Integrating Azure single sign-on with ECE in 1-2-3 at STRABAG
At STRABAG, we are using Elastic Cloud Enterprise (ECE) for two main use cases within our on-premises web applications. One to power different kinds of search and a second for operations where we ship more than 25,000 log entries per minute to Elastic from our load balancers. The ECE platform runs in an air-gapped environment, and we would still like to be able to use our corporate logins for the ECE platform.
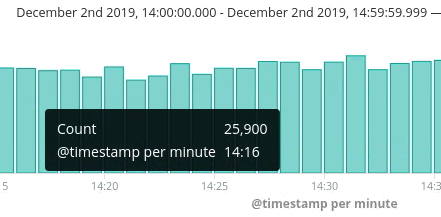
Therefore it was a very important task for us to implement a highly secure and identity management-aware authentication for the ECE platform based on Azure AD’s SAML protocol. Read on to see how we did it and how you can do it too in 1-2-3!
Authenticating ECE with Azure AD
Azure AD is commonly used as an identity provider for businesses who use Microsoft Office 365. It enables the customer to create a so called enterprise applications that can provide single sign-on (SSO) functionalities based on SAML or OAuth2.
Step 1: Creating an enterprise application
To get up and running, it is mandatory to create an enterprise application inside the Azure cloud at first. This can be done through the Azure portal. Just head over to the Azure Active Directory management and then use Enterprise applications to create a new application which will be used as an authentication entity for ECE later.

With a click on New application, a new enterprise application will be created.
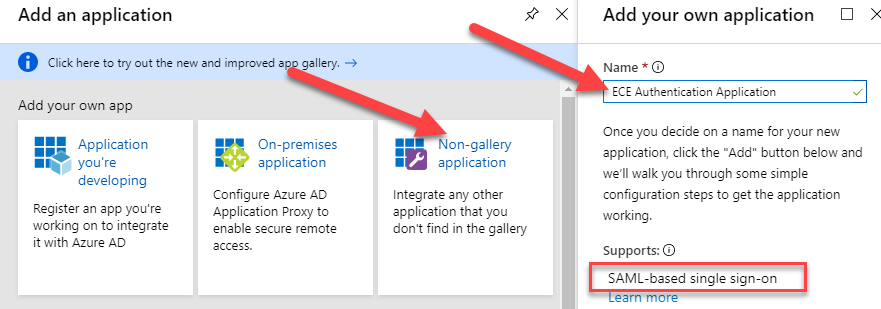
As we will just use the authentication features of Azure AD enterprise applications, we will create a Non-gallery application. Type in a name for the new application, eg ECE Authentication Application, and press the Add button afterwards. As shown in the screenshot, the application will provide the SAML-based single sign-on feature. This is what we want to achieve.
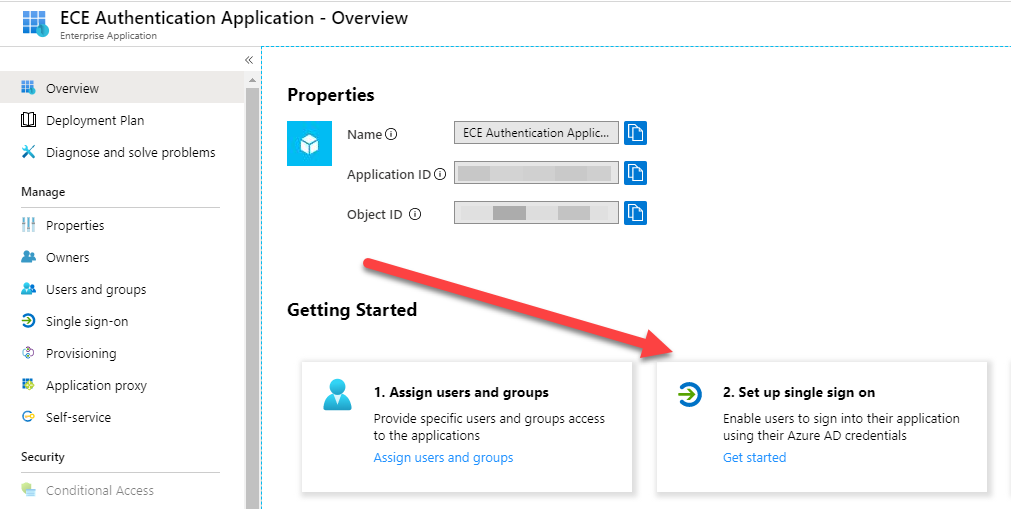
After some seconds, the configuration screen of your application will appear and you can continue to configure the SAML based authentication. Just click Set up single sign on.
