Overview dashboard
Serverless Security Stack
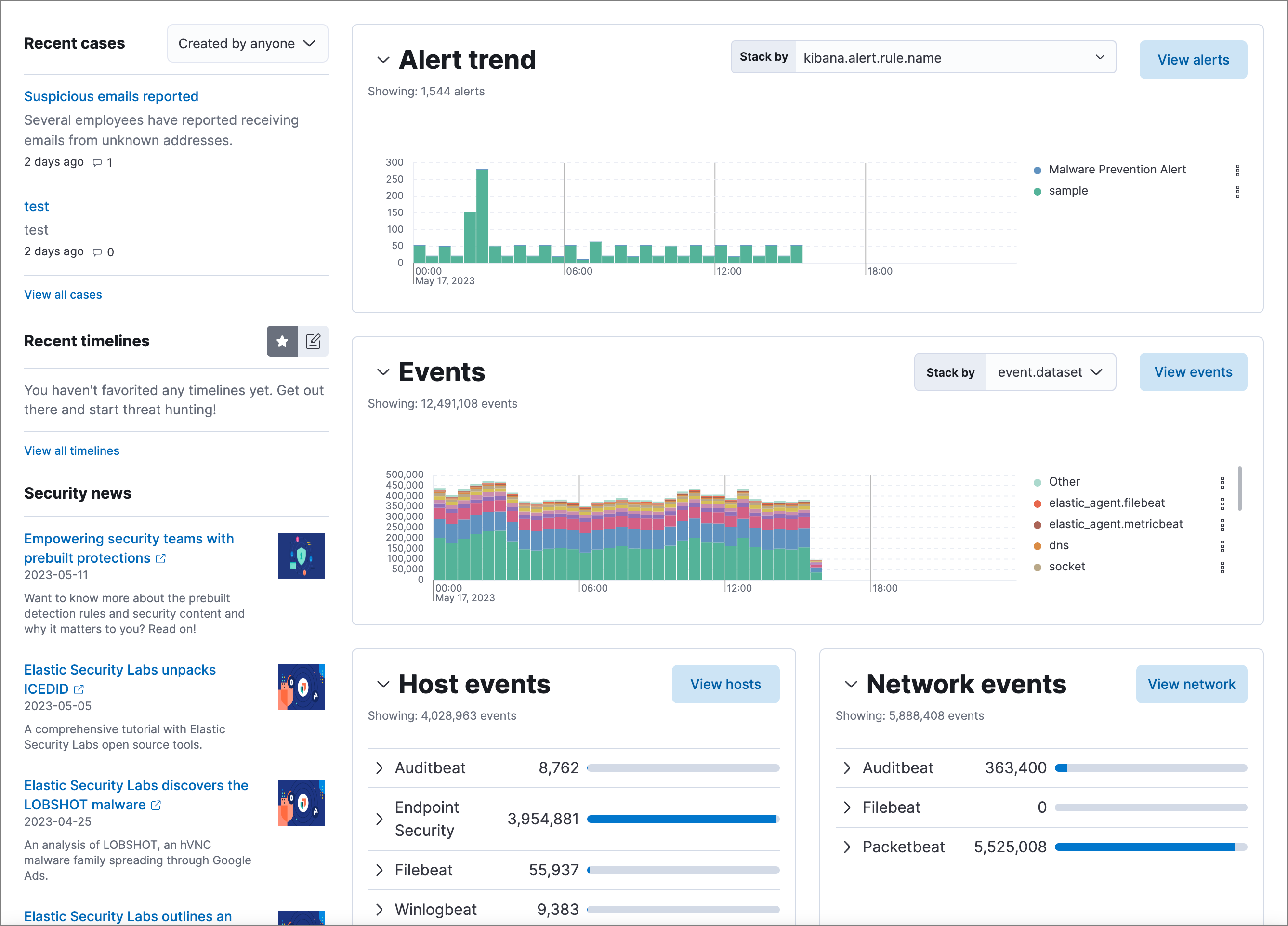
The Overview dashboard provides a high-level snapshot of alerts and events. It helps you assess overall system health and find anomalies that may require further investigation.
The live feed on the Overview dashboard helps you quickly access recently created cases, favorited Timelines, and the latest Elastic Security news.
The Security news section provides the latest Elastic Security news to help you stay informed of new developments, learn about Elastic Security features, and more.
Time-based histograms show the number of detections, alerts, and events that have occurred within the selected time range. To focus on a particular time, click and drag to select a time range, or choose a preset value. The Stack by menu lets you select which field is used to organize the data. For example, in the Alert trend histogram, stack by kibana.alert.rule.name to display alert counts by rule name within the specified time frame.
Hover over histograms, graphs, and tables to display an Inspect button (![]() ) or options menu (
) or options menu (![]() ). Click to inspect the visualization’s Elasticsearch queries, add it to a new or existing case, or open it in Lens for customization.
). Click to inspect the visualization’s Elasticsearch queries, add it to a new or existing case, or open it in Lens for customization.
