How does Elastic Security drive value to your organization?
Elastic Security is used by more than 50% of Fortune 500 companies, minimizes TCO, and delivers a modern approach to detection, investigation, and response to increase security team efficiency. For organizations looking to strengthen defenses by getting access to real-time insights, Elastic Security, built on a Search AI Platform, offers visibility across the entire attack surface to help you meet your business objectives.
How Elastic leverages Elastic Security
Before explaining the value drivers, let's hear from our Elastic CISO Mandy Andress. Mandy compares her viewpoint and experiences consolidating tech stacks for a Fortune 100 firm and Elastic with an 87.5% faster time-to-market.
Video transcript:
Hi, all. I'm Mandy, Elastic’s CISO. Before I compare the above outcomes, let me first share my perspective for context. Fundamentally, I see security as a data problem, and I'm often asked, what keeps you up at night? I always give the same answer: what do I not know? There are so many things changing and happening in the global threat environments and our overall environment that I'm always concerned about what we are missing. What actions should we be taking that we don't have the visibility or are just not looking at with the correct perspective? With that in mind, I try to build a diverse team that brings different skills and different perspectives and stays really connected with the community.
But there will always be things that we don't know. And how do we learn that? How do we apply Elastic and the power of the ELK stack to provide us that visibility? Elastic helps our organization uncover some of those unknown unknowns with data. There are so many great stories I can tell you about how Elastic enables organizations to do that. But fundamentally, it's a mindset shift. How do you transition from focusing on discrete activities that you don't want to see happening in your environment to really understanding the baseline of how your environment should be behaving and what anomalous activities are occurring that you should investigate? With today's scale and overall significant amounts of data. Elastic provides the ability to quickly process significant amounts of data at scale. That speed, combined with our machine learning and generative AI capabilities, means we don't have to do it the same way. When you replace the tech stack for your SOC. These combined capabilities are some of the most powerful I have seen and some of the easiest to configure just out of the box, turning on machine learning rules. We gain significantly more insight than organizations can achieve with the traditional SIEM. We're all awaiting the addition of Elastic Security Assistant that utilizes generative AI to shorten the learning curve of analysts.
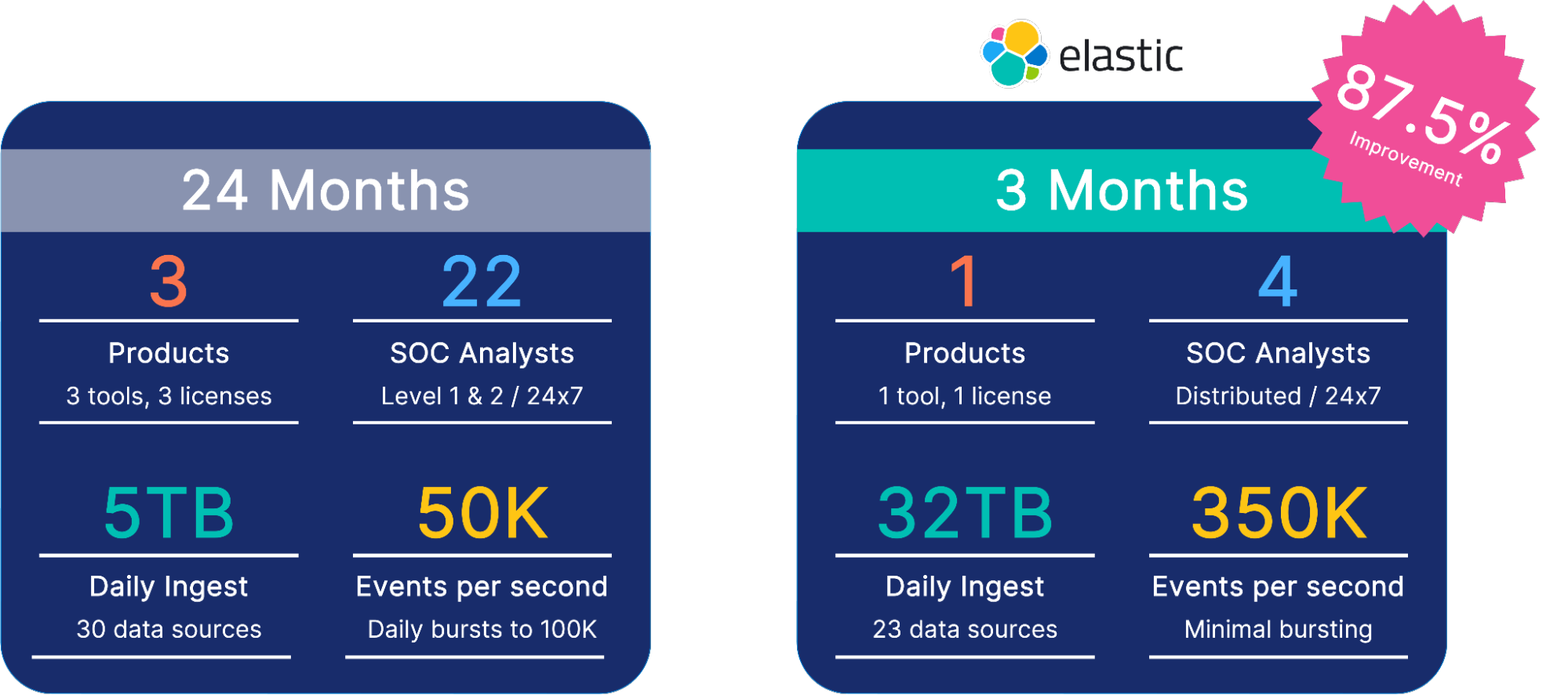
Before Elastic, I was working at a Fortune 100 firm. We wanted to completely rebuild our SOC and expand to provide global 24x7 support. We were ingesting daily about five terabytes of data with 50,000 events per second. Additionally, we had daily bursts, occasionally reaching 100,000 events per second. We knew we wanted detection and analysis with some behavioral analytics. We wanted to start moving into anomalous behavior. Understanding what was suspicious about our environment, whether it was a user or a machine. Getting all of that stood up took us three tools, 24 months, millions of dollars in licenses, and even millions of dollars more in services. And after 24 months, we were functional, but we still had a lot of work to do to get us to our desired end state.
