IMPORTANT: No additional bug fixes or documentation updates
will be released for this version. For the latest information, see the
current release documentation.
MISP module
edit
IMPORTANT: This documentation is no longer updated. Refer to Elastic's version policy and the latest documentation.
MISP module
editThis functionality is in beta and is subject to change. The design and code is less mature than official GA features and is being provided as-is with no warranties. Beta features are not subject to the support SLA of official GA features.
This is a filebeat module for reading threat intel information from the MISP platform (https://www.circl.lu/doc/misp/). It uses the httpjson input to access the MISP REST API interface.
The configuration in the config.yml file uses the following format:
- var.api_key: specifies the API key to access MISP.
-
var.http_request_body: an object containing any parameter that needs to be sent to the search API. Default:
limit: 1000 - var.url: URL of the MISP REST API, e.g., "http://x.x.x.x/attributes/restSearch"
Read the quick start to learn how to configure and run modules.
Example dashboard
editThis module comes with a sample dashboard. For example:
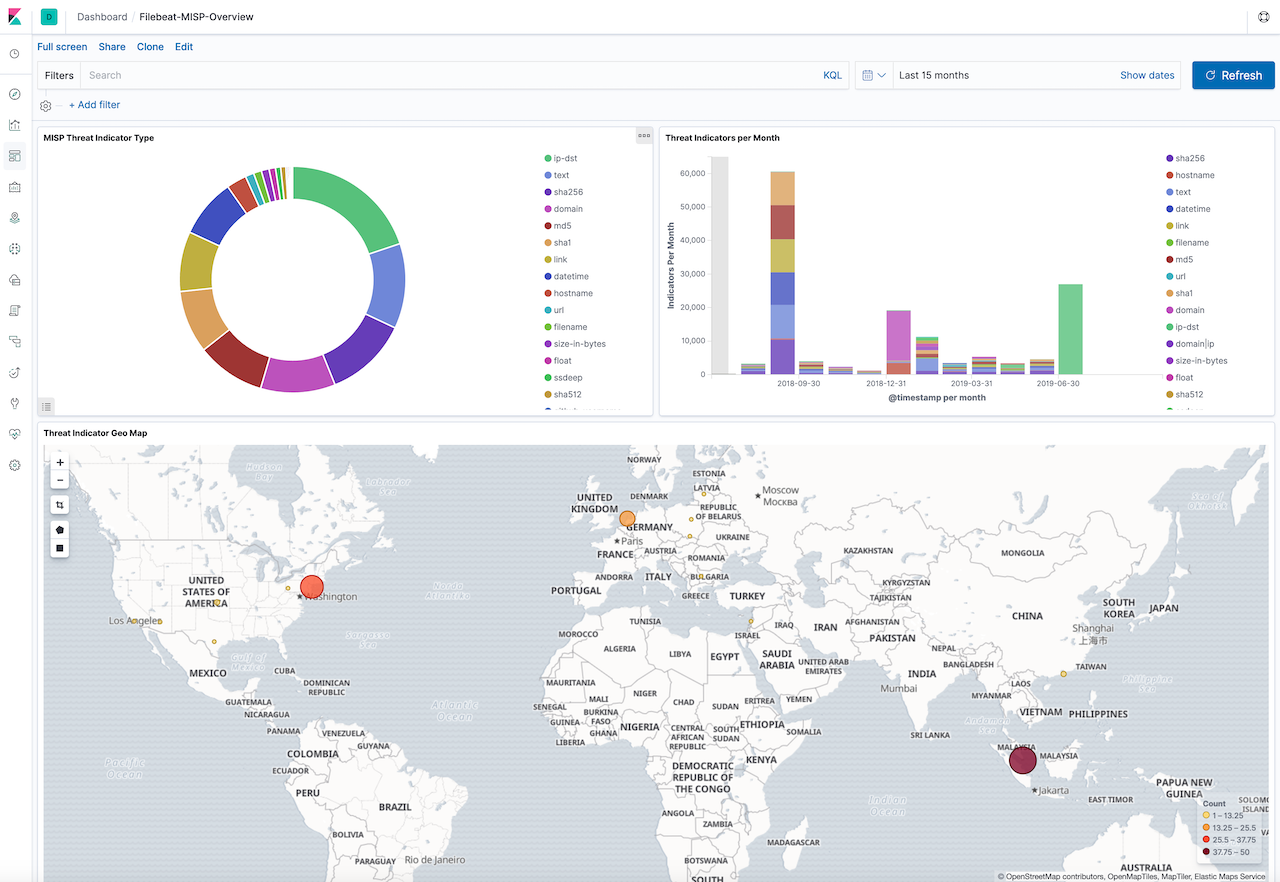
Fields
editFor a description of each field in the module, see the exported fields section.