Detecting the undetectable: Building a fraud detection framework with Elastic
Learn how public sector organizations are using Elastic to identify fraudulent activity with rules and anomaly detection jobs fine-tuned for their specific use cases.
_(1).png)
Every organization faces the challenge of identifying and combating fraud. In the financial services industry, it might be credit card fraud; in the auto insurance space, staged accident fraud; and in the public sector, unemployment, health insurance, or tax fraud. Each domain presents unique challenges, requiring custom detection rules for known tactics and machine learning (ML) jobs to uncover the unknowns — this is where Elastic can be incredibly valuable.
These fraud challenges aren’t just theoretical. During the pandemic, the US Department of Labor estimated that “fraud accounted for 11–15% of the total amount of unemployment insurance benefits”1 which highlights how critical it is for organizations to proactively identify fraud patterns before they escalate.
Below, we’ll discuss how the Elasticsearch Platform can be used as a fraud detection tool using only Elastic-native features. Together, these capabilities provide a holistic approach to fraud detection. You can identify the known-knowns with threshold rules built using the detection rules feature, uncover the known-unknowns with anomaly detection jobs powered by ML, and reveal the unknown-unknowns by using an agentic system to correlate hundreds of alerts and surface coordinated activity through the Attack Discovery capability.
Elastic’s fraud detection capabilities can be especially valuable for smaller state, local, and education agencies that may already be using Elastic for use cases, such as search, SIEM, generative AI (GenAI), or logging. As a result, these agencies can consolidate tools, reduce tech debt, and increase ROI.
Detection rules: Identifying the known-knowns
Detection rules help identify the known-knowns — patterns and tactics you already understand and can codify into thresholds or conditions. One of the most common and basic fraud tactics involves a user submitting multiple claims with different email addresses from a single machine like an IP address.
With GenAI as accessible as it is today, it’s easy for a fraudster to purchase stolen identities on the dark web and use a script written by a GenAI chatbot to update accounts, redirect funds to a specific bank account, and submit fraudulent claims. To monitor for this known tactic, we can create a custom threshold rule to flag instances where three or more claims are submitted within a 24-hour period using different email addresses.
See detection rules in action:

Machine learning: Expanding detection to discover the known-unknowns
Machine learning expands detection to the known-unknowns — activities that don’t match fixed patterns but stand out as statistically unusual for your environment. Detection rules are an excellent first step in capturing tactics that you already know exist, but they can also generate noise. For example, checking for claims from three or more distinct email addresses from a single IP seems like the right approach, but what about three adults that are all filing for unemployment from the same computer in the same household? Should that trigger an alert that needs to be investigated by a fraud analyst? Probably not.
A better approach might be to use an ML job to monitor for an actual anomalous event — activities that deviate from their historical baseline. Elastic offers both unsupervised and supervised machine learning. But in this scenario, an anomaly detection job is the right choice. The GIF below demonstrates how to set up a multi-metric job that constructs a probability model capable of running continuously to identify unusual events as they occur with the model evolving over time.
In our example of three adults filing for unemployment from the same household, this approach is a better indicator of fraud because it won’t capture this activity; it's not anomalous relative to the IP address’ claim history. Instead, it will detect IPs with an unusually high number of claims using distinct email addresses.
Watch the machine learning demo:

Attack Discovery: Revealing the unknown-unknowns
Finally, Attack Discovery helps uncover the unknown-unknowns — complex, coordinated behaviors that no rule or model could have anticipated but can be surfaced by correlating signals through a large language model (LLM). Attack Discovery, a feature many of our Elastic Security customers are already familiar with, was designed to lighten the workload of SOC analysts.
SOCs have to sift through thousands of alerts every day. By using an LLM to evaluate alerts — factoring in metadata like severity, risk scores, and asset criticality — Elastic can surface attacks that encompass multiple alerts. Doing so eliminates the need for SOC analysts to spend hours manually reviewing all the alerts individually to try to piece together what happened. There’s no reason that this same approach can’t also be used to triage alerts triggered by detection rules and anomaly detection jobs built specifically to identify fraud.
With a single click of the “Generate” button in the top right corner, Elastic can identify coordinated fraud operations, such as two IP addresses associated with suspicious claims. The details provided in the output would have taken hours for a fraud analyst to triage and organize. But with Attack Discovery, the analyst can immediately focus on preventing further fraud by isolating these accounts and contacting the legitimate account owners.