When I started at Elastic, I was looking to achieve the same thing, and we were able to do that with one product and one license, Elastic. We’re known to Elasticians as customer zero. We start testing and consuming capabilities as soon as possible. In that first three months, we were ingesting about 32 terabytes of data daily, 350,000 events per second. And we only had four SOC analysts distributed across the globe. From an information security perspective, we were up and running in three months versus 24. Not to mention that our current architecture is ingesting daily 200 terabytes of data, but this story doesn't tell us the rest of the power across the environment. Utilizing cross-cluster search on petabytes of data across multi-cloud and on-prem environments, searching many, many petabytes of data in just under 30 seconds.
This provides insights allowing us to respond to real-time events like Log4j and helps us provide data analysis to answer some of those questions to help ensure that we're knowing what's happening in our environment and identifying, as best we can, those unknown unknowns. With elastic security, we've seen clear productivity gains, risk reductions, and cost savings, and we look forward to continuing on this journey to improve the security of elastic. I encourage you to evaluate the gains your organization can achieve using elastic. Thank you.Video transcript:
Hi, all. I'm Mandy, Elastic’s CISO. Before I compare the above outcomes, let me first share my perspective for context. Fundamentally, I see security as a data problem, and I'm often asked, what keeps you up at night? I always give the same answer: what do I not know? There are so many things changing and happening in the global threat environments and our overall environment that I'm always concerned about what we are missing. What actions should we be taking that we don't have the visibility or are just not looking at with the correct perspective? With that in mind, I try to build a diverse team that brings different skills and different perspectives and stays really connected with the community.
But there will always be things that we don't know. And how do we learn that? How do we apply Elastic and the power of the ELK stack to provide us that visibility? Elastic helps our organization uncover some of those unknown unknowns with data. There are so many great stories I can tell you about how Elastic enables organizations to do that. But fundamentally, it's a mindset shift. How do you transition from focusing on discrete activities that you don't want to see happening in your environment to really understanding the baseline of how your environment should be behaving and what anomalous activities are occurring that you should investigate? With today's scale and overall significant amounts of data. Elastic provides the ability to quickly process significant amounts of data at scale. That speed, combined with our machine learning and generative AI capabilities, means we don't have to do it the same way. When you replace the tech stack for your SOC. These combined capabilities are some of the most powerful I have seen and some of the easiest to configure just out of the box, turning on machine learning rules. We gain significantly more insight than organizations can achieve with the traditional SIEM. We're all awaiting the addition of Elastic Security Assistant that utilizes generative AI to shorten the learning curve of analysts.
Before Elastic, I was working at a Fortune 100 firm. We wanted to completely rebuild our SOC and expand to provide global 24x7 support. We were ingesting daily about five terabytes of data with 50,000 events per second. Additionally, we had daily bursts, occasionally reaching 100,000 events per second. We knew we wanted detection and analysis with some behavioral analytics. We wanted to start moving into anomalous behavior. Understanding what was suspicious about our environment, whether it was a user or a machine. Getting all of that stood up took us three tools, 24 months, millions of dollars in licenses, and even millions of dollars more in services. And after 24 months, we were functional, but we still had a lot of work to do to get us to our desired end state.
