Tutorial: Use role-based access control to customize Kibana spaces
editTutorial: Use role-based access control to customize Kibana spaces
editWith role-based access control (RBAC), you can provide users access to data, tools, and Kibana spaces. In this tutorial, you will learn how to configure roles that provide the right users with the right access to the data, tools, and Kibana spaces.
Scenario
editOur user is a web developer working on a bank’s online mortgage service. The web developer has these three requirements:
- Have access to the data for that service
- Build visualizations and dashboards
- Monitor the performance of the system
You’ll provide the web developer with the access and privileges to get the job done.
Prerequisites
editTo complete this tutorial, you’ll need the following:
-
Administrative privileges: You must have a role that grants privileges to create a space, role, and user. This is any role which grants the
manage_securitycluster privilege. By default, thesuperuserrole provides this access. See the built-in roles. -
A space: In this tutorial, use
Dev Mortgageas the space name. See spaces management for details on creating a space. - Data: You can use sample data or live data. In the following steps, Filebeat and Metricbeat data are used.
Steps
editWith the requirements in mind, here are the steps that you will work through in this tutorial:
-
Create a role named
mortgage-developer - Give the role permission to access the data in the relevant indices
- Give the role permission to create visualizations and dashboards
- Create the web developer’s user account with the proper roles
Create a role
editOpen the menu, then go to Stack Management > Security > Roles for an overview of your roles. This view provides actions for you to create, edit, and delete roles.
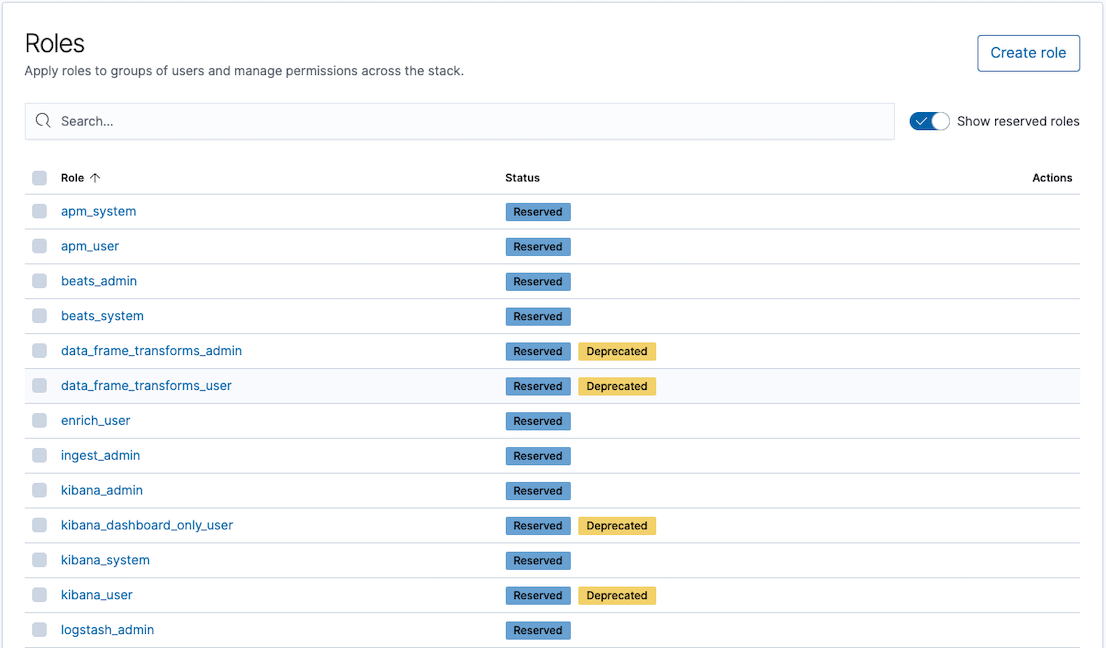
You can create as many roles as you like. Click Create role and
provide a name. Use dev-mortgage because this role is for a developer
working on the bank’s mortgage application.