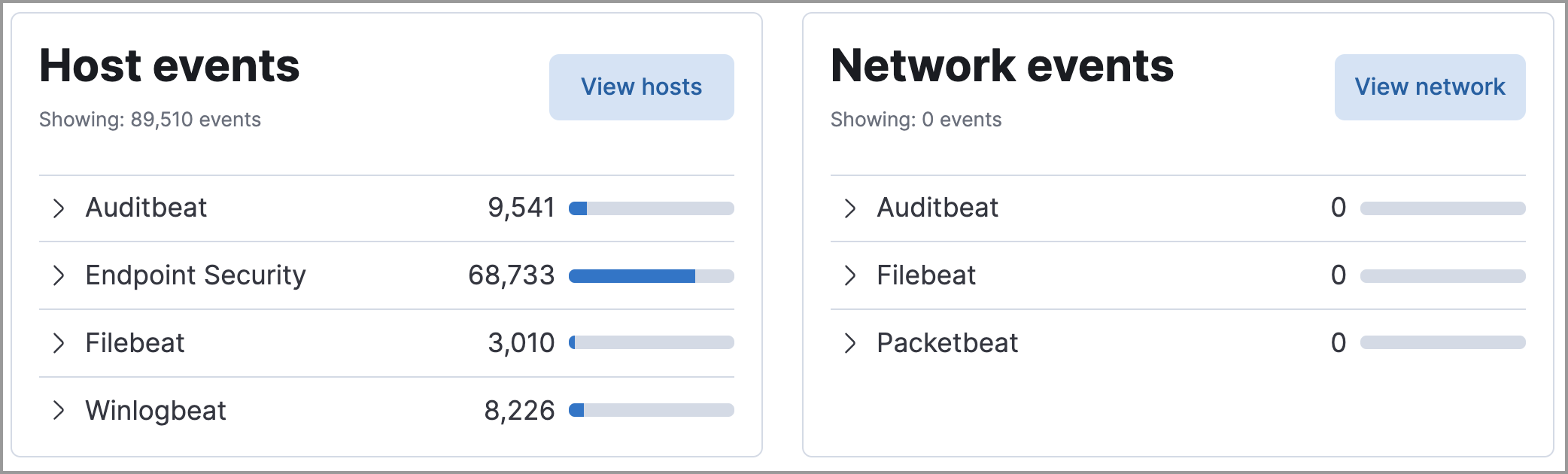
View event and host counts grouped by data source, such as Auditbeat or Elastic Defend. Expand a category to view specific counts of host or network events from the selected source.
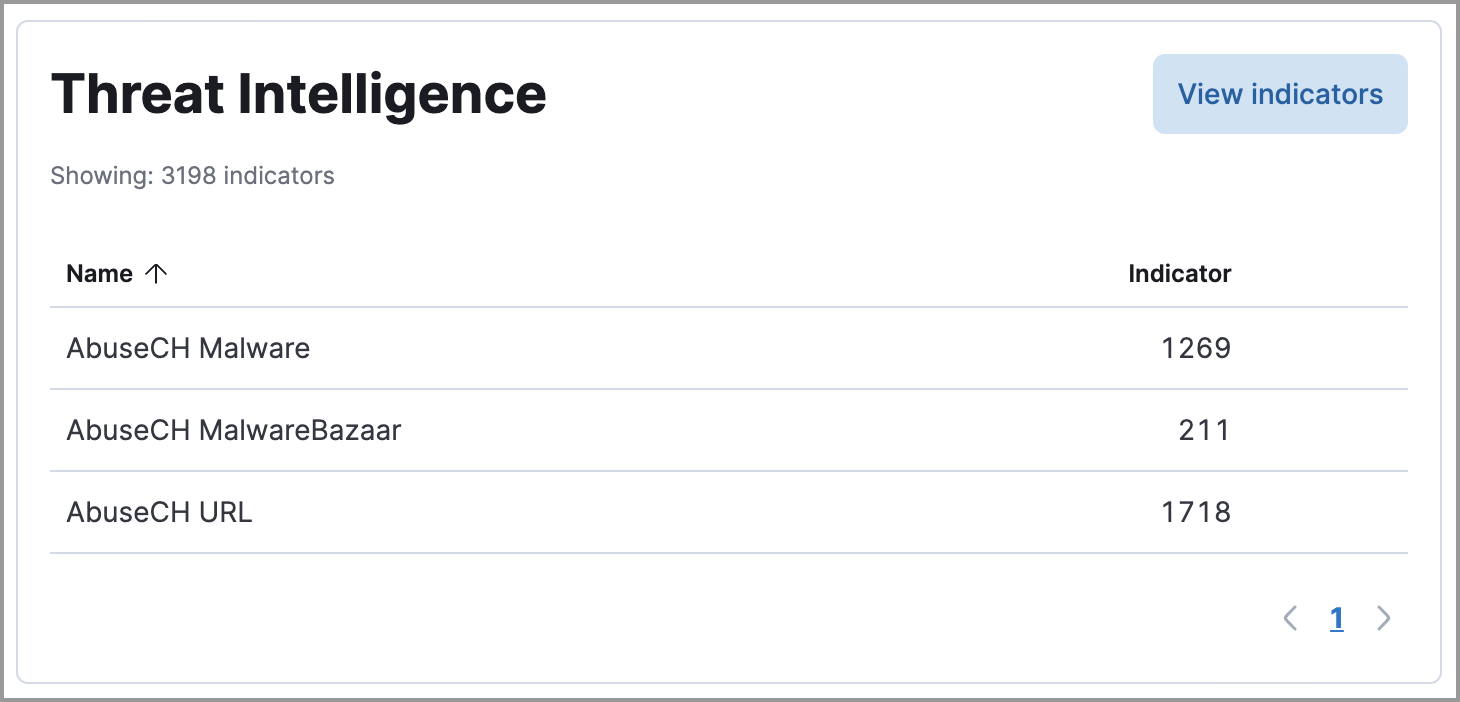
The Threat Intelligence view on the Overview dashboard provides streamlined threat intelligence data for threat detection and matching.
The view shows the total number of ingested threat indicators, enabled threat intelligence sources, and ingested threat indicators per source. To learn more about the ingested indicator data, click View indicators.
For more information about connecting to threat intelligence sources, visit Enable threat intelligence integrations.