When I started at Elastic, I was looking to achieve the same thing, and we were able to do that with one product and one license, Elastic. We’re known to Elasticians as customer zero. We start testing and consuming capabilities as soon as possible. In that first three months, we were ingesting about 32 terabytes of data daily, 350,000 events per second. And we only had four SOC analysts distributed across the globe. From an information security perspective, we were up and running in three months versus 24. Not to mention that our current architecture is ingesting daily 200 terabytes of data, but this story doesn't tell us the rest of the power across the environment. Utilizing cross-cluster search on petabytes of data across multi-cloud and on-prem environments, searching many, many petabytes of data in just under 30 seconds.
This provides insights allowing us to respond to real-time events like Log4j and helps us provide data analysis to answer some of those questions to help ensure that we're knowing what's happening in our environment and identifying, as best we can, those unknown unknowns. With elastic security, we've seen clear productivity gains, risk reductions, and cost savings, and we look forward to continuing on this journey to improve the security of elastic. I encourage you to evaluate the gains your organization can achieve using elastic. Thank you.
Curious to see how your team compares?Try out our interactive value calculator.
Value drivers for security teams
Modern security solutions typically drive values in these four primary areas:
Costs savings: This includes any monetary savings from reducing the total cost of ownership of technology that directly impacts the bottom line.
Risk reduction: Here, we quantify the value of reducing the likelihood and severity of security incidents with Elastic. Elastic looks to identify potential risks before they occur, allowing your organization to uncover any additional financial benefits that allow you to retain losses.
Productivity gains: Elastic boosts productivity by accelerating analysis, facilitating collaboration, and automating key steps. These gains improve efficiency, accelerate decision-making, and allow organizations to redistribute resources to new projects.
- Revenue recovery: Service downtime and customer experience issues can impact revenue and customer retention. This area reflects the bottom-line value of reducing these risks.
Value drivers of Elastic Security
For Elastic Security specifically, we define value in the following categories:
1. Security team efficiency improvement
- Elastic Security drives productivity gains across security analysts, engineers, and management personnel from a business analysis perspective. We begin by accounting for the economic value of improving the productivity of every SOC’s most valuable resource: its skilled practitioners. If time is money, how much can your team expect to save by automating threat detection and streamlining investigation and incident response?
- By centralizing data, security teams can analyze information faster and accelerate response with embedded case management and automated actions. This allows teams to quickly determine root cause and reduce escalations. By improving mean time to investigate, detect, and respond (MTTX) and reducing false-positive alerts and escalations, teams can reduce their overall cost per incident.
2. Security technology consolidation and optimization
- Elastic Security unifies several vital technologies — SIEM, endpoint, and cloud security — on a single platform. In this calculation, we estimate the value of lowering licensing and infrastructure costs, reducing technical overhead, and simplifying the implementation of new use cases.
3. Business disruption risk reduction
- Any disruption to your business by security incidents — whether internal or external — can cost your organization. Elastic Security allows you to improve visibility, eliminate blind spots, increase automation, and reduce the number of incidents. In this calculation, we consider downtime associated with internal and customer-facing services and applications. This can bring productivity gains for employees and recover revenue previously lost to downtime, SLA violations, and customer churn.
4. Incident risk reduction
- With robust endpoint security solutions and capabilities, Elastic Security prevents and detects ransomware, malware, phishing, and other attacks, and enables automated response environment-wide. Here, we measure the impact of reducing these risks and measure potential financial savings based on IBM’s Cost of a Data Breach Report.
5. Incident cost avoidance
- Elastic Security modernizes SecOps, equipping practitioners to protect, detect, and respond to complex attacks. With an open and transparent platform — and an agent that stops ransomware and advanced threats alike — it helps organizations reduce risk, advance SecOps maturity, and harden DevSecOps processes. Here we take into account post-incident cost savings, including system reimaging and hours spent by an external incident response firm.
Elastic AI Assistant
These calculations don’t reflect the value delivered in the recently introduced Elastic AI Assistant for Elastic Security. AI helps practitioners harness the rapidly shifting LLM landscape to address various security use cases. It provides guidance on topics as varied as alert summarization, triage steps, query conversion, and custom data ingestion. These capabilities streamline analyst workflows, reducing mean time to investigate, detect, and respond.
How does Elastic Security drive value for our customers?
See how Proficio turned to Elastic Security and used Elastic AI Assistant to reduce investigation time by 34% and project cost savings.