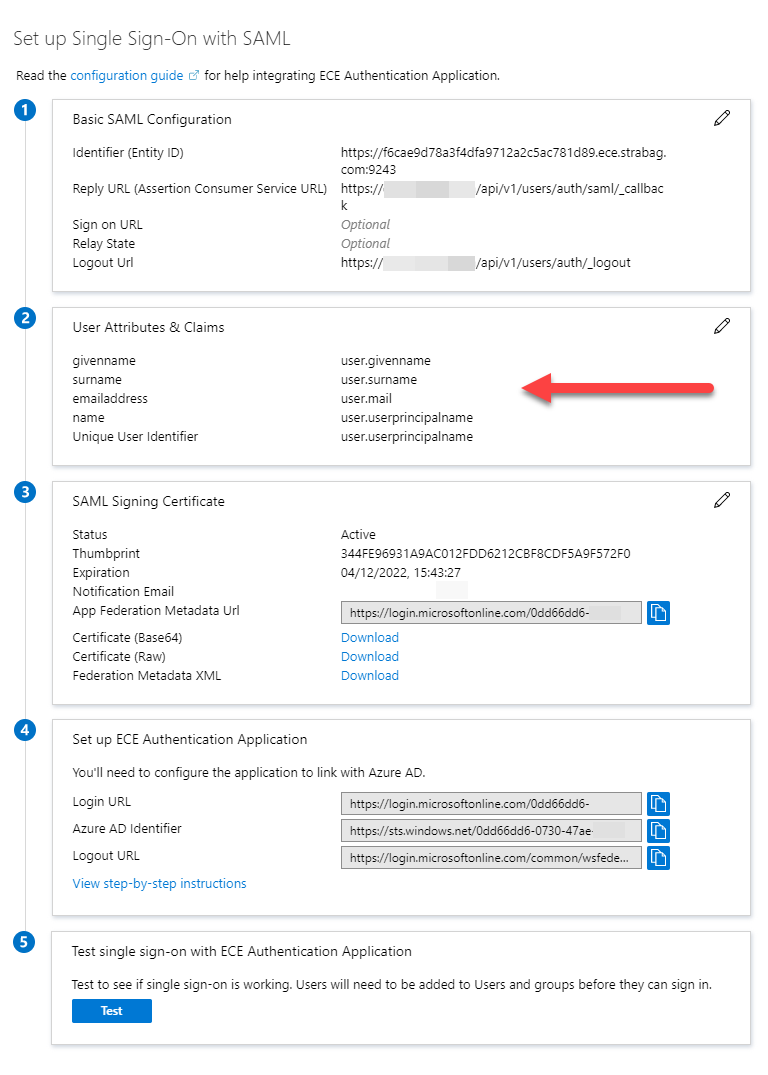
You have to configure the SAML authentication properties accordingly to the given defaults and your needs as follows:
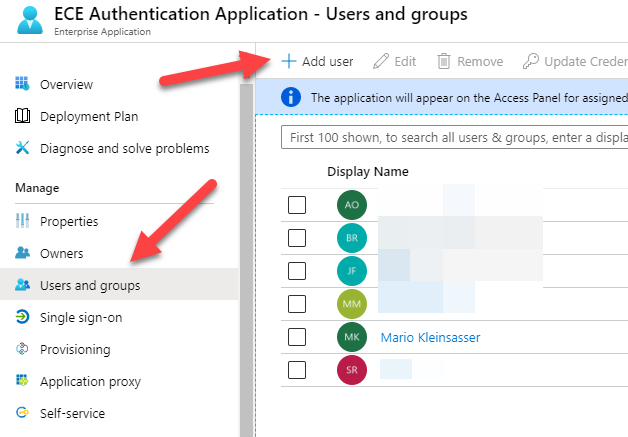
After the enterprise application is created, some users need to be assigned. In this configuration, it is assumed that every assigned user is permitted to have administrator access to the ECE platform. The user management can be done with the Users and groups configuration option of the enterprise application. Users can be added with the Add users button.
Step 2: Adding a SAML provider
Next, head over to the ECE platform administration page and navigate to Authentication providers and click the Add provider button.