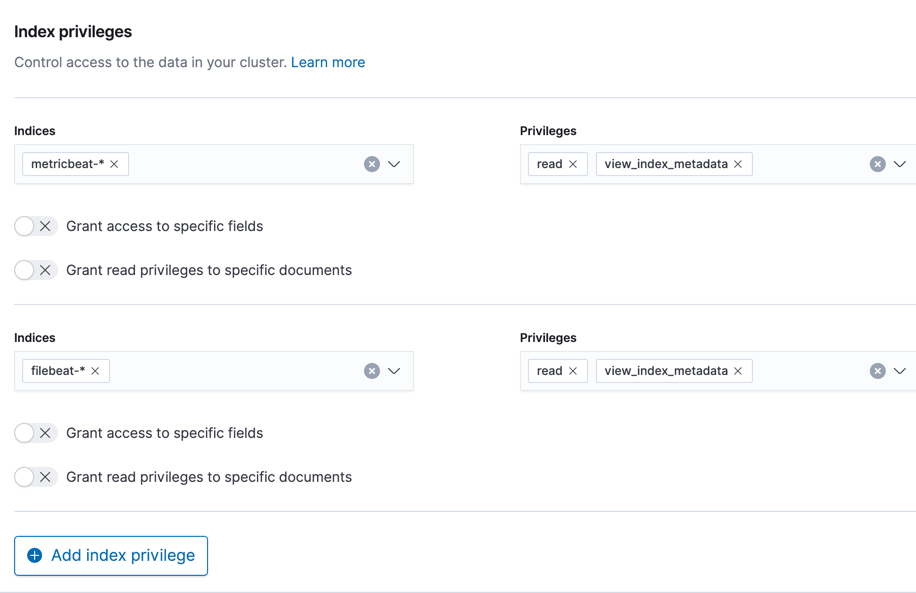
Give the role permission to access the data
editAccess to data in indices is an index-level privilege, so in
Index privileges, add lines for the indices that contain the
data for this role. Two privileges are required: read and
view_index_metadata. All privileges are detailed in the
security privileges documentation.
In the screenshots, Filebeat and Metricbeat data is used, but you should use the index patterns for your indices.
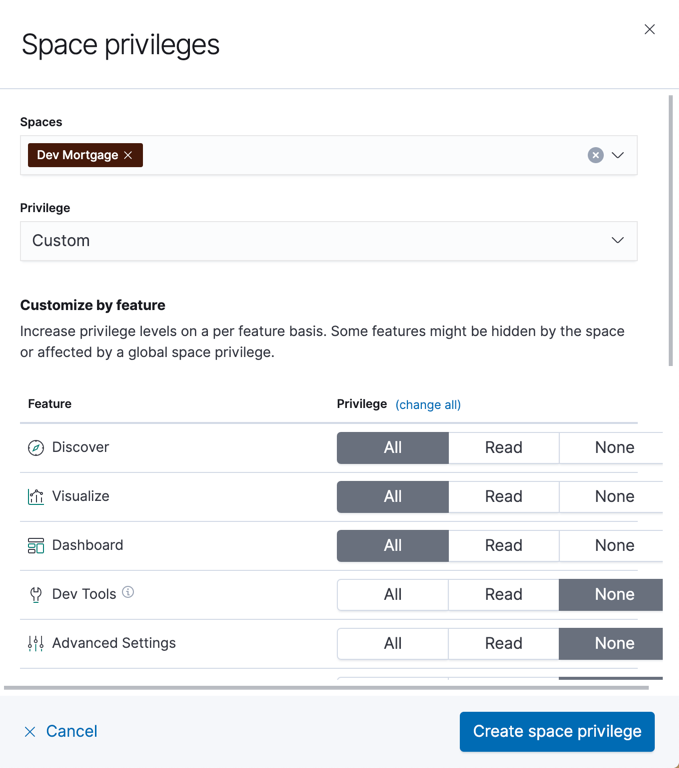
Give the role permission to create visualizations and dashboards
editBy default, roles do not give Kibana privileges. Click Add space
privilege and associate this role with the Dev Mortgage space.
To enable users with the dev-mortgage role to create visualizations
and dashboards, click All for Visualize and Dashboard. Also
assign All for Discover because it is common for developers
to create saved searches while designing visualizations.
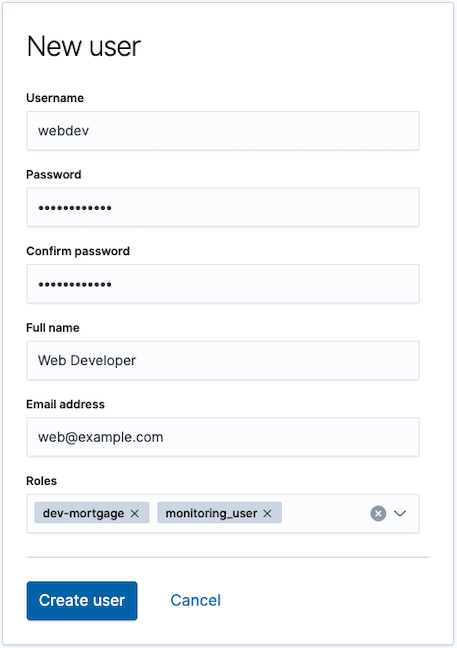
Create the developer user account with the proper roles
edit- Open the menu, then go to Stack Management > Security > Users.
-
Click Create user, then give the user the
dev-mortgageandmonitoring-userroles, which are required for Stack Monitoring users.
Finally, have the developer log in and access the Dev Mortgage space and create a new visualization.
If the user is assigned to only one space, they will automatically enter that space on login.