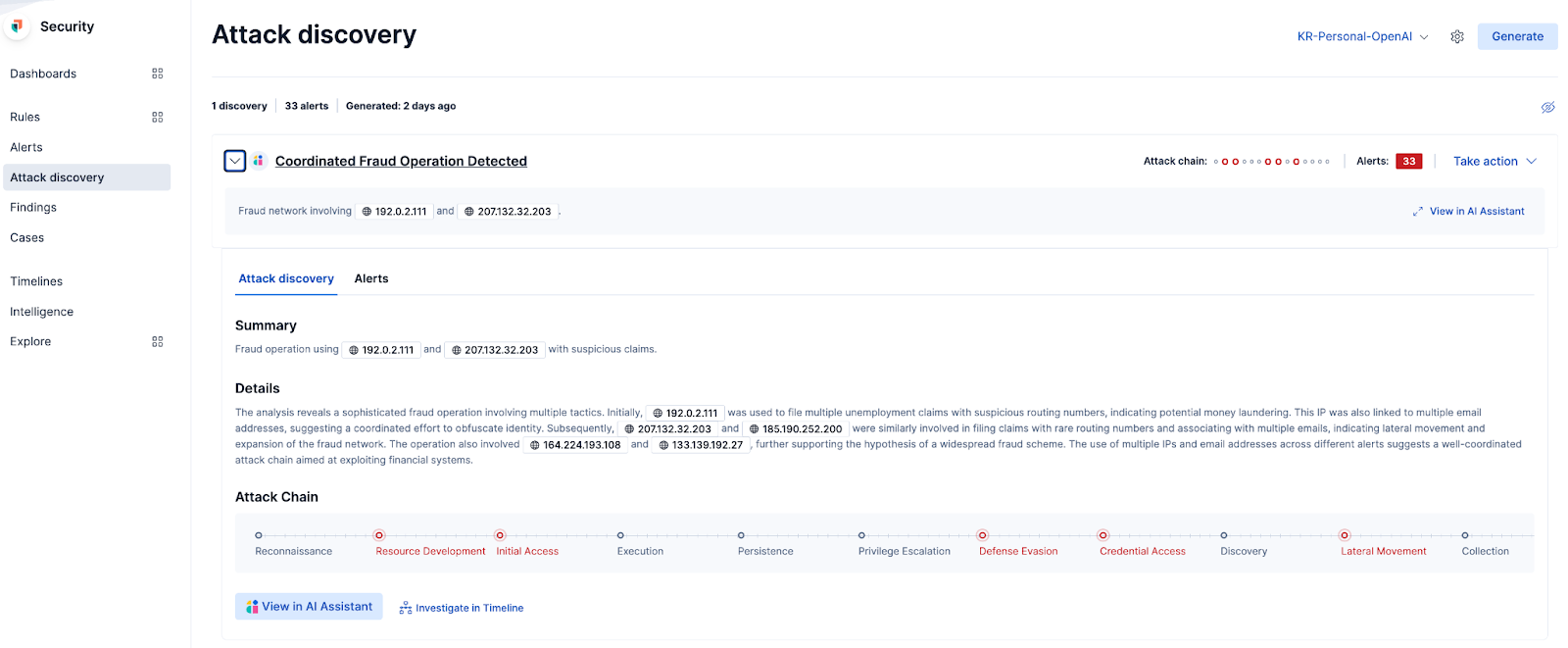
A holistic approach to modern fraud detection
In this blog, we demonstrated how teams can use Elastic-native features to build a fraud detection solution tailored to their specific needs. Detection rules help capture recurring fraud patterns; anomaly detection jobs uncover unusual activity relative to an entity’s baseline; and Attack Discovery uses LLMs to surface coordinated activity that would otherwise take hours to piece together manually.
Fraud has always been a persistent threat. And with the rise of GenAI, it’s becoming even more sophisticated. That’s why public sector organizations are using Elastic’s flexible data platform to design solutions that address their unique environments and risks.
If you’re using Elastic Enterprise, you already have access to all of these features. It’s just a matter of using them. Elasticsearch is more than just a SIEM, EDR/XDR, APM, or search application tool. It’s an extensive data and analytics platform that can solve a multitude of data challenges.
Ready to put Elastic’s native fraud detection capabilities to work?
Discover how Elastic can help your organization detect, prevent, and respond to fraud with a flexible, scalable data platform. Get in touch with our Public Sector team today.
Source:
1U.S. Government Accountability Office, “Unemployment Insurance: Estimated Amount of Fraud During Pandemic Likely Between $100 Billion and $135 Billion,” 2023.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos or registered trademarks of Elasticsearch B.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.