Elastic Defend feature privileges
editElastic Defend feature privileges
editYou can create user roles and define privileges to manage feature access in Kibana. This allows you to use the principle of least privilege while managing access to Elastic Defend’s features.
Roles and privileges are configured in Stack Management → Roles in Kibana. For more details on using this UI, refer to Kibana privileges.
Elastic Defend’s feature privileges must be assigned to All Spaces. You can’t assign them to an individual Kibana space.
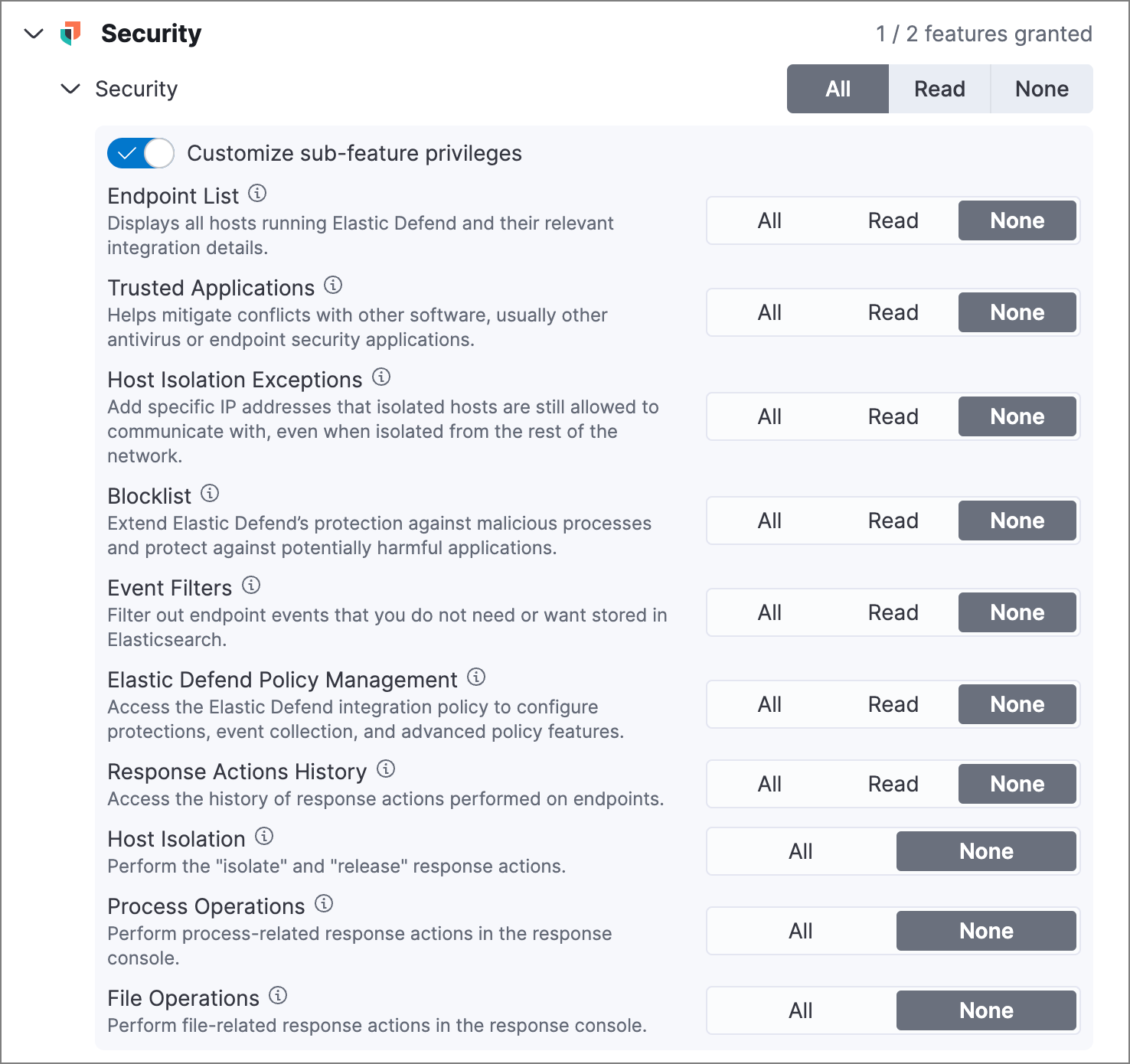
To grant access, select All for the Security feature in the Kibana privileges configuration UI, then turn on the Customize sub-feature privileges switch. For each of the following sub-feature privileges, select the type of access you want to allow:
- All: Users have full access to the feature, which includes performing all available actions and managing configuration.
- Read: Users can view the feature, but can’t perform any actions or manage configuration. (Some features don’t have this privilege.)
- None: Users can’t access or view the feature.
Endpoint List |
Access the Endpoints page, which lists all hosts running Elastic Defend, and associated integration details. |
Trusted Applications |
Access the Trusted Applications page to remediate conflicts with other software, such as antivirus or endpoint security applications. |
Host Isolation Exceptions |
Access the Host Isolation Exceptions page to add specific IP addresses that isolated hosts can still communicate with. |
Blocklist |
Access the Blocklist page to prevent specified applications from running on hosts, extending the list of processes that Elastic Defend considers malicious. |
Event Filters |
Access the Event Filters page to filter out endpoint events that you don’t want stored in Elasticsearch. |
Elastic Defend Policy Management |
Access the Policies page and Elastic Defend integration policies to configure protections, event collection, and advanced policy features. |
Response Actions History |
Access the response actions history for endpoints. |
Host Isolation |
Allow users to isolate and release hosts. |
Process Operations |
Perform host process-related response actions, including |
File Operations |
Perform file-related response actions in the response console. |
Upgrade considerations
editAfter upgrading from Elastic Security 8.6 or earlier, existing user roles will be assigned None by default for any new endpoint management feature privileges, and you’ll need to explicitly assign them. However, many features previously required the built-in superuser role, and users who previously had this role will still have it after upgrading.
You’ll probably want to replace the broadly permissive superuser role with more focused feature-based privileges to ensure that users have access to only the specific features that they need. Refer to Kibana role management for more details on assigning roles and privileges.