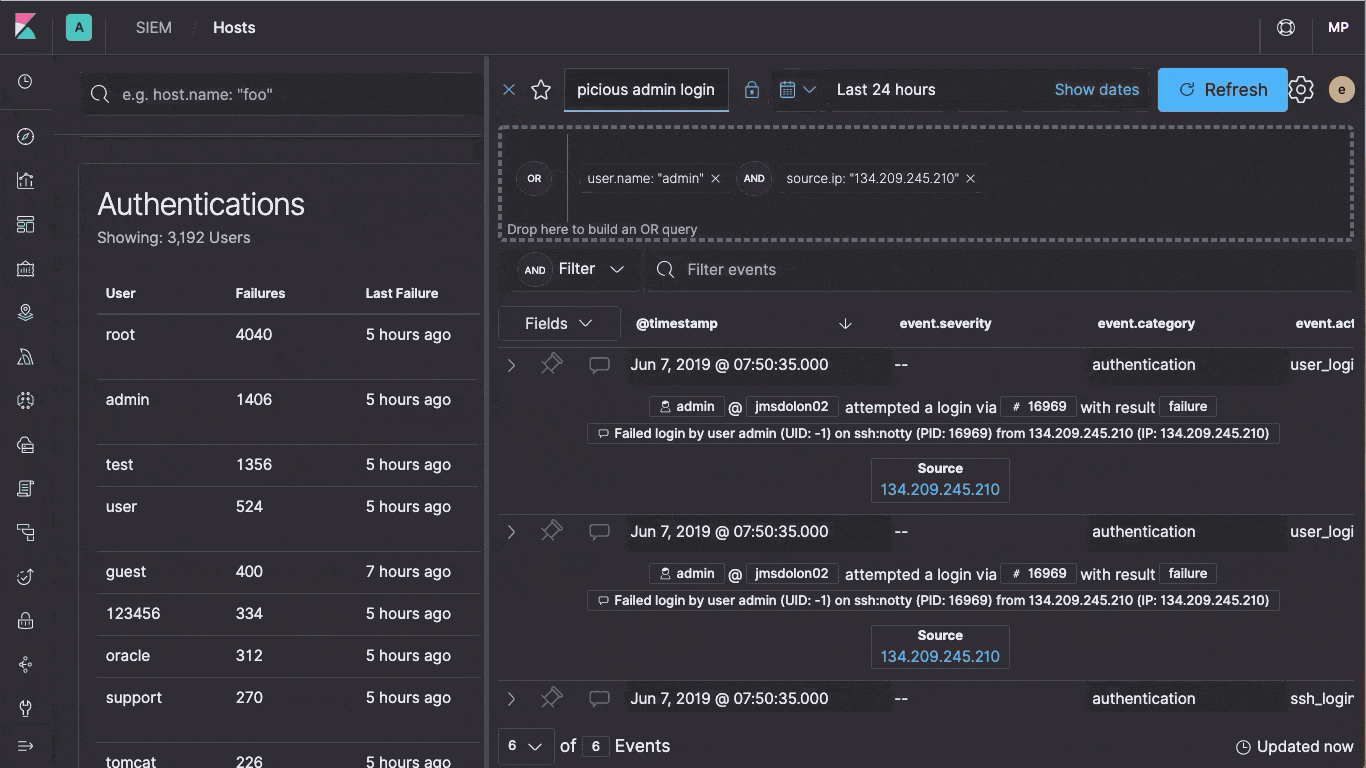
At the heart of Elastic SIEM is the new SIEM app, an interactive workspace for security teams to triage events and perform initial investigations. Its Timeline Event Viewer allows analysts to gather and store evidence of an attack, pin and annotate relevant events, and comment on and share their findings, all from within Kibana — allowing you to easily work with any data that follows the ECS format.
Kibana has always been a wonderful place for security teams to visualize, search, and filter their security data. The Elastic SIEM app takes all the aspects that security teams love about Kibana — interactivity, ad hoc search, and responsive drill downs — and packages it into an intuitive product experience that aligns with typical SOC workflows.
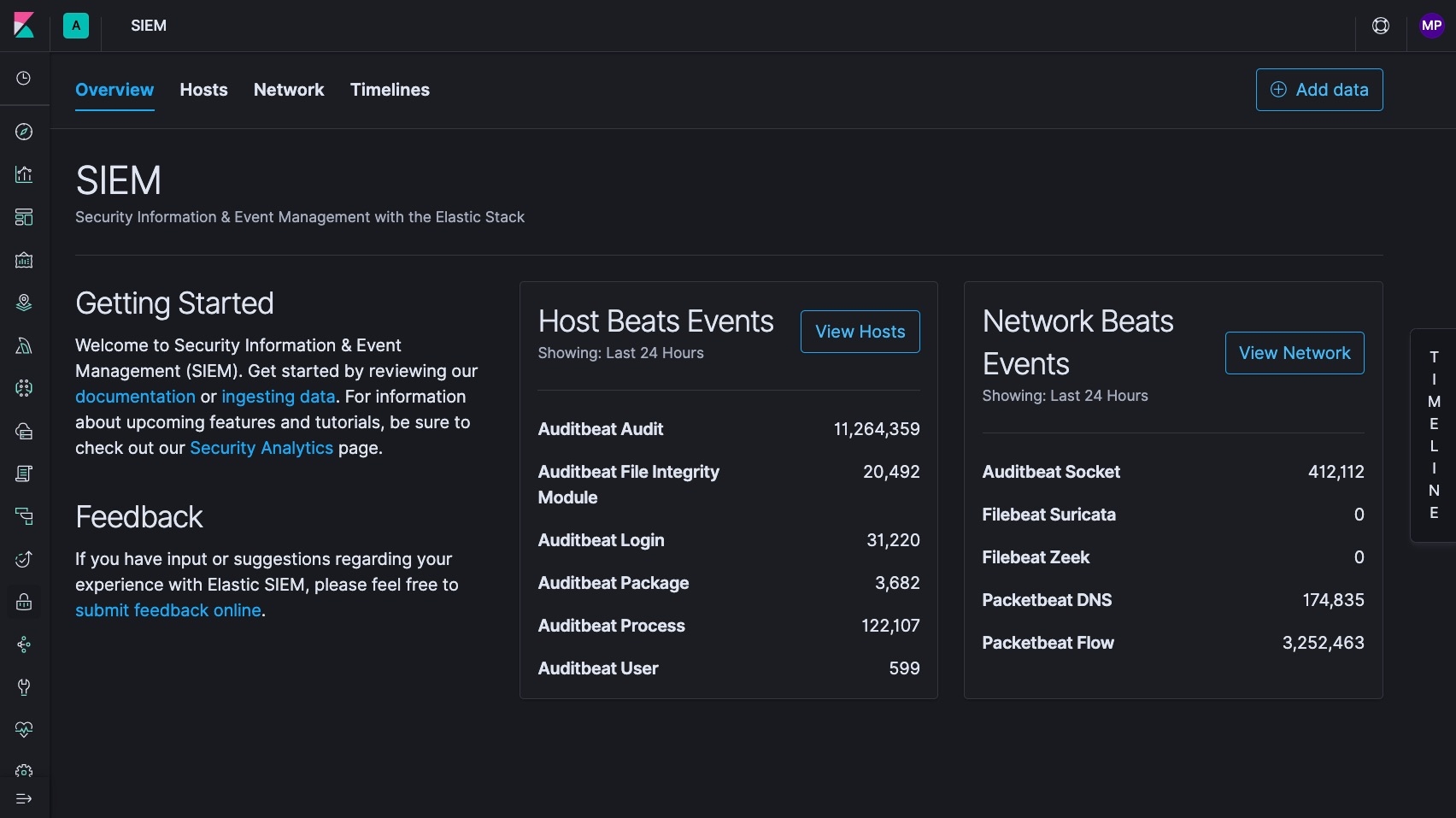
The SIEM app enables analysis of host-related and network-related security events as part of alert investigations or interactive threat hunting, including the following:
Host security event analysis
As a complement to the extensive library of visualizations and dashboards that already exist in Kibana, the Hosts view in the SIEM app provides key metrics regarding host-related security events, and a set of data tables that enable interaction with the Timeline Event Viewer. 7.2 also brings new host-based data collection with support for Sysmon in Winlogbeat.
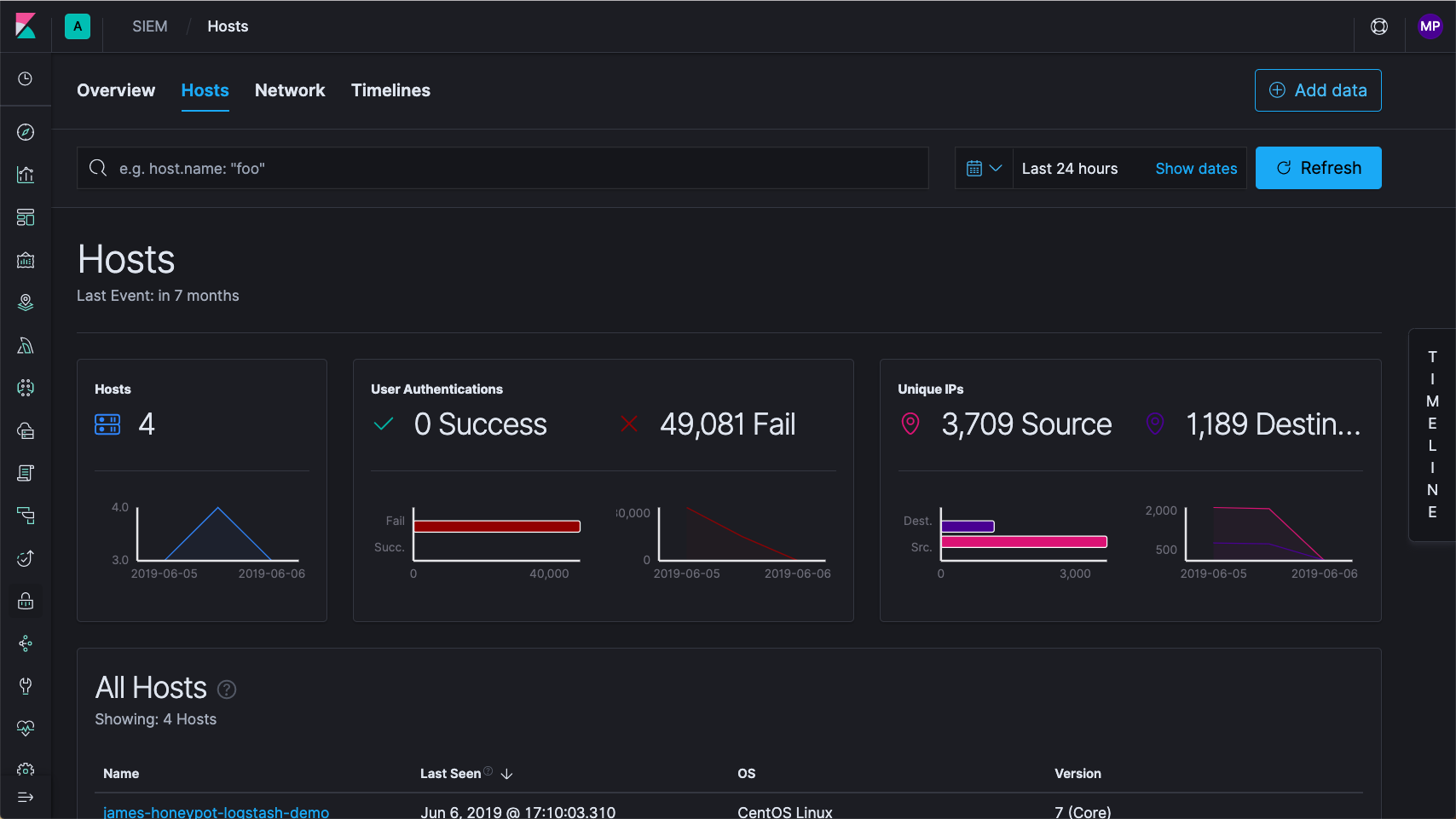
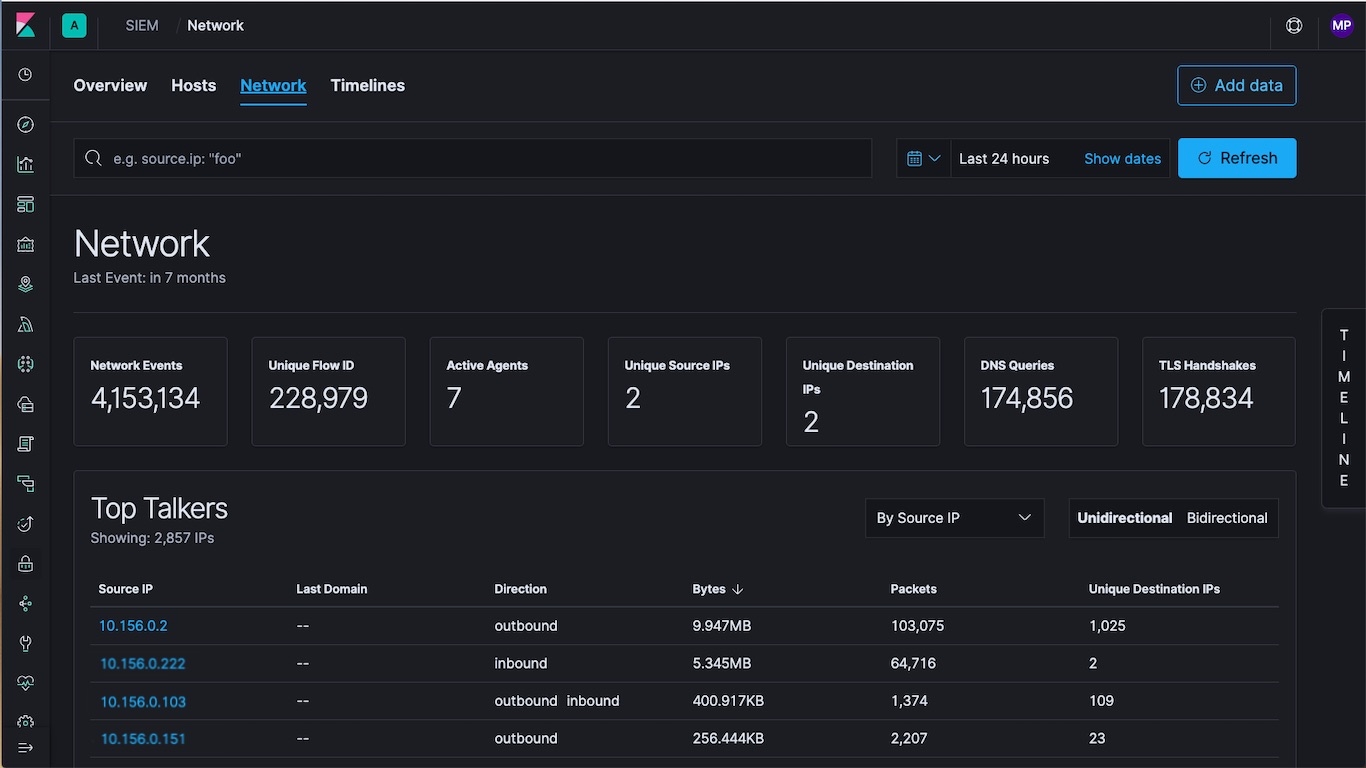
Network security event analysis
Similarly, the Network view informs analysts of key network activity metrics, facilitates investigation time enrichment, and provides network event tables that enable interaction with the Timeline Event Viewer. We’re also introducing support for Cisco ASA and Palo Alto firewalls in 7.2.
Timeline Event Viewer
As the collaborative workspace for investigations or threat hunting, analysts can easily drag objects of interest into the Timeline Event Viewer to create exactly the query filter they need to get to the bottom of an alert. During the investigation, analysts can pin and annotate individual events, and can add notes to describe the steps taken during the investigation. Auto-saving ensures that the results of the investigation are available for incident response teams.
The journey continues
At Elastic, we strive to move fast, release often, and provide a constant stream of value to our users. We believe Elastic SIEM is a great first step toward our vision of what a SIEM should be, and the early feedback from our user and partner community has been very positive.
Our partner ecosystem, including global systems integrators, has also witnessed users naturally deploying the Elastic Stack for SIEM use cases.
“Elastic’s new SIEM capability is enhancing our ability to streamline security visibility and build scalable, end-to-end security and data solutions for clients on the Elastic Stack,” said Greg Baker, vice president and general manager, cyber digital at Optiv, a security solutions integrator and Elastic recommended partner. “We are looking forward to jointly supporting the client demand for these capabilities and continuing our long-standing partnership with Elastic.”
This is a big milestone in our security journey, and we are excited to continue building this forward. Capabilities such as SIEM detection rules, user analysis, threat intelligence integration, and more data sources are all right up there on our roadmap. And it’s safe to say that we will continue to do things the Elastic way, and push and shift traditional boundaries and definitions of SIEM to help you protect your data, applications, and network infrastructure.
Get started today
To get started, spin up a cluster on Elasticsearch Service or install the latest version of the Elastic Stack. Already have ECS data in Elasticsearch? Just upgrade your clusters to 7.2 and give Elastic SIEM a try.
To simplify your getting started journey, we have some great material to get you started: