Findings
editFindings
editThe vulnerabilities findings page displays the vulnerabilities detected by the CNVM integration. CNVM findings include metadata such as the CVE identifier, CVSS score, severity, affected package, and fix version if available, as well as information about impacted systems.
To help you prioritize remediation efforts, you can filter and sort your findings based on these fields.
Clicking on a finding provides a detailed description of the vulnerability, and any available remediation information.
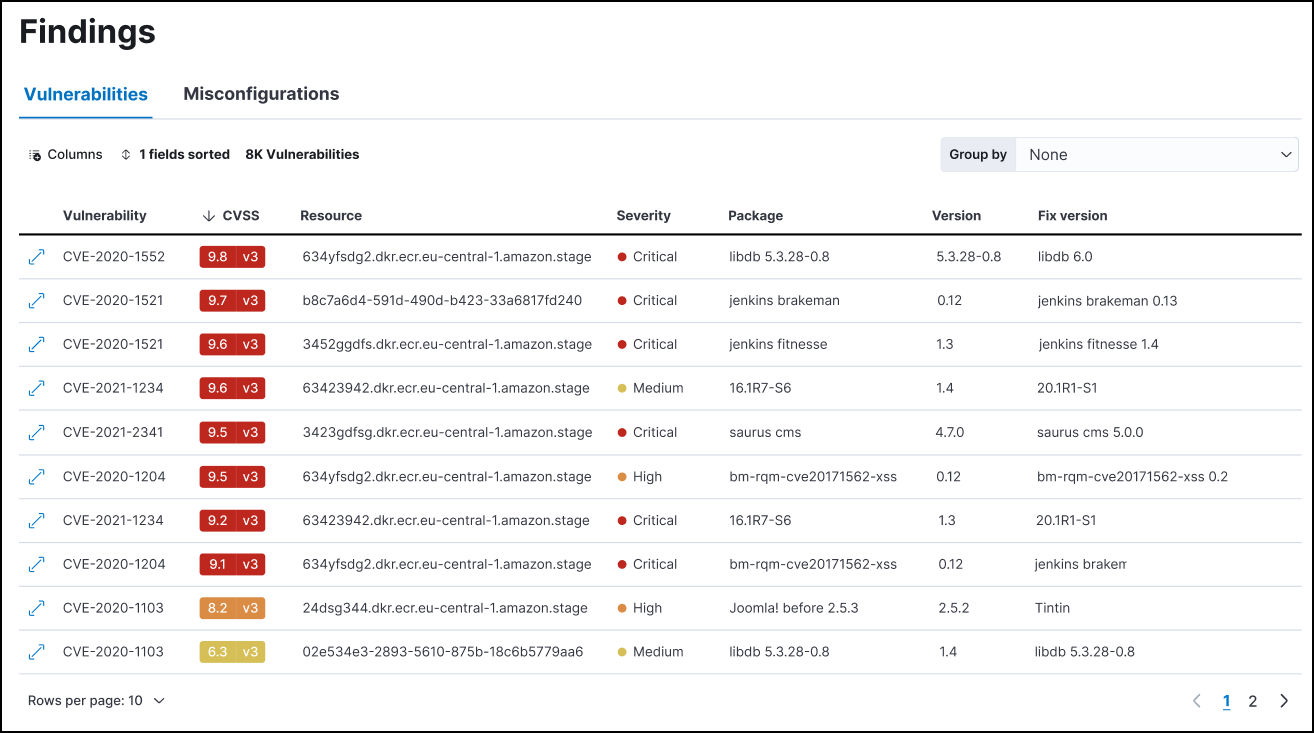
Group, sort, and filter findings
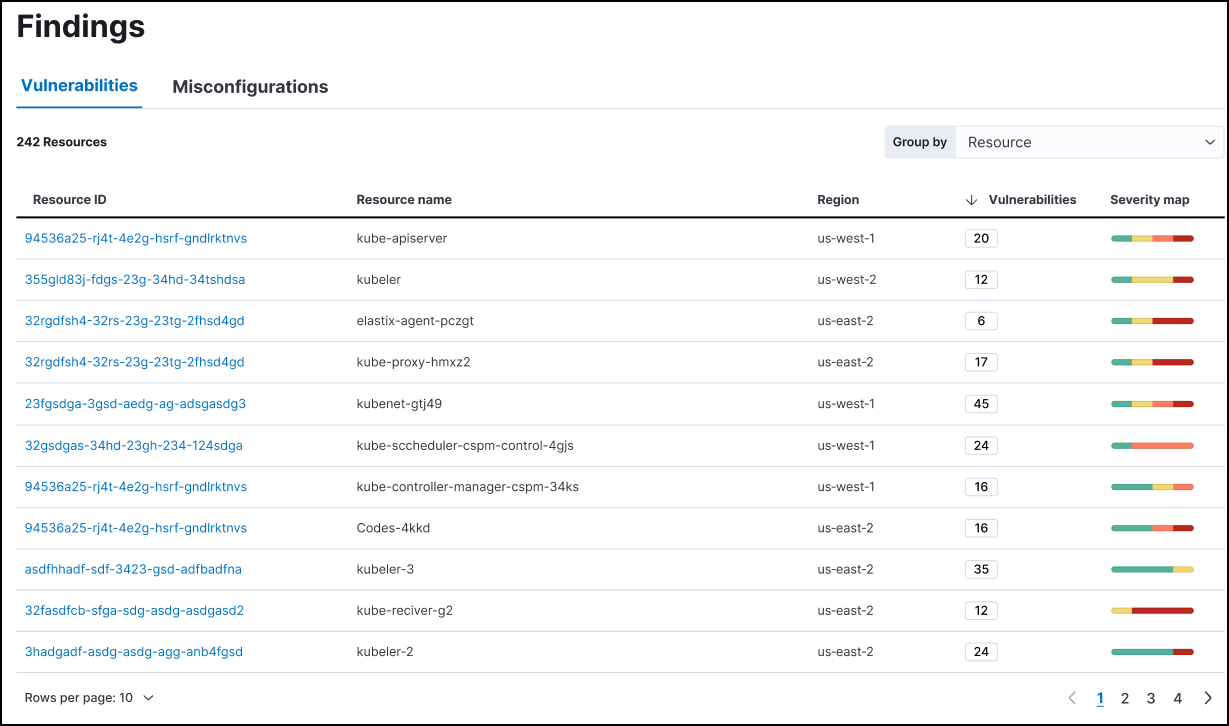
editYou can group your data by resource by selecting Resource from the Group by menu. When data is grouped by resource, you can click on the name of a virtual machine to view all vulnerabilities that were found on it.
When Group by is set to None, you can sort the Findings table by clicking the column headings or the Sort fields button to the upper left of the table. When sorting is active, the Sort fields button changes to X fields sorted (where X is the number of fields sorting your data), and can be used to modify or clear sorting.
Independent of grouping, you can filter data in two ways:
-
The KQL search bar: Use this to filter your findings. For example, search for
vulnerability.id : CVE-2019-00001to view all findings related to a particular vulnerability. - In-table value filters: Hover over a vulnerability CVE ID to display available inline actions. Use the Filter In (+) and Filter Out (-) buttons.
Learn more about a vulnerability
editClick a vulnerability to open the vulnerability details flyout. This flyout includes a link to the related vulnerability database, the vulnerability’s publication date, CVSS vector strings, fix versions (if available), and more.
When you open the vulnerability details flyout, it defaults to the Overview tab, which highlights key information. To view every field present in the vulnerability document, select the Table or JSON tabs.
Customize the Findings table
editUse the toolbar buttons in the upper-left of the Findings table to customize the columns you want displayed:
- Columns: Select which columns to display.
- x fields sorted: Sort the table by one or more columns.
Remediate vulnerabilities
editTo remediate a vulnerability and reduce your attack surface, update the affected package if a fix is available.
Generate alerts for failed Findings
editYou can create detection rules that detect specific vulnerabilities directly from the Findings page:
- Click a vulnerability to open the vulnerability details flyout flyout.
- Click Take action, then Create a detection rule. This automatically creates a detection rule that creates alerts when the associated vulnerability is found.
- To review or customize the new rule, click View rule.