Trusted applications
editTrusted applications
editAdministrators can add Windows, macOS, and Linux applications that should be trusted. By adding these trusted applications, you can use Elastic Security without compatibility or performance issues with other installed applications on your system. Trusted applications are applied only to hosts running Endpoint Security.
Trusted applications are designed to help mitigate performance issues and incompatibilities with other endpoint software. However, they create blindspots for Elastic Security. One avenue attackers use to exploit these blindspots is by DLL (Dynamic Link Library) side-loading, where they leverage processes signed by trusted vendors — such as antivirus software — to execute their malicious DLLs. Such activity appears to originate from the trusted vendor’s process.
To add a trusted application:
- Go to Manage → Trusted applications.
- Click Add Trusted Application.
-
Fill in the following fields in the Add trusted application pane:
-
Name your trusted application: Enter a name for the trusted application. -
Select operating system: Select the appropriate operating system from the drop-down. -
Field: Select the appropriate field you want to use —Hash,Path, or, if you are adding a Windows trusted application,Signature.You can only add a single field type value per trusted application. For example, if you try to add two
Pathvalues, you’ll get an error message. Hash values must also be valid to add the trusted application. In addition, to minimize the gaps in visibility to the Security solution, be as specific as possible in your entries. For example, combineSignatureinformation with knownPaths. -
Operator: Defaults tois("equal to"). This cannot be changed. -
Value: Enter the hash value or file path. To add an additional value, click AND. -
Description(Optional): Enter a description for the trusted application.
-
- Click Add trusted application. The application appears in the Trusted applications table.
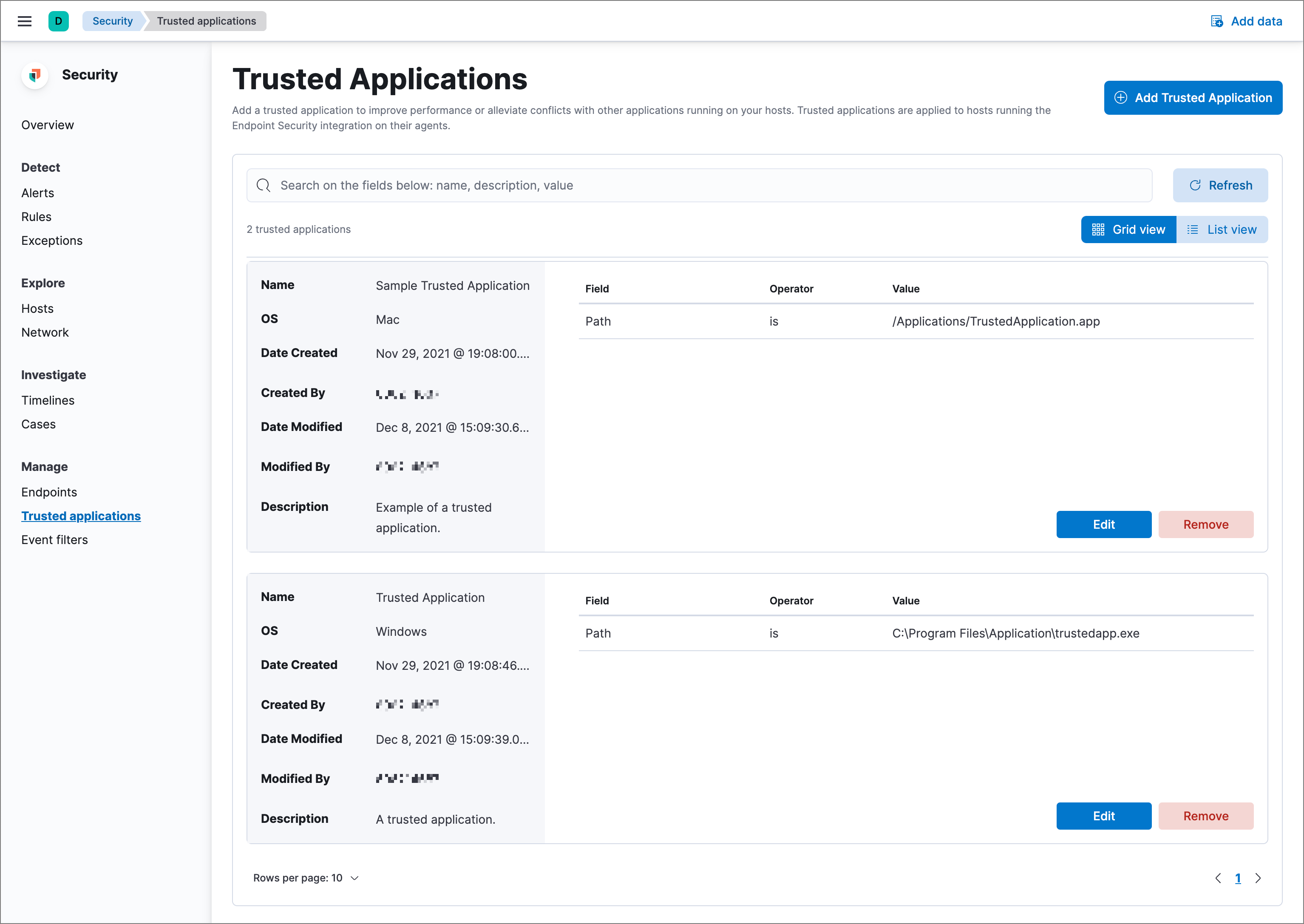
Trusted applications table
editThe Trusted applications table displays all the trusted applications that have been added to the Elastic Security app. By default, applications appear in Grid view — a comprehensive display of all metadata and field values in table format. To view a simplified, condensed version of the table, select List view.
In the list view, click the arrow to expand and collapse details.
Manage trusted applications
editFilter trusted applications
editTo filter trusted applications by specific criteria, enter a simple search in the search bar. You can search the following attributes:
-
name -
description -
value
Remove a trusted application
edit-
Find the application you want to remove. Click Remove if you’re in the grid view or the Remove this entry icon if you’re in the list view.
- On the dialog that appears, verify that you are removing the correct application, then click Remove trusted application. A message confirming the application was removed displays.