Elastic Defend feature privileges
editElastic Defend feature privileges
editYou can create user roles and define privileges to manage feature access in Kibana. This allows you to use the principle of least privilege while managing access to Elastic Defend’s features.
Roles and privileges are configured in Stack Management → Roles in Kibana. For more details on using this UI, refer to Kibana privileges.
Elastic Defend’s feature privileges must be assigned to All Spaces. You can’t assign them to an individual Kibana space.
To grant access, set the privileges for the following sub-features under the Security feature in the Kibana privileges configuration UI:
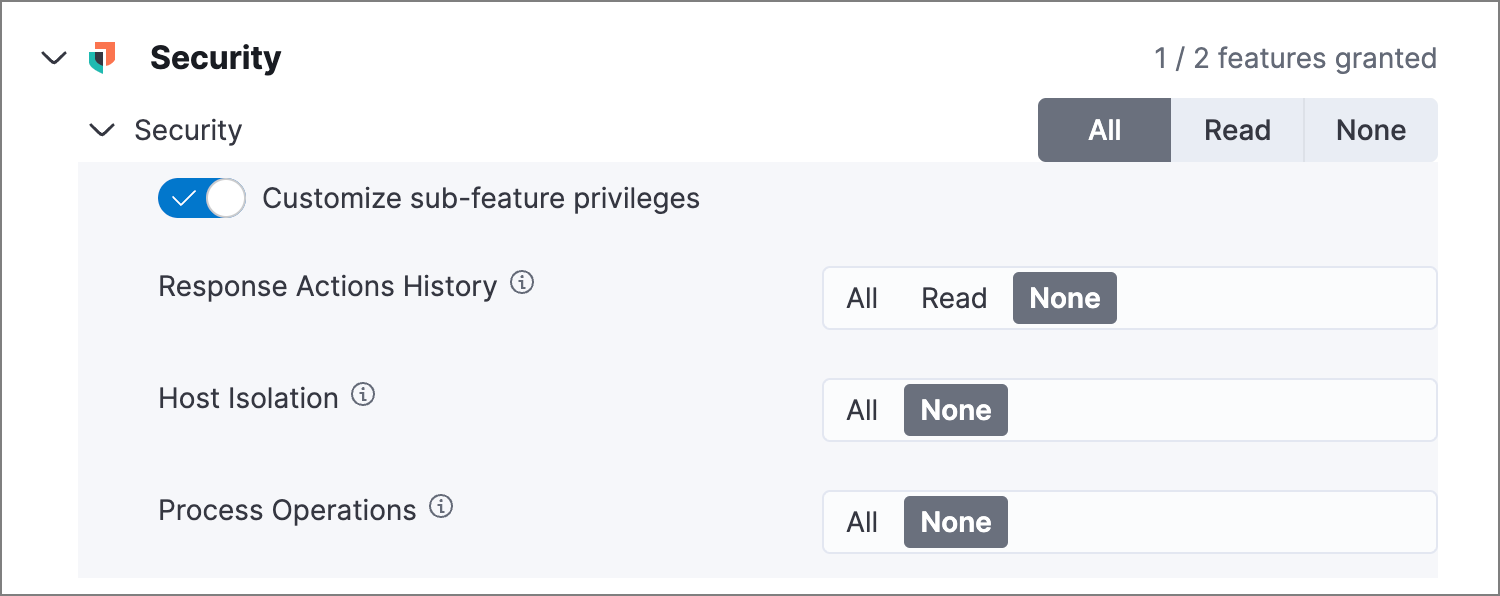
Response Actions History |
Allow users to access the response actions history for endpoints.
|
Host Isolation |
Allow users to isolate and release hosts. |
Process Operations |
Allow users to perform response actions related to host processes, including |