Create an index pattern
editCreate an index pattern
editKibana requires an index pattern to access the Elasticsearch data that you want to explore. An index pattern selects the data to use and allows you to define properties of the fields.
An index pattern can point to one or more indices, data stream, or index aliases. For example, an index pattern can point to your log data from yesterday, or all indices that contain your data.
Required permissions
edit-
Access to Index Patterns requires the Kibana privilege
Index Pattern Management. -
To create an index pattern, you must have the Elasticsearch privilege
view_index_metadata. - If a read-only indicator appears in Kibana, you have insufficient privileges to create or save index patterns. The buttons to create new index patterns or save existing index patterns are not visible. For more information, refer to Granting access to Kibana.
Create an index pattern
editIf you collected data using one of the Kibana ingest options, uploaded a file, or added sample data, you get an index pattern for free, and can start exploring your data. If you loaded your own data, follow these steps to create an index pattern.
- Open the main menu, then click to Stack Management > Index Patterns.
-
Click Create index pattern.
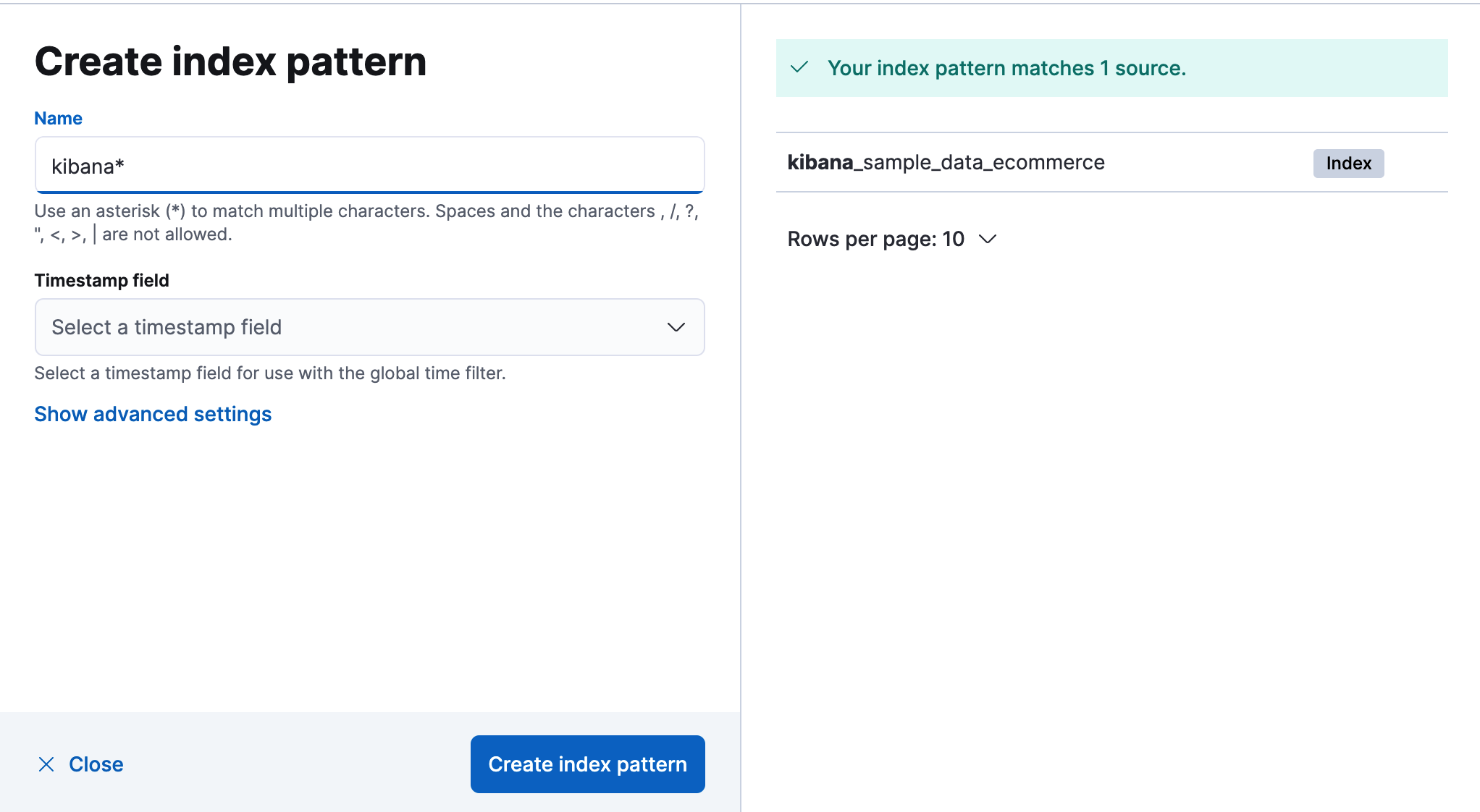
-
Start typing in the Index pattern field, and Kibana looks for the names of indices, data streams, and aliases that match your input.
-
To match multiple sources, use a wildcard (*). For example,
filebeat-*matchesfilebeat-apache-a,filebeat-apache-b, and so on. -
To match multiple single sources, enter their names,
separated with a comma. Do not include a space after the comma.
filebeat-a,filebeat-bmatches two indices, but not matchfilebeat-c. -
To exclude a source, use a minus sign (-), for example,
-test3.
-
To match multiple sources, use a wildcard (*). For example,
-
If Kibana detects an index with a timestamp, expand the Timestamp field menu, and then select the default field for filtering your data by time.
- If your index doesn’t have time-based data, choose I don’t want to use the time filter.
- If you don’t set a default time field, you can’t use global time filters on your dashboards. This is useful if you have multiple time fields and want to create dashboards that combine visualizations based on different timestamps.
-
Click Create index pattern.
Kibana is now configured to use your Elasticsearch data. When a new field is added to an index, the index pattern field list is updated the next time the index pattern is loaded, for example, when you load the page or move between Kibana apps.
- Select this index pattern when you search and visualize your data.
Create an index pattern for rolled up data
editAn index pattern can match one rollup index. For a combination rollup index pattern with both raw and rolled up data, use the standard notation:
rollup_logstash,kibana_sample_data_logs
For an example, refer to Create and visualize rolled up data.
Create an index pattern that searches across clusters
editIf your Elasticsearch clusters are configured for cross-cluster search, you can create an index pattern to search across the clusters of your choosing. Use the same syntax that you use in a raw cross-cluster search request in Elasticsearch:
<cluster-names>:<pattern>
To query Logstash indices across two Elasticsearch clusters
that you set up for cross-cluster search, named cluster_one and cluster_two:
cluster_one:logstash-*,cluster_two:logstash-*
Use wildcards in your cluster names
to match any number of clusters. To search Logstash indices across
clusters named cluster_foo, cluster_bar, and so on:
cluster_*:logstash-*
To query across all Elasticsearch clusters that have been configured for cross-cluster search, use a standalone wildcard for your cluster name:
*:logstash-*
To match indices starting with logstash-, but exclude those starting with logstash-old, from
all clusters having a name starting with cluster_:
`cluster_*:logstash-*,cluster_*:-logstash-old*`
To exclude a cluster having a name starting with cluster_:
`cluster_*:logstash-*,cluster_one:-*`
Once you configure an index pattern to use the cross-cluster search syntax, all searches and aggregations using that index pattern in Kibana take advantage of cross-cluster search.
Delete index patterns
editWhen you delete an index pattern, you cannot recover the associated field formatters, runtime fields, source filters, and field popularity data. Deleting an index pattern does not remove any indices or data documents from Elasticsearch.
Deleting an index pattern breaks all visualizations, saved searches, and other saved objects that reference the index pattern.
- Open the main menu, then click Stack Management > Index Patterns.
- Click the index pattern to delete.
-
Delete (
 ) the index pattern.
) the index pattern.