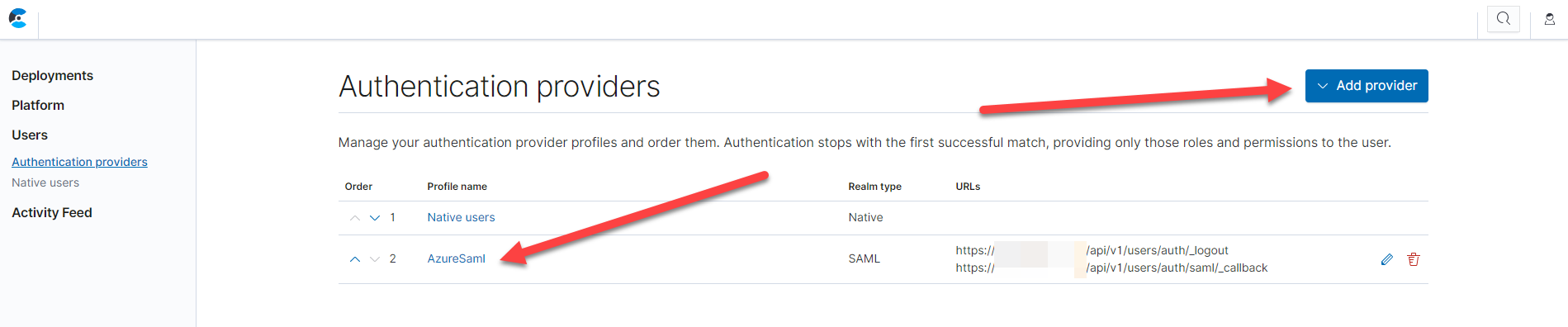
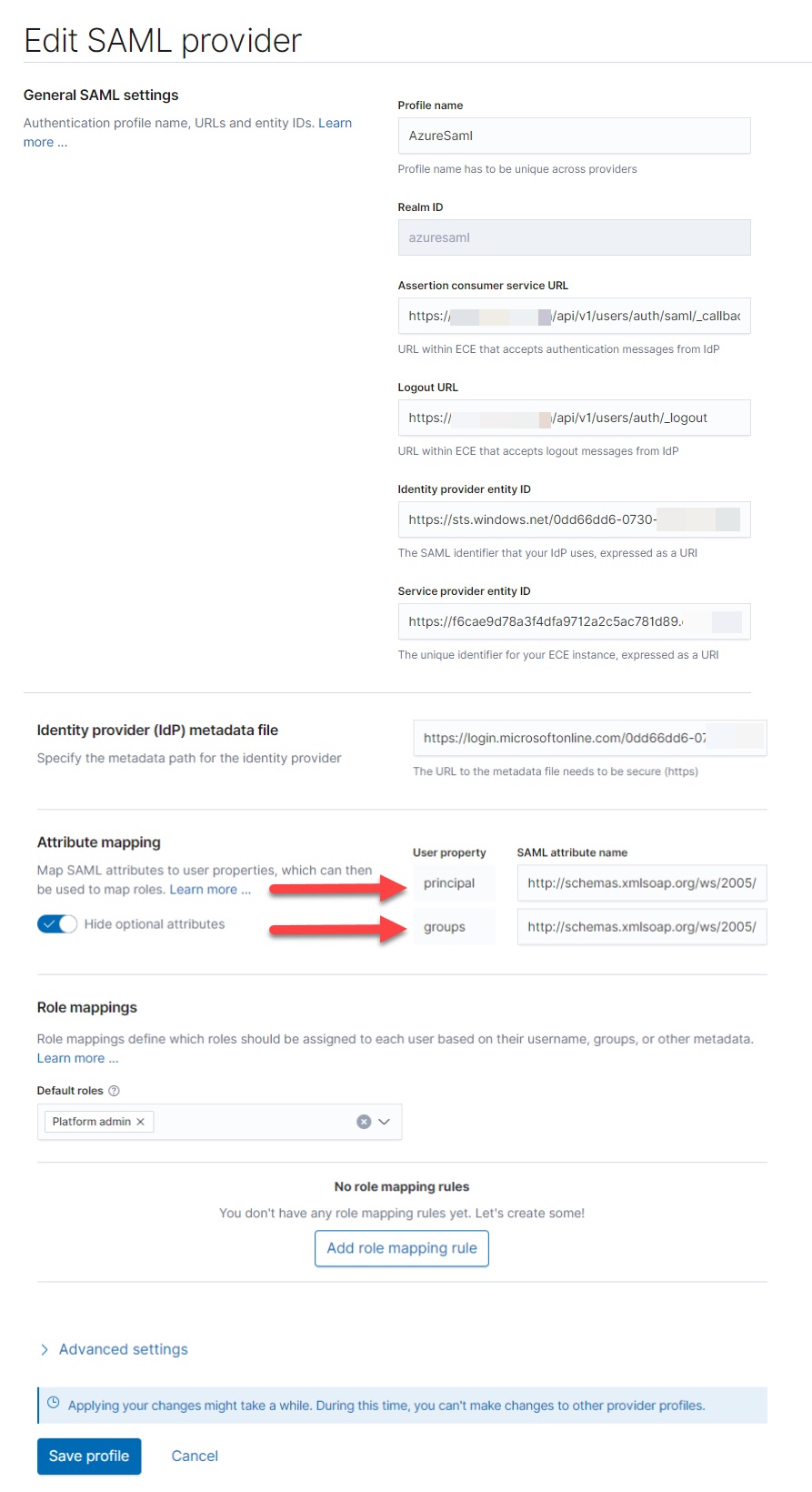
Configure the SAML provider to match the settings from the Azure AD enterprise application. It is very important here, that you specify the correct XML schema for the Attribute mapping of the principal and the groups.
