7.10
edit7.10
edit7.10.1
editBug fixes and enhancements
edit7.10.0
editPost upgrade requirements
editWhen upgrading the Elastic Stack to version 7.10.0 from a previous minor version (7.9.x), perform the following:
-
Grant
view_index_metadatapermissions to any Elastic Security users. This is required to enable event correlation rules. Other previously activated detection rules will continue to run after upgrade.
Breaking changes
editSignals template updated for rollover indices
The create_index_route now checks if the template needs to be upgraded
before creating the index. If the index already exists and the template was upgraded,
the index rolls over so that the write index has the upgraded mapping.
This breaks the old mappings that have risk_score mapped as a keyword.
In the new mapping, signal.rule.risk_score is a float. After rolling over,
there is a conflict between the old and new signal.rule.risk_score for some
features, such as aggregations.
This requires the view_index_metadata permission in Kibana. See (#80019) for details.
Connect incident fields allowed when cases are sent
You can now specify connector incident fields when cases are sent. This includes: * Jira: issue type, priority, and parent issue in the case of a subtask. * IBM Resilient: issue types, and severity. * ServiceNow: urgency, severity, and impact.
See (#77327) for details.
Bug fixes and enhancements
edit- Adds Metadata and Discovery Analysis Jobs to Security Integration (#76023).
- Improves Alert Telemetry for the Security app (#77200).
- Allows passwords to be visible on security screens (#77394).
- Groups features for role management (#78152).
- Warns users when security is not configured (#78545).
- Enhancements for saved object management workflows (#75444).
- Adds EQL search strategy for security (#78645).
- Fetches related events from specified devices (#78780).
- Excludes cloud alias index from EQL query (#81551).
- Telemetry: Displays collected security event sample (#78963).
- Analyze Events: Requests data from new event API (#78782).
- Detections: Handle conflicts on alert status update (#75492).
Known issues
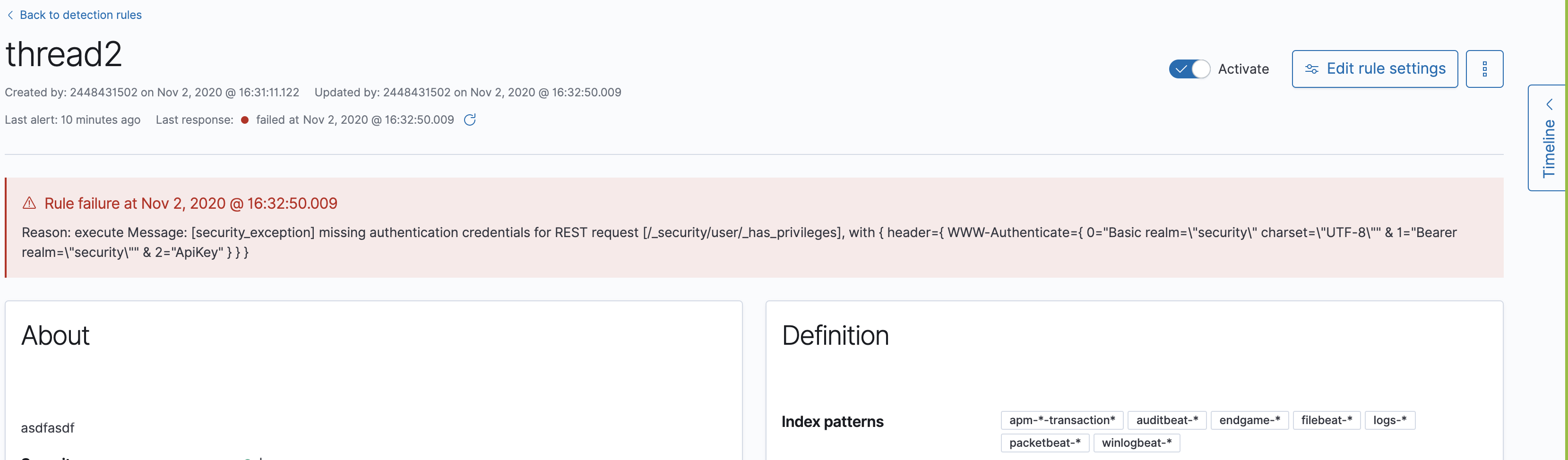
edit-
If you edit a rule while that rule is running, the rule fails. Subsequent successful runs will retain the previous failure message (#82320).
-
When adding a rule exception, you cannot select value lists of type
ip_range. Lists of typeip_rangewill not appear in the Add Exception dropdown as possible values after selecting the is in list operator. (#79511).