Cases prerequisites
editCases prerequisites
editYou can create roles and define feature privileges at different levels to manage feature access in Kibana. Kibana privileges grant access to features within a specified Kibana space, and you can grant full or partial access. For more information, see Feature access based on user privileges.
To send cases to external systems, you need the appropriate license.
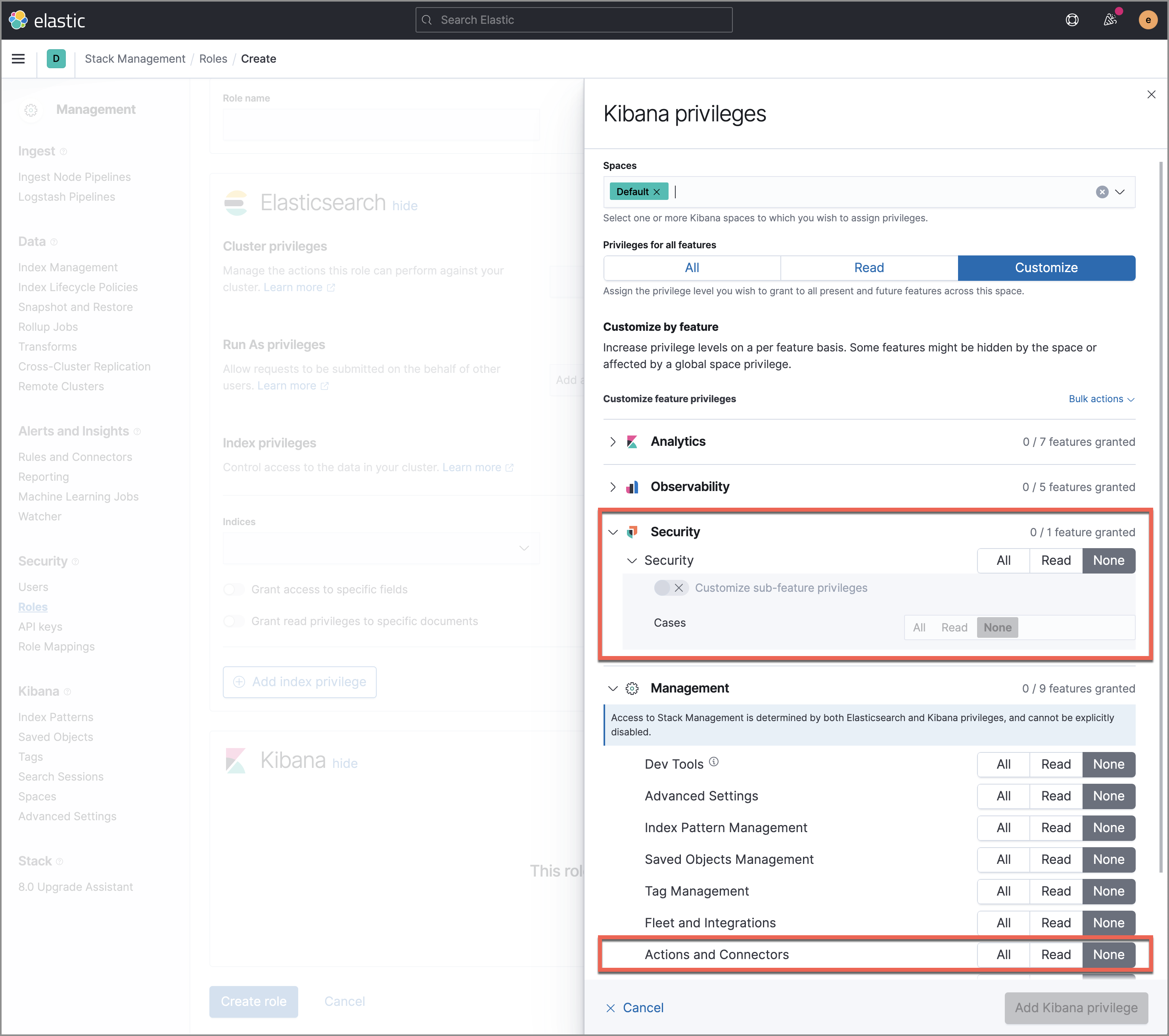
When setting up feature access to cases, you can configure the following:
- Base privileges for the Elastic Security solution
- Sub-feature privileges for the Cases feature (toggle Customize sub-feature privileges to use this optional setting)
- Privileges for actions and connectors
Privileges set at the sub-feature level will override base privileges for the Elastic Security solution. In other words, the Cases feature takes on the base privileges of the Elastic Security solution unless configured otherwise. For example, a role with Read base privileges only can view Elastic Security features and artifacts (including cases) within the Elastic Security app but can’t modify them. However, setting the role’s sub-feature privileges for Cases to All allows the role to view and manage cases only.
More information about the minimum privileges needed to use cases is below:
| Action | Kibana Privileges |
|---|---|
Give full access to manage cases |
Roles without |
Give view-only access for cases |
|
Revoke all access to cases |
|