The schemas you have to use are:
- Principal attribute: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
- Group attribute: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
Note: The above schema information is currently undocumented.
The SAML attributes are provided by the Azure AD User and Attributes & Claims configuration section (in the screenshot above).
Step 3: Testing the configuration
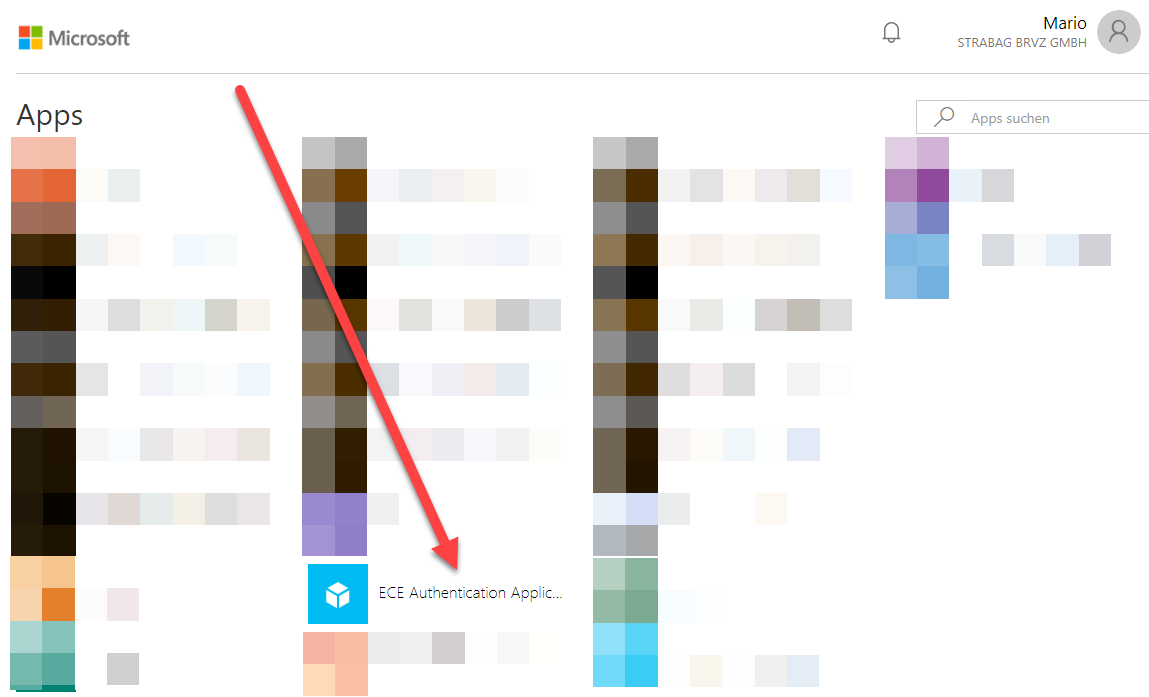
After you have configured everything you can head over to test the configuration. Microsoft provides an application portal which you can reach via https://myapps.microsoft.com.
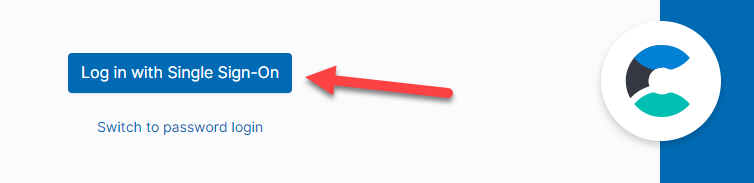
The application will be there as ECE Authentication Application. If you click on it, you will be redirected to the on-premises ECE platform and you will be logged in as the Azure AD authenticated user.
Conclusion
This configuration allows us to use corporate identities which are managed by Azure AD to log in via single sign-on in a secure and reliable way. As a fallback, you can login into the ECE platform administration anytime by using your admin account and your secret key which was generated during the setup. We hope you find this post helpful.
About the Authors
Mario Kleinsasser — Cloud Solution Architect Team Leader, STRABAG
Manuel Moser — Software Development Department Team Leader, STRABAG
Ahil PonArul — Consulting Architect, Elastic
Bernhard Rausch — Cloud Solution Architect, STRABAG
Stefan Ringhofer — Cloud Solution Architect, STRABAG
Ugo Sangiorgi — Principal Consulting Architect